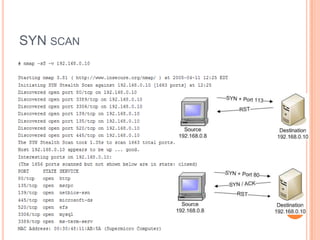
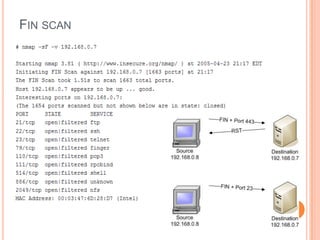
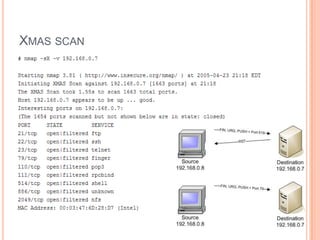
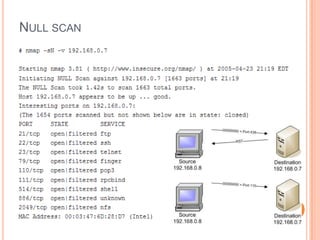
This document summarizes different types of network scans that can be performed using Nmap, including TCP connect scans, SYN scans, FIN scans, Xmas scans, Null scans, and least traffic scans. It also discusses why vulnerability scanning is important and compares the features of the free Nessus Home Feed versus the paid Professional Feed for vulnerability scanning. The Professional Feed provides more frequent plugin updates, policy compliance checks, unlimited PCI audits, operating system audits, and technical support compared to the free Home Feed.