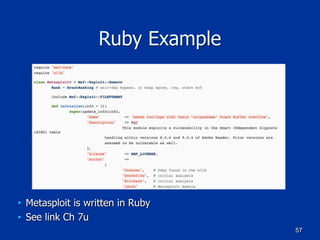
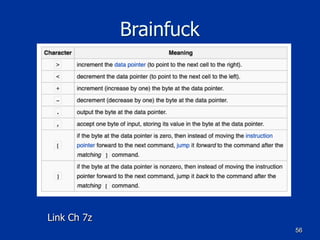
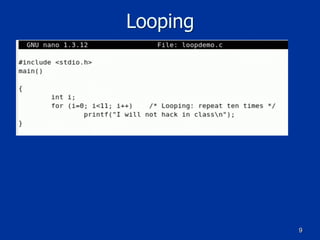
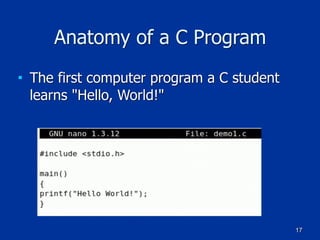
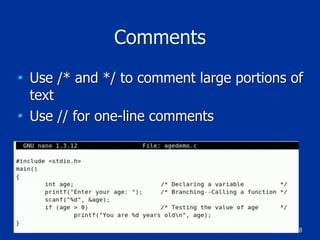
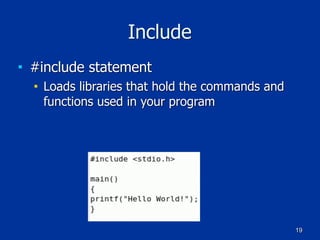
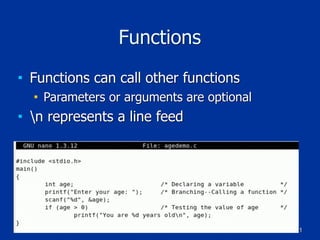
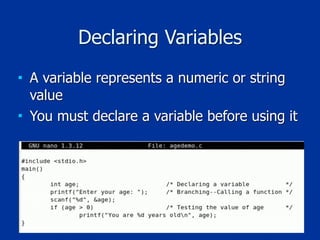
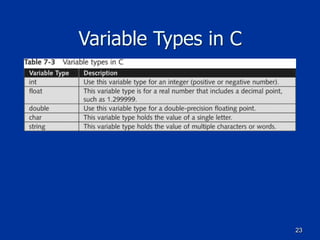
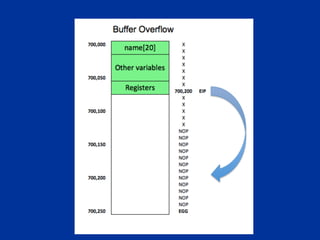
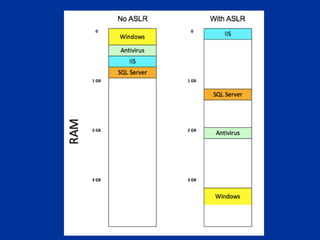
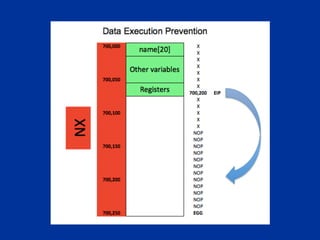
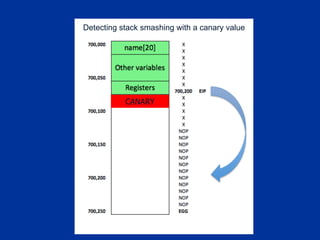
The document covers programming fundamentals for security professionals, focusing on basic programming concepts, C language, HTML, Perl, and object-oriented programming. It emphasizes the importance of debugging, documenting code, and understanding programming rules to avoid errors. Additionally, it introduces concepts like branching, looping, and testing, along with practical exercises for creating simple programs.





















![56
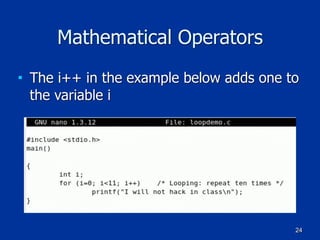
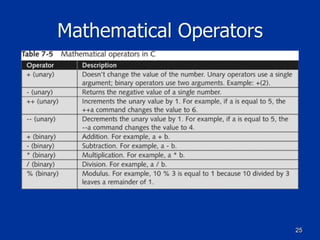
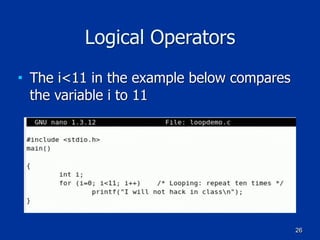
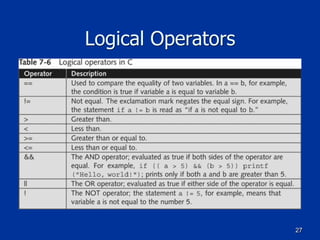
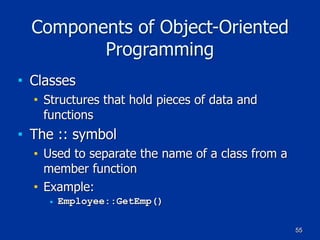
Example of a Class in C++
class Employee
{
public:
char firstname[25];
char lastname[25];
char PlaceOfBirth[30];
[code continues]
};
void GetEmp()
{
// Perform tasks to get employee info
[program code goes here]
}](https://image.slidesharecdn.com/ch07-170112044914/85/Ch-7-Programming-for-Security-Professionals-50-320.jpg)