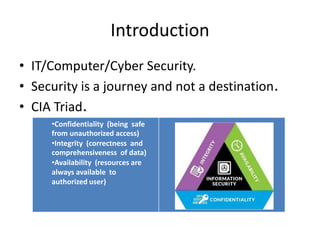
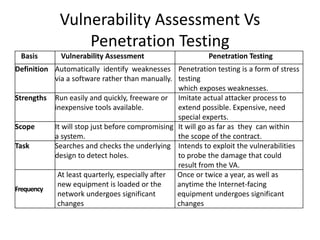
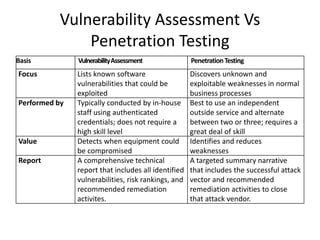
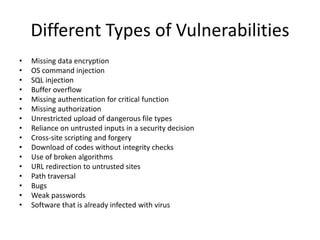
This document discusses vulnerability assessment and penetration testing. It defines them as two types of vulnerability testing that search for known vulnerabilities and attempt to exploit vulnerabilities, respectively. Vulnerability assessment uses automated tools to detect known issues, while penetration testing employs hacking techniques to demonstrate how deeply vulnerabilities could be exploited like an actual attacker. Both are important security practices for identifying weaknesses and reducing risks, but require different skills and have different strengths, weaknesses, frequencies, and report outputs. Reasons for vulnerabilities include insecure coding, limited testing, and misconfigurations. The document outlines common vulnerability and attack types as well as how vulnerability assessment and penetration testing are typically conducted.