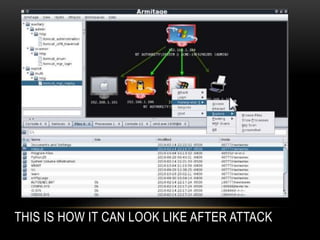
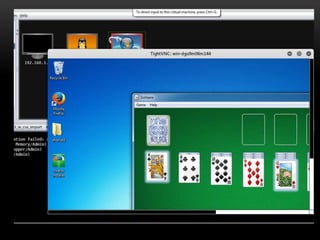
The document provides an overview of the Metasploit Framework, an open-source exploitation tool used for penetration testing and research. It covers its history, architecture, basic terminologies like vulnerabilities, exploits, and payloads, and includes practical demonstrations of using Metasploit for various attacks. The document also emphasizes prevention measures against such attacks and encourages questions from the audience.