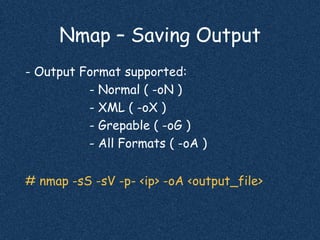
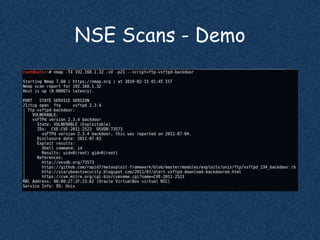
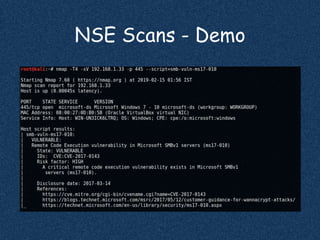
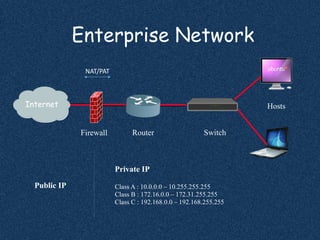
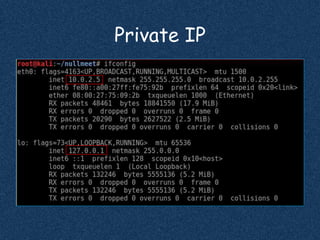
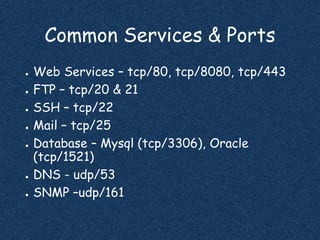
The document discusses using Nmap to perform network scanning and reconnaissance. It provides an overview of Nmap, describing common scan types like TCP and UDP scans. It also covers useful Nmap options for tasks like service and operating system detection. The document demonstrates the Nmap Scripting Engine for tasks like vulnerability scanning and brute force attacks. It provides examples of commands for different scan types and scripts.











![Nmap – Common Scan Types
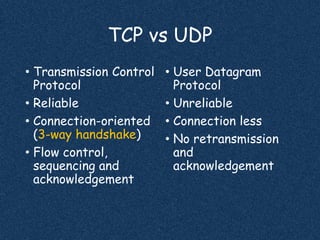
TCP Connect Scan ( -sT )
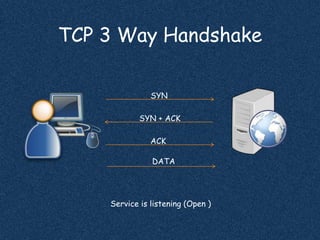
- Complete 3-way handshake
# nmap -sT <target>
TCP SYN Scan ( -sS ) [Default]
- Also known as Half-open scan
# nmap -sS <target>
UDP Scan ( -sU )
- Scan UDP ports, Runs Slow
# nmap -sU <target>](https://image.slidesharecdn.com/reconwithnmap-feb2019-190216172853/85/Recon-with-Nmap-20-320.jpg)