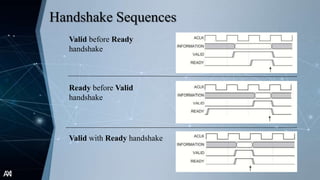
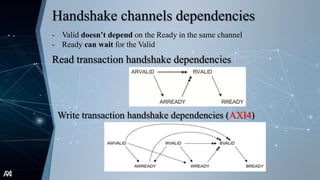
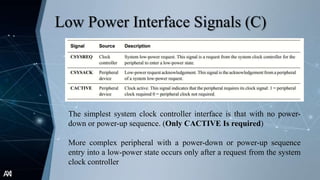
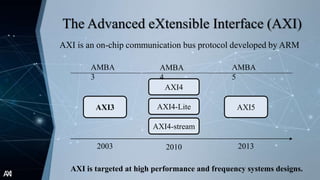
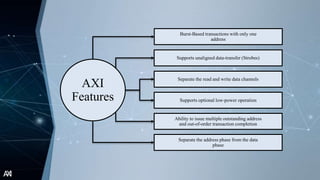
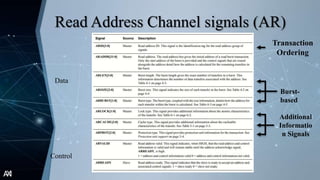
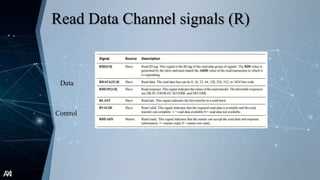
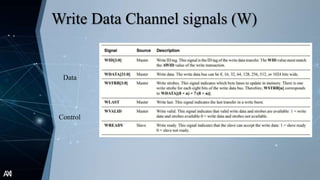
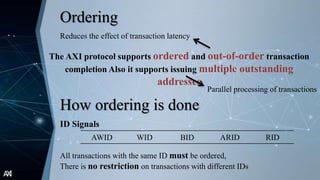
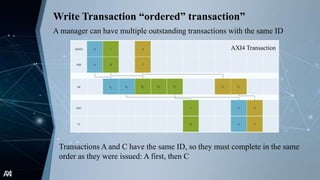
The document outlines the Advanced Extensible Interface (AXI), a high-performance communication bus protocol developed by ARM for on-chip systems, detailing its features, transactions, and architecture. Key aspects discussed include burst-based transactions, separate read/write channels, support for out-of-order transactions, and various addressing options. It also describes protocol signals for read and write operations, transaction ordering, and low-power interface capabilities.
























![AXI
Protect Signal
Information about the level of access protection
PROT [2:0] Protection Level
bit[0]
1= privileged access
0 = normal access
bit[1]
1 = nonsecure access
0 = secure access
bit[2]
1 = instruction access
0 = data access
Protection encoding](https://image.slidesharecdn.com/axiprotocol-221025120544-c6fcd19c/85/AXI-Protocol-pptx-32-320.jpg)