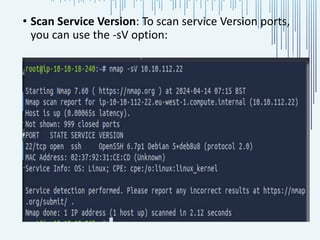
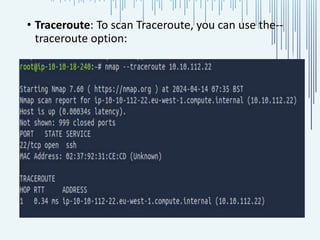
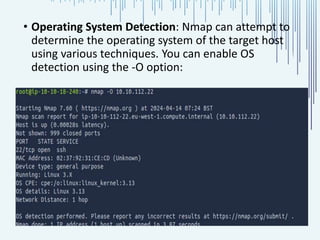
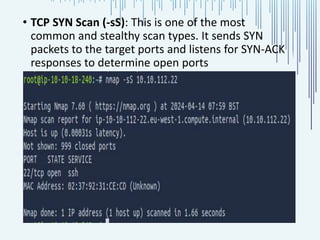
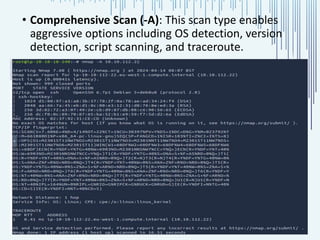
The document discusses the process of port scanning, focusing on identifying open network ports and their potential vulnerabilities using tools like nmap. It outlines the importance of port scanning for network security and various types of scans, detailing specific ports and their functions, benefits, and related threats. The conclusion emphasizes the necessity of understanding these elements to protect web servers from cyber threats.