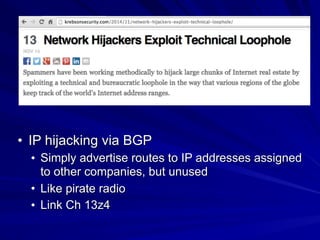
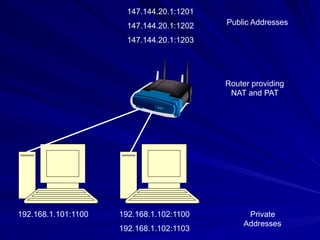
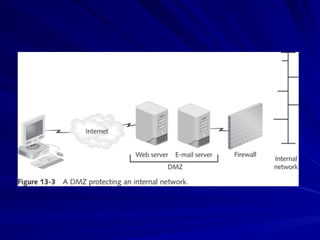
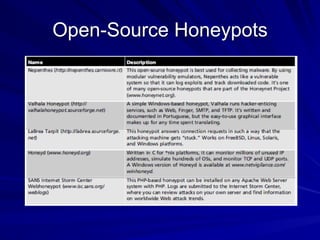
Chapter 13 of the hands-on ethical hacking and network defense guide covers network protection systems, including the roles of routers, firewalls, and intrusion detection systems (IDS). It discusses routing protocols, the function of firewalls, and the importance of monitoring network traffic to prevent unauthorized access and attacks, emphasizing the use of honeypots for trapping hackers. The chapter highlights various technologies and strategies to protect networks effectively against evolving threats.