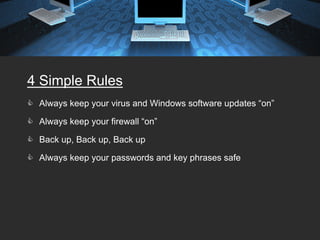
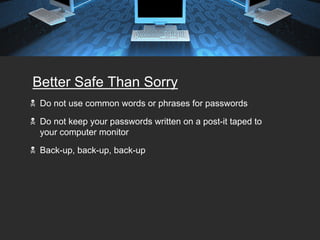
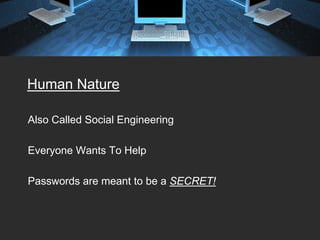
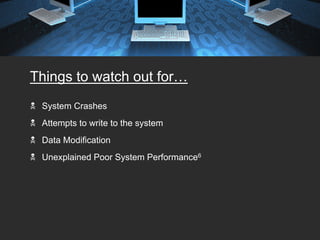
The document provides tips for keeping a network secure, including always keeping virus software and Windows updates enabled, using firewalls, backing up data regularly, and using strong passwords. It warns about common password risks like using obvious words or writing passwords down. The document also covers securing laptops, email, wireless networks, and avoiding risks from open networks. Proper authentication, surge protection, and password protecting are emphasized as important security best practices.












![Works Cited
1. Curtin Matt, Introduction to Network Security, March 1997, page 8.
2. Curtin Matt, Snake Oil Warning Signs: Encryption Software to Avoid
©1996 -1998, page 5.
3. Vermaat, Discovering Computers, Fundamentals, Third Edition, Chapter
10, pages 364, 368, 369, 374.
4. BusinessWeek, “Anatomy of a Spear-Phish,” April 21, 2008, page 38.
5. [Fraser 1997] Ed Fraser, RFC 2196, “Site Security Handbook”,
September 1997.
6. Checking Microsoft Windows® Systems for Signs of Compromise,
Simon Baker, UCL Computer Security Team; Patrick Green, OXCERT
Thomas Meyer, Garaidh Cochrane Version: 1.3.4, 10/28/2005.
7. DEPARTMENT OF DEFENSE, STANDARD DEPARTMENT OF
DEFENSE TRUSTED COMPUTER SYSTEM EVALUATION
CRITERIA, DECEMBER l985 (DOD Orange book),
8. http://en.wikipedia.org/wiki/Network_security#column-one.](https://image.slidesharecdn.com/networksecuritypresentation-12562665172347-phpapp01/85/Network-Security-Presentation-17-320.jpg)