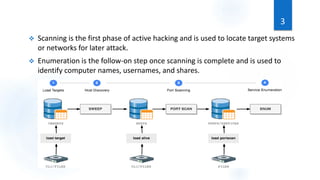
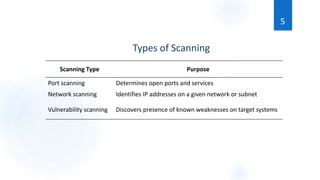
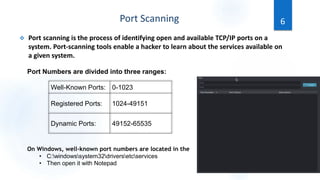
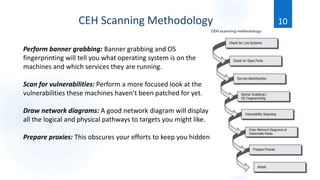
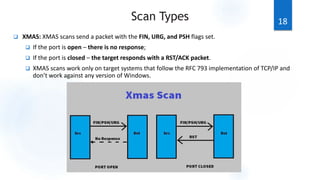
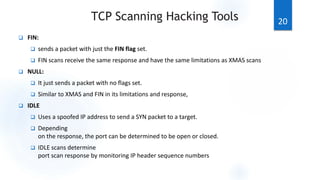
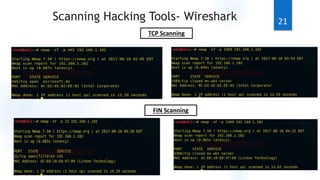
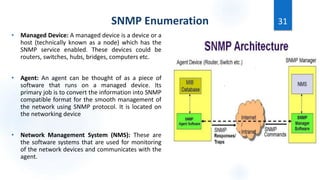
Scanning is the first phase of active hacking used to locate target systems and networks. It involves identifying live hosts, open ports, services, and OS details through techniques like ping sweeps, port scanning, banner grabbing, and vulnerability scanning. Enumeration occurs after scanning and is used to extract additional information like usernames, shares, and services. Specific enumeration techniques discussed include SNMP enumeration, which identifies device information by querying SNMP agents, and NetBIOS enumeration, which extracts Windows account and share details. Hacking tools mentioned that assist with scanning and enumeration include Nmap, SNMPUtil, DumpSec, and Hyena.