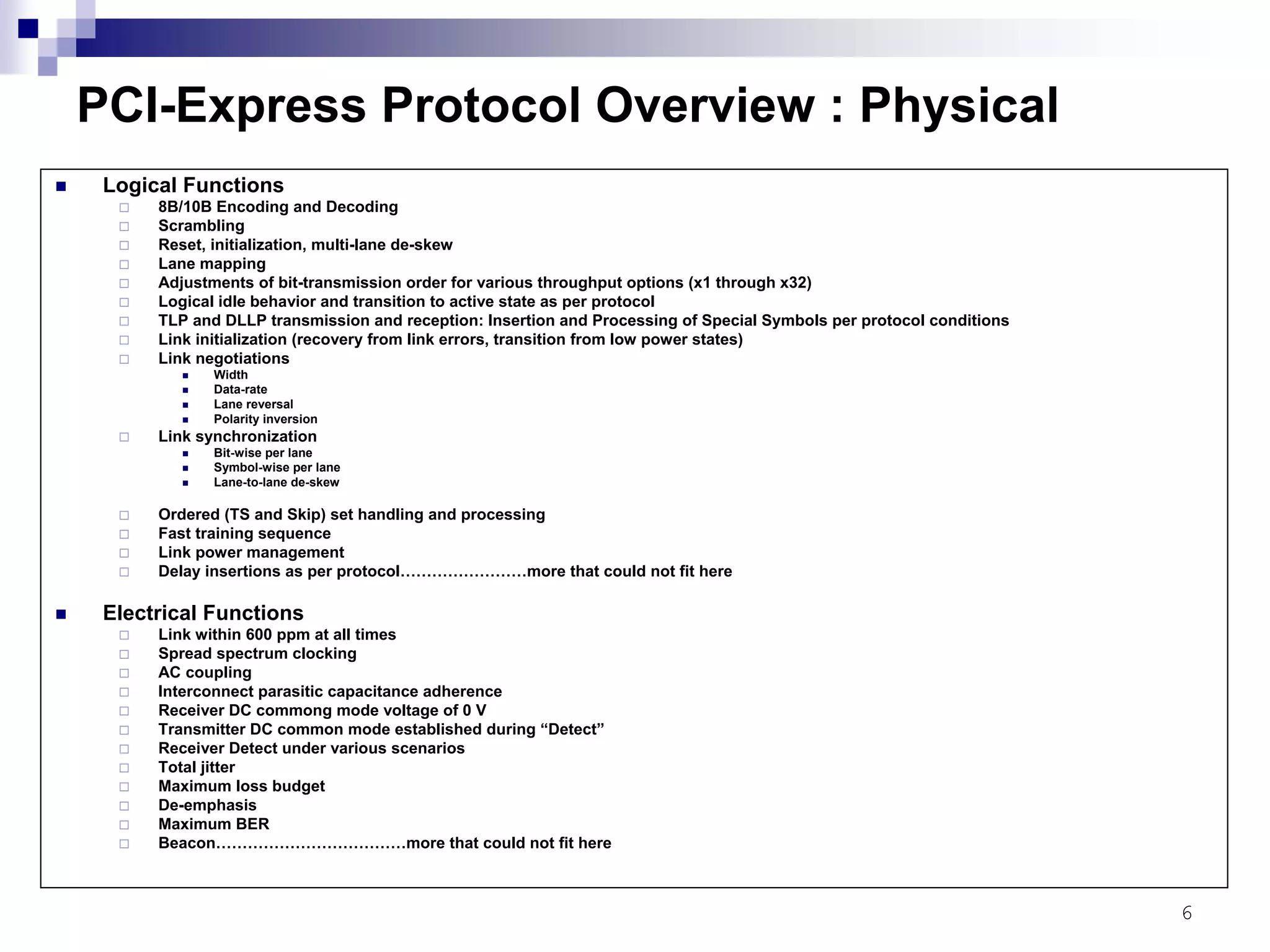
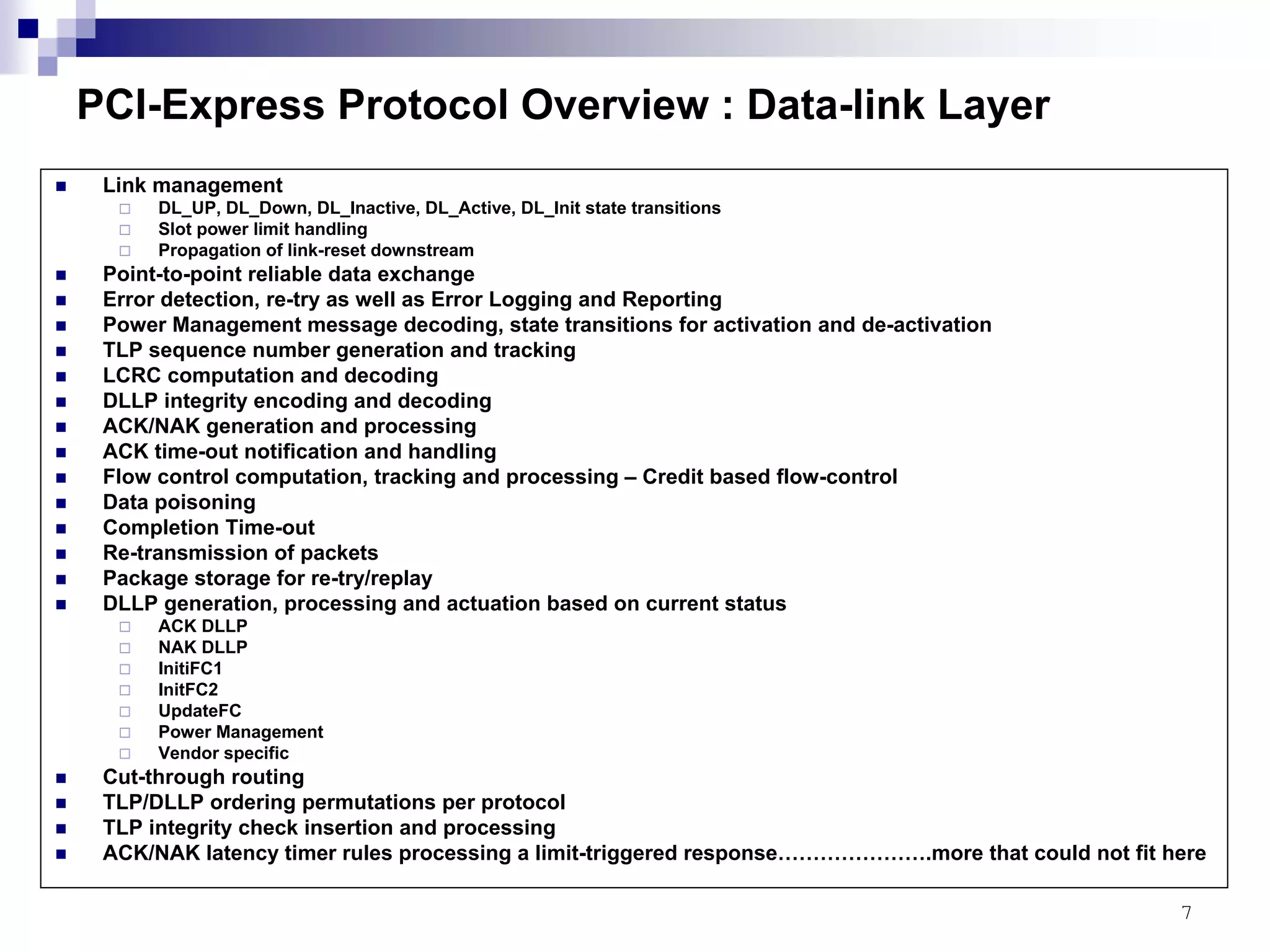
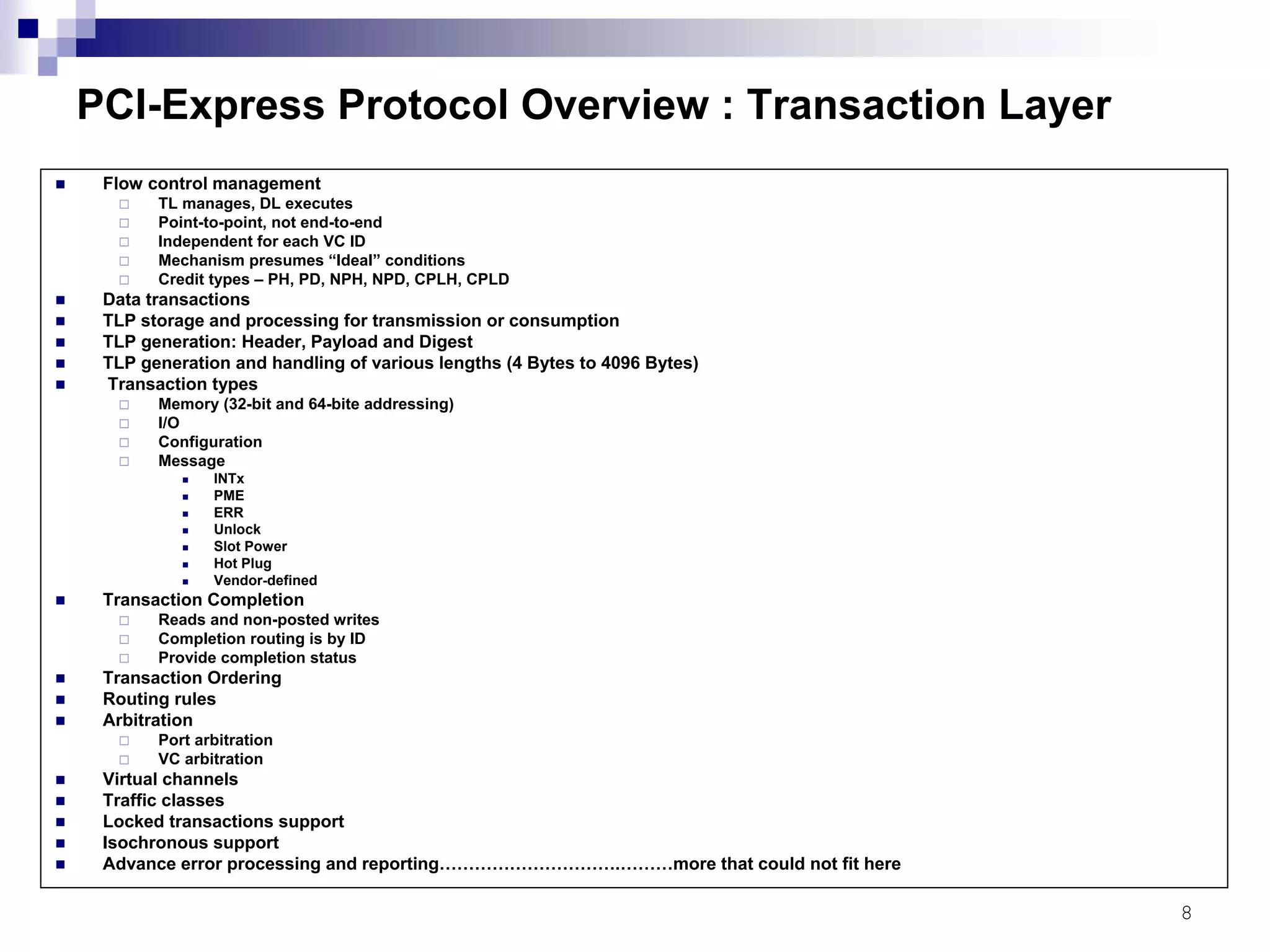
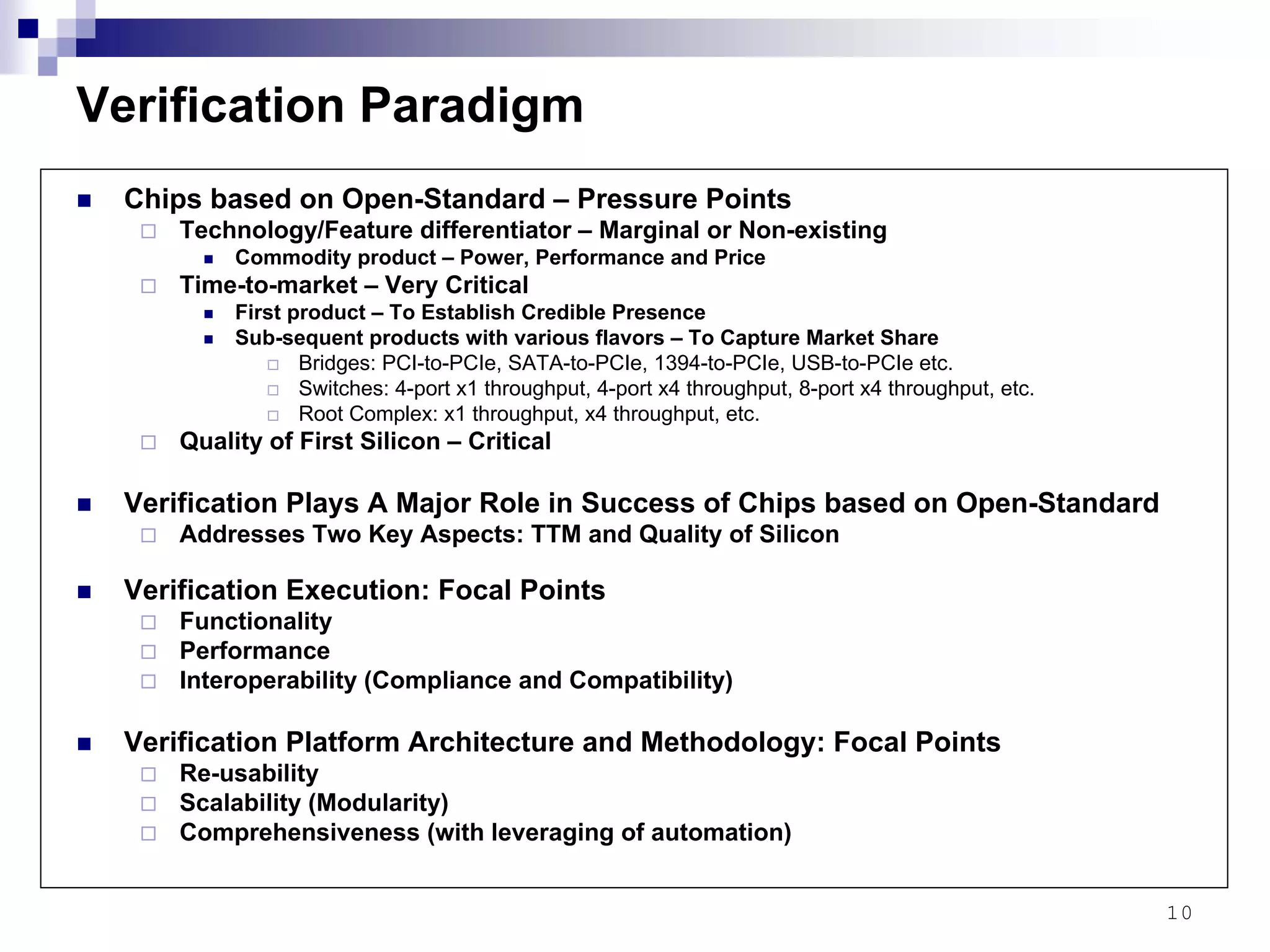
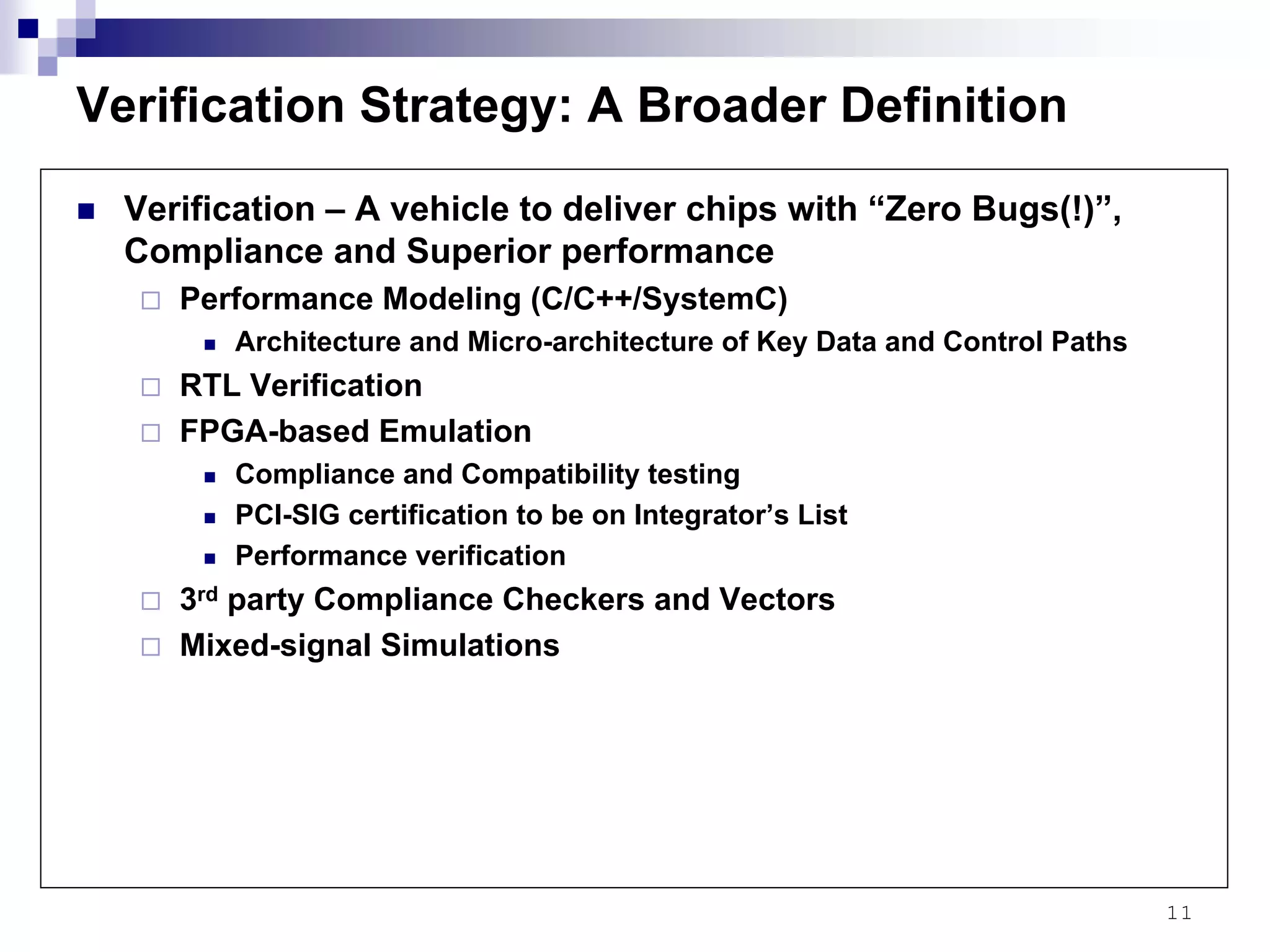
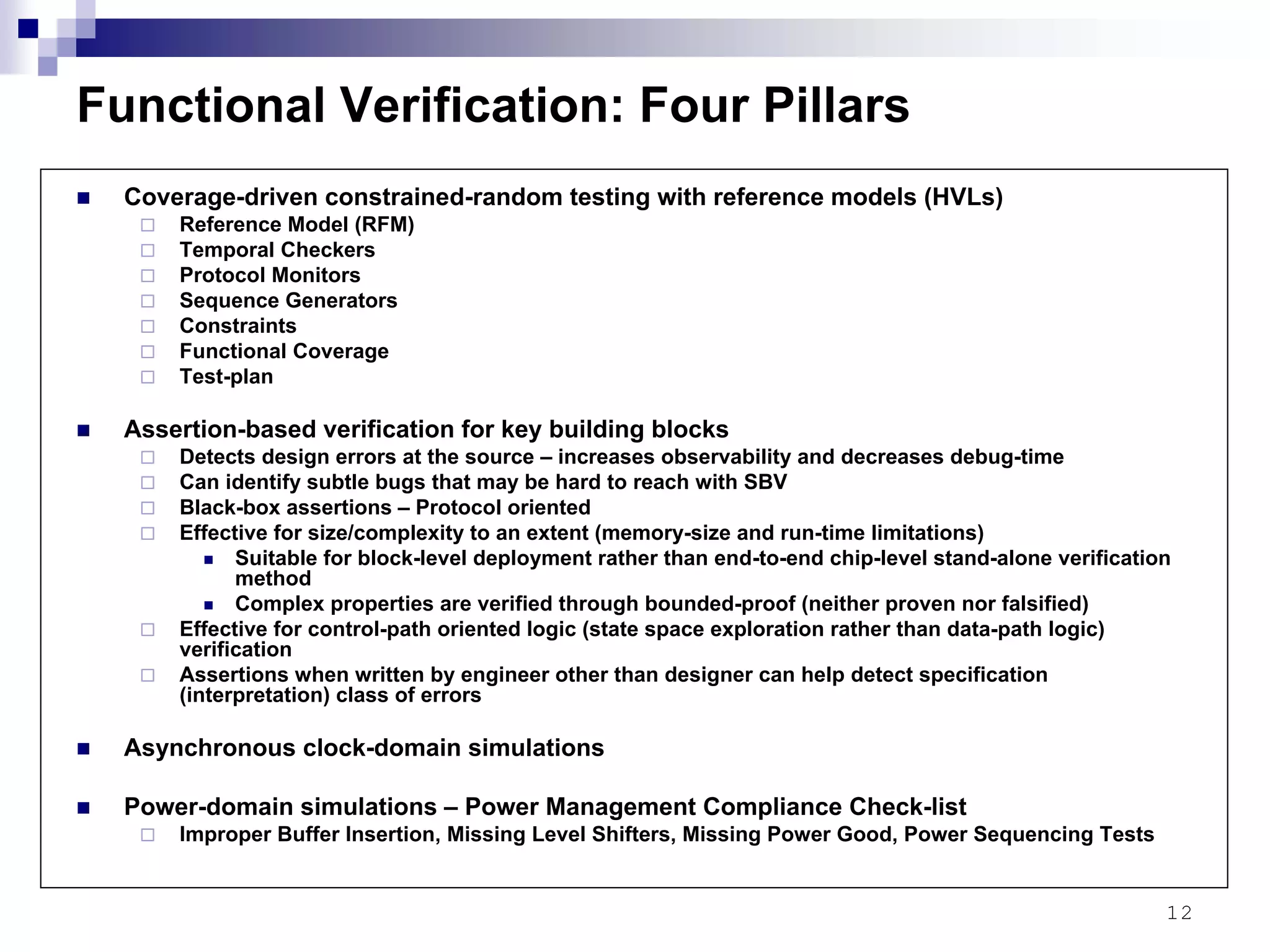
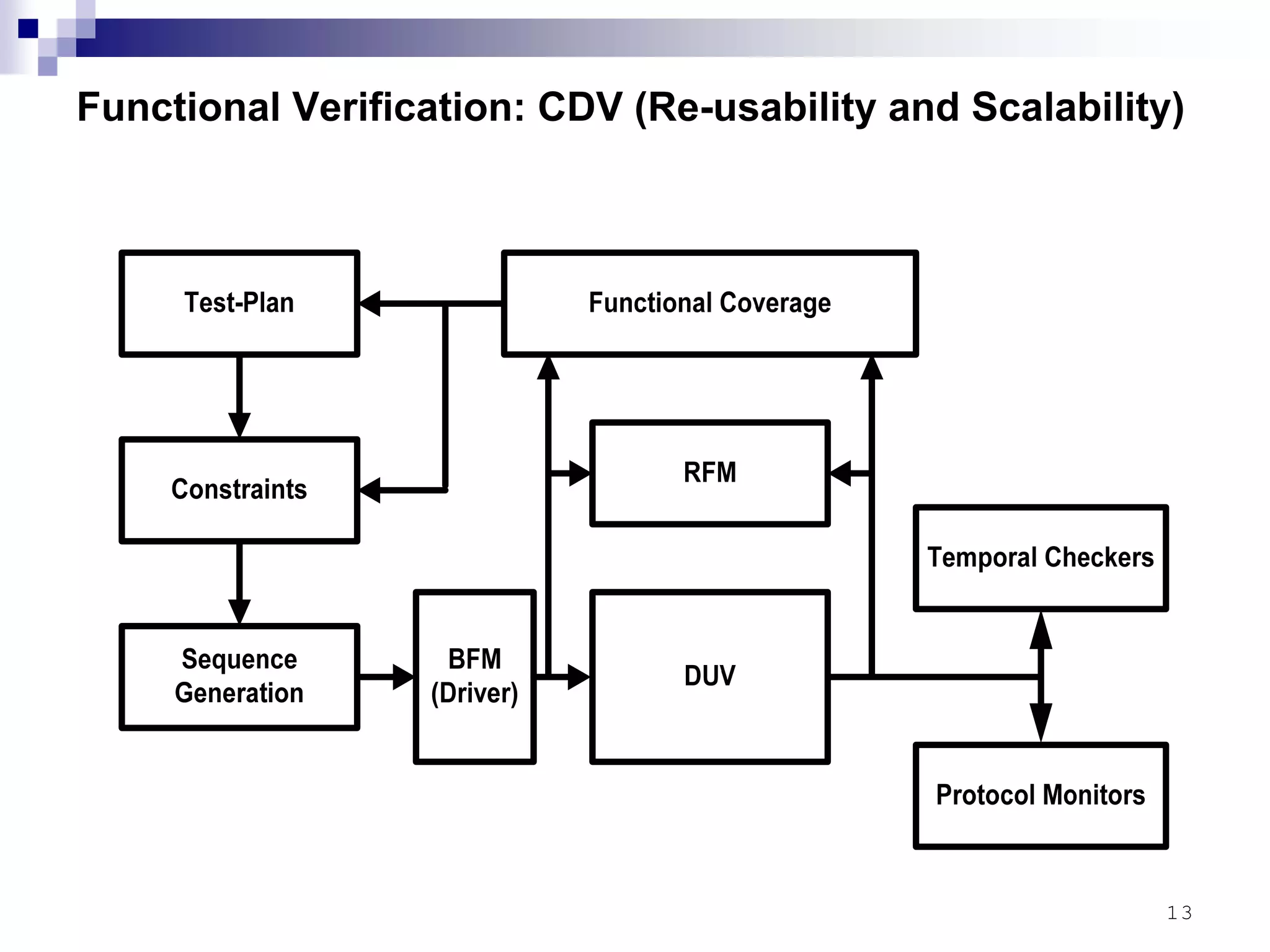
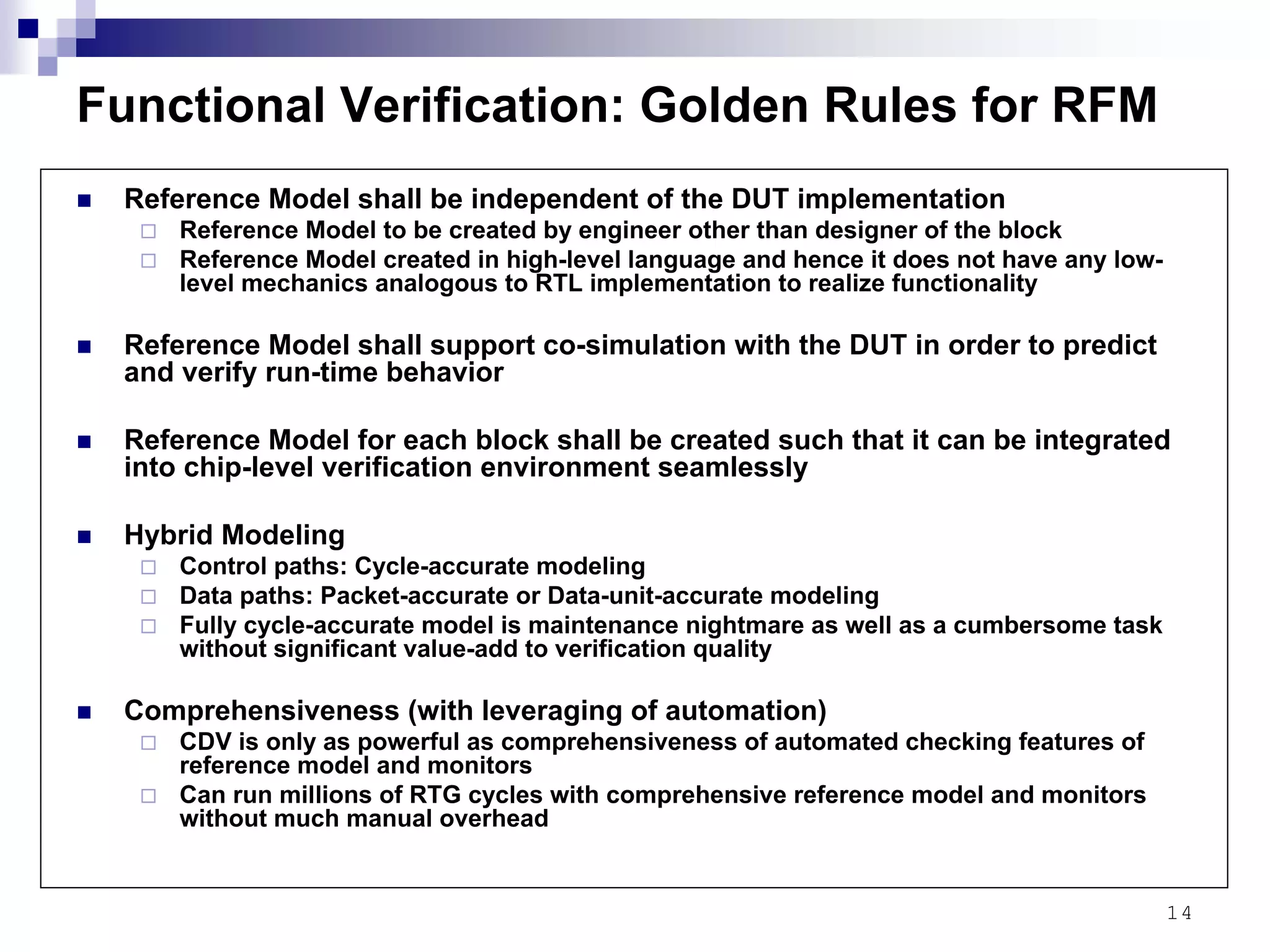
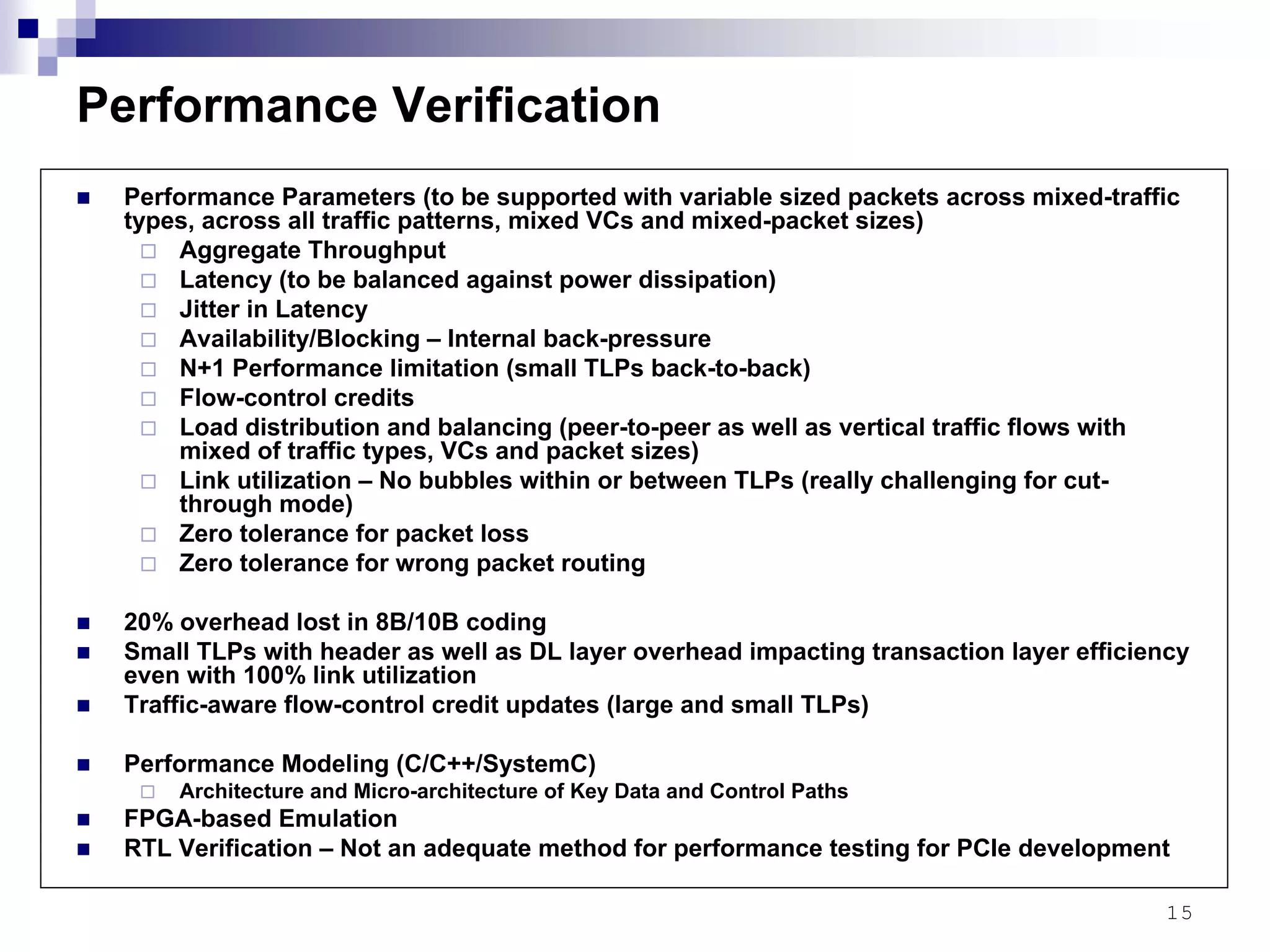
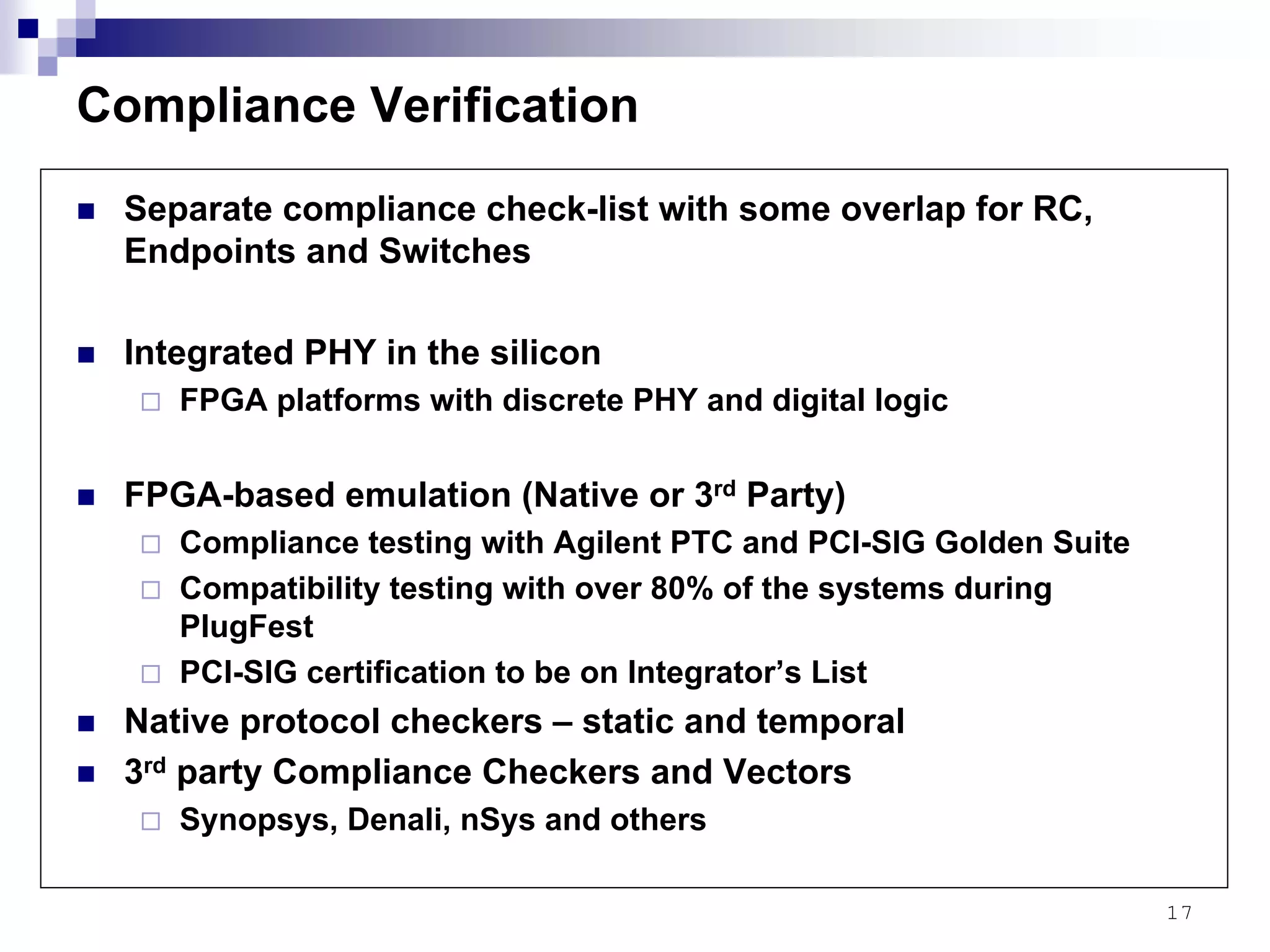
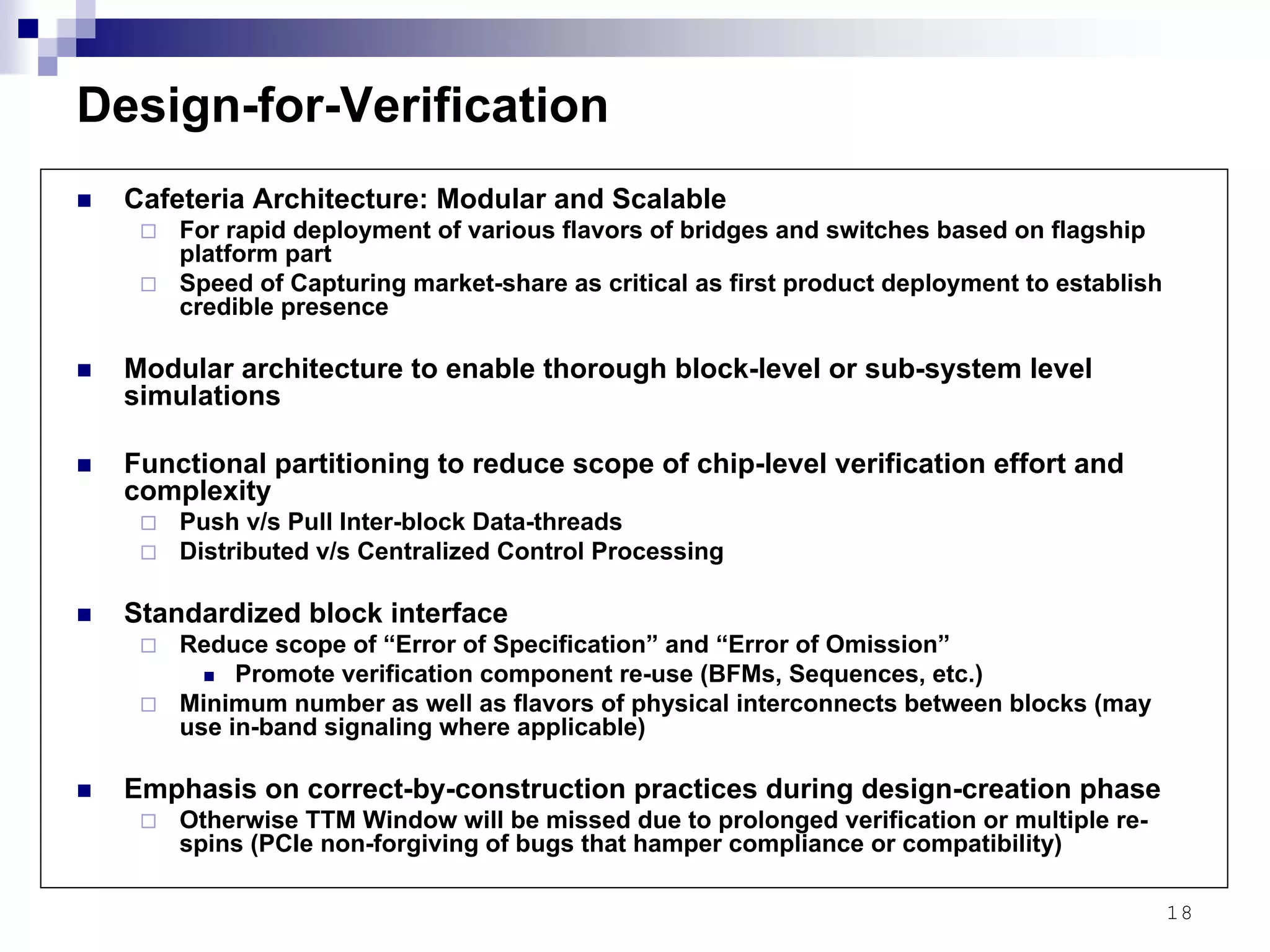
This document provides an overview of the verification strategy for PCI-Express. It discusses the PCI-Express protocol, including the physical, data link, transaction, and software layers. It outlines the verification paradigm, including functional verification using constrained random testing, assertions, asynchronous/power domain simulations, and performance verification. It also discusses compliance verification through electrical, data link, transaction, and system architecture checklists. Finally, it discusses design for verification through a modular and scalable architecture to promote reusability and reduce verification effort and complexity.