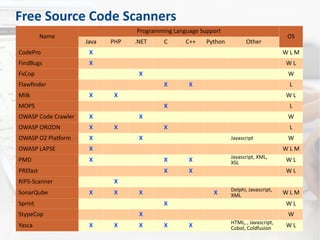
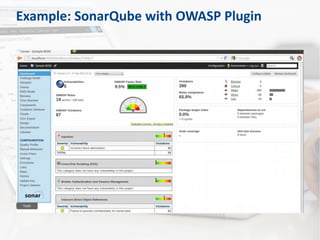
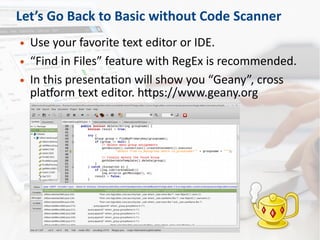
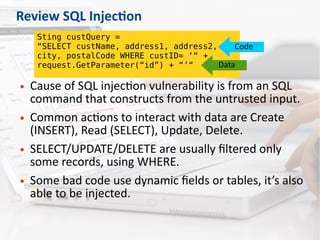
The document discusses secure code review, emphasizing its role in identifying security flaws and ensuring secure development practices in applications. It covers preparation factors, a detailed checklist, and the advantages and limitations of source code scanners. Additionally, the presentation highlights key vulnerabilities like SQL injection, remote code execution, and poor logging practices, stressing the necessity for skilled reviewers and the importance of context in code evaluation.












![Review Session Management
● .Net ASPX web.config
<authentication mode=”Forms”>
<forms loginUrl=”member_login.aspx”
cookieless=”UseCookies”
requireSSL=”true”
path=”/MyApplication” />
</authentication>
● Java web.xml
<session-config>
<cookie-config>
<secure>true</secure>
</cookie-config>
</session-config>
● PHP.ini
session.cookie_lifetime=0
session.use_cookies=On
session.use_only_cookies=On
session.use_strict_mode=On
session.cookie_httponly=On
session.cookie_secure=On
session.gc_maxlifetime=[choose smallest possible]
session.use_trans_sid=Off](https://image.slidesharecdn.com/securecodereview101-161119132006/85/Secure-Code-Review-101-23-320.jpg)

