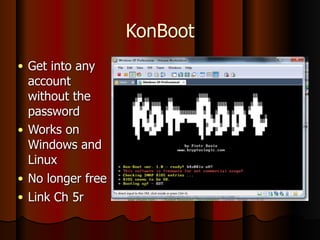
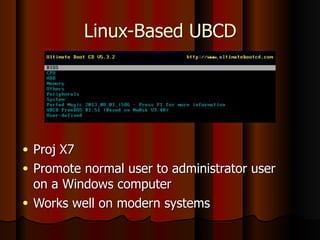
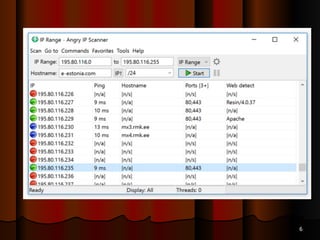
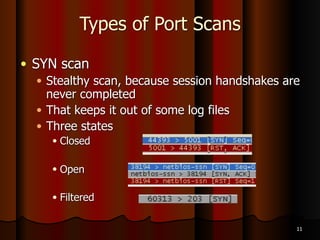
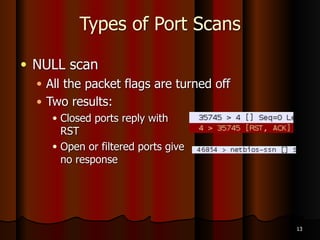
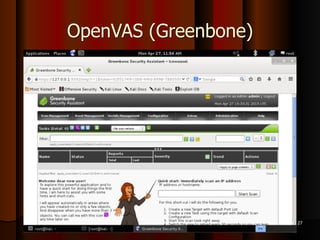
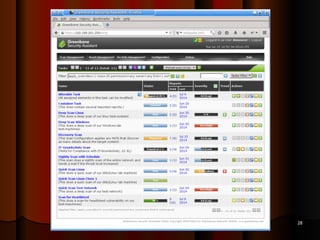
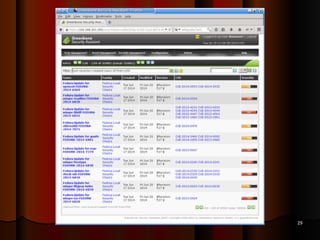
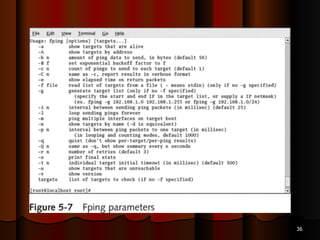
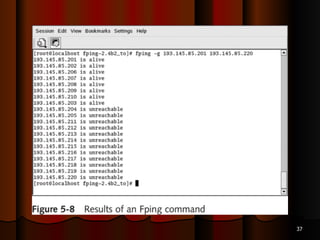
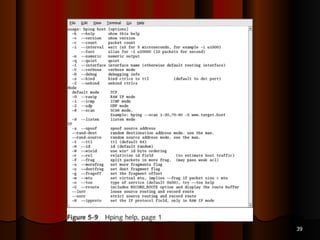
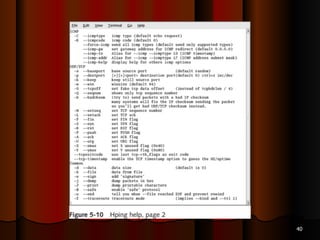
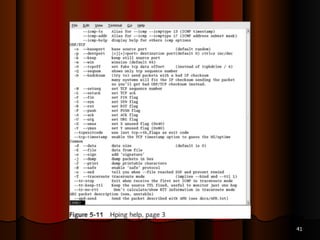
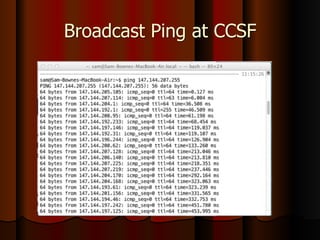
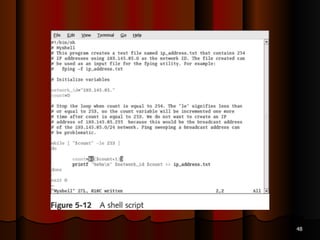
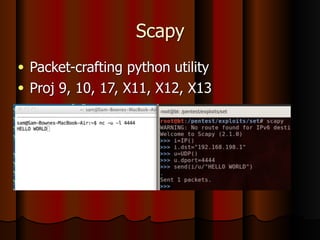
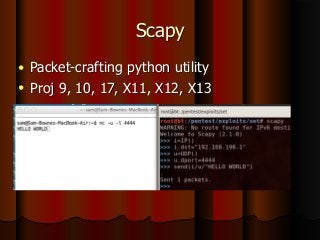
Chapter 5 of the document discusses port scanning, including its objectives, legal implications, different types of scans, and tools for conducting these scans such as Nmap and Nessus. It details methods for identifying active hosts, vulnerabilities on ports, and the automation of security tasks through shell scripting. The chapter emphasizes the importance of understanding the various scanning techniques and their impact on network security.