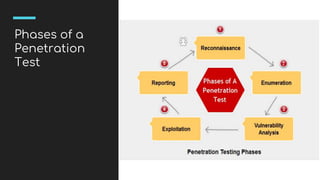
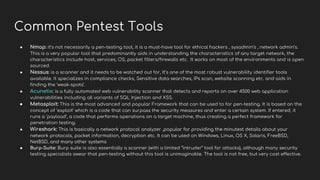
This document provides an overview of penetration testing, describing its purpose, types (black-box and white-box testing), and essential steps involved in the process. It covers common types of cyber attacks and vulnerabilities, as well as tools and techniques used by penetration testers. Additionally, the document outlines the roles, responsibilities, and certifications relevant to the field of penetration testing.