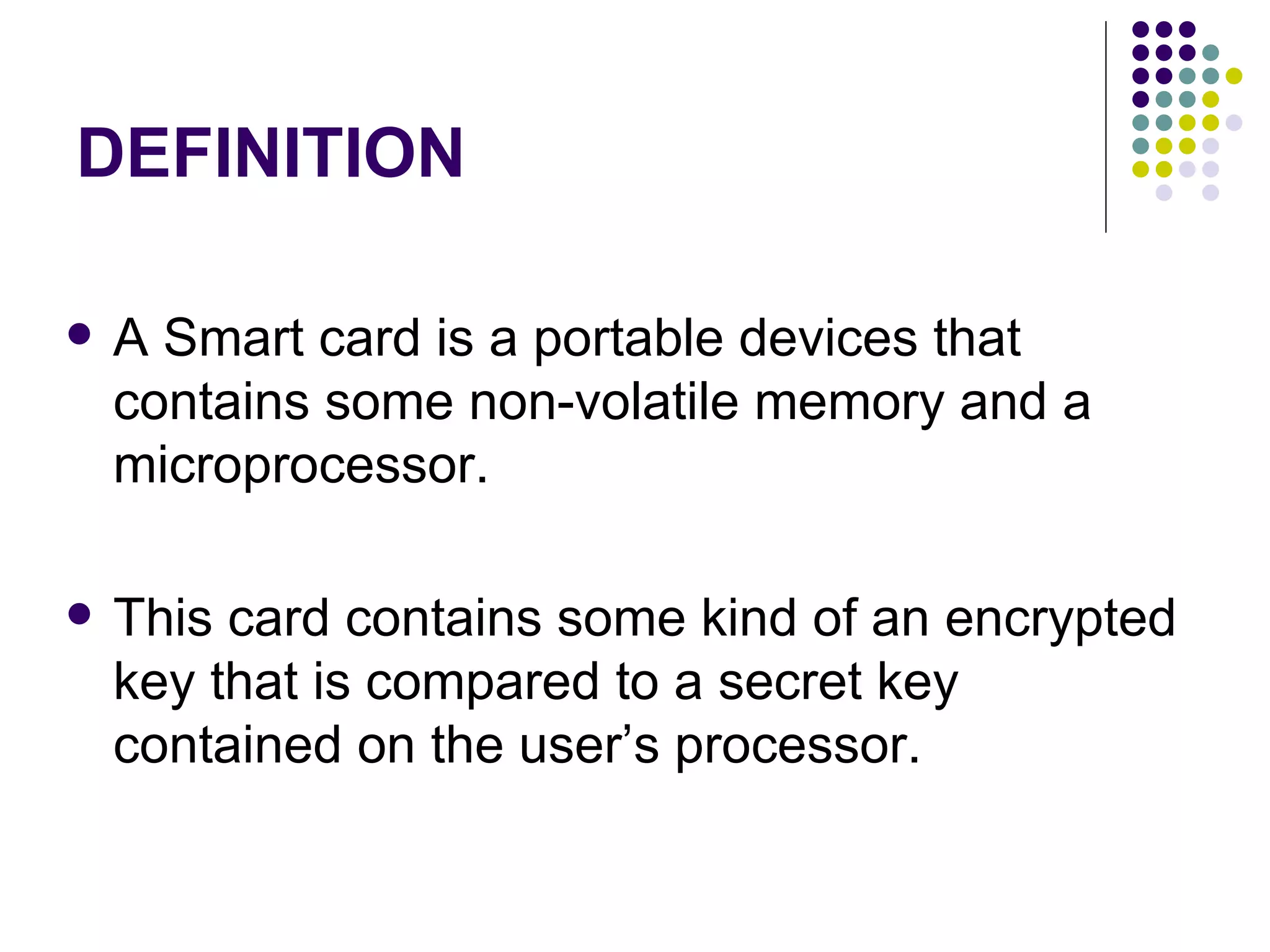
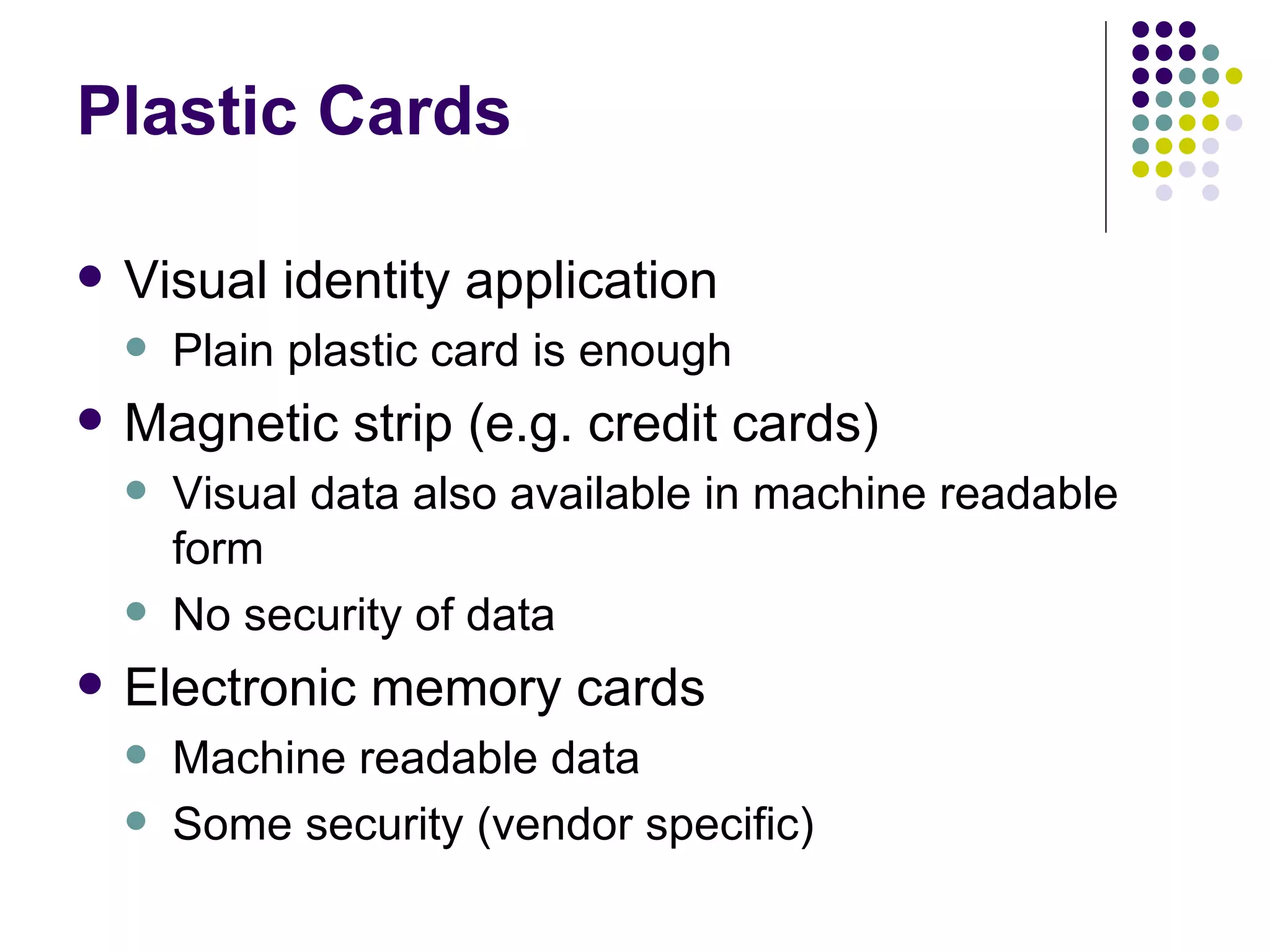
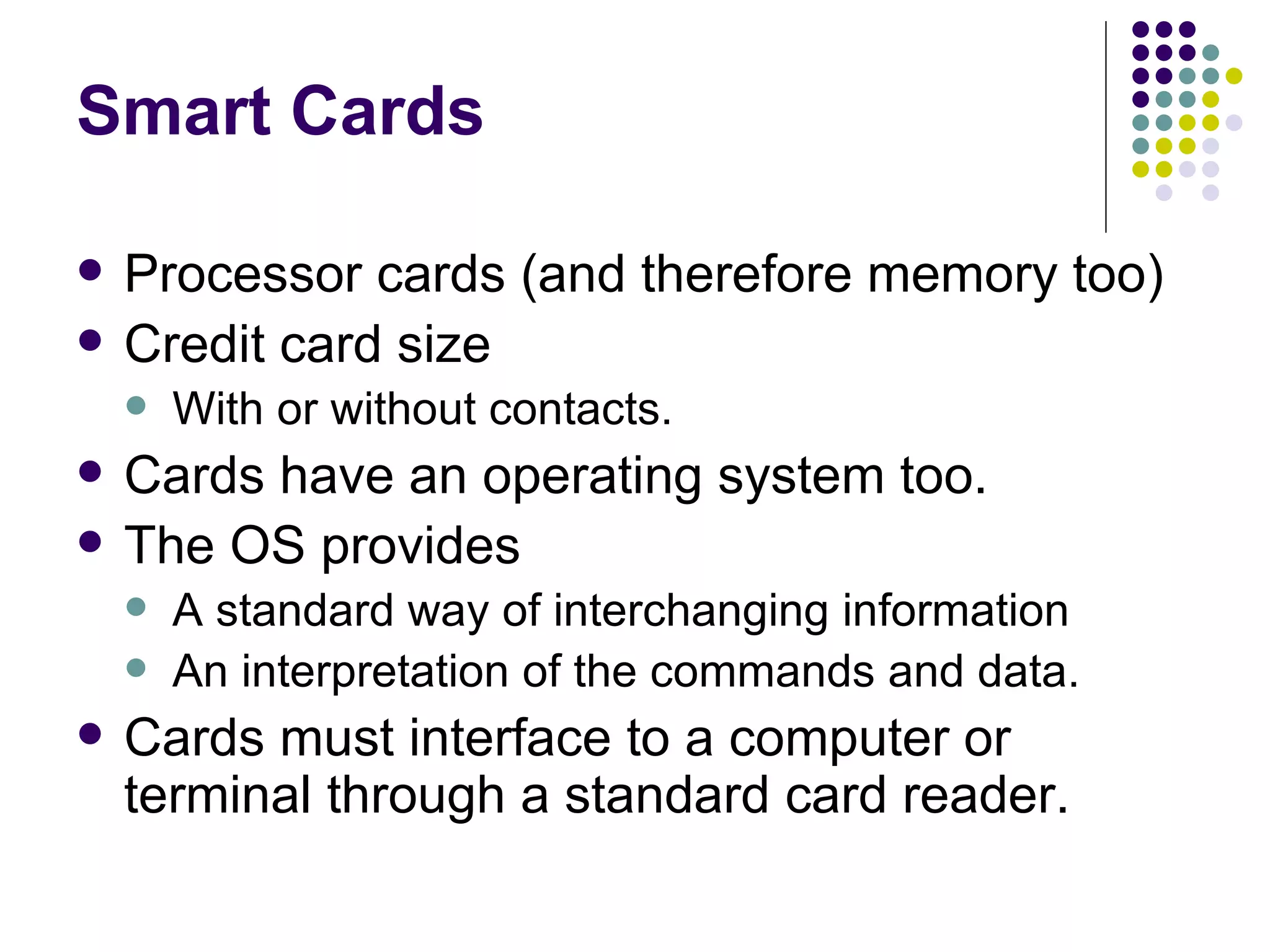
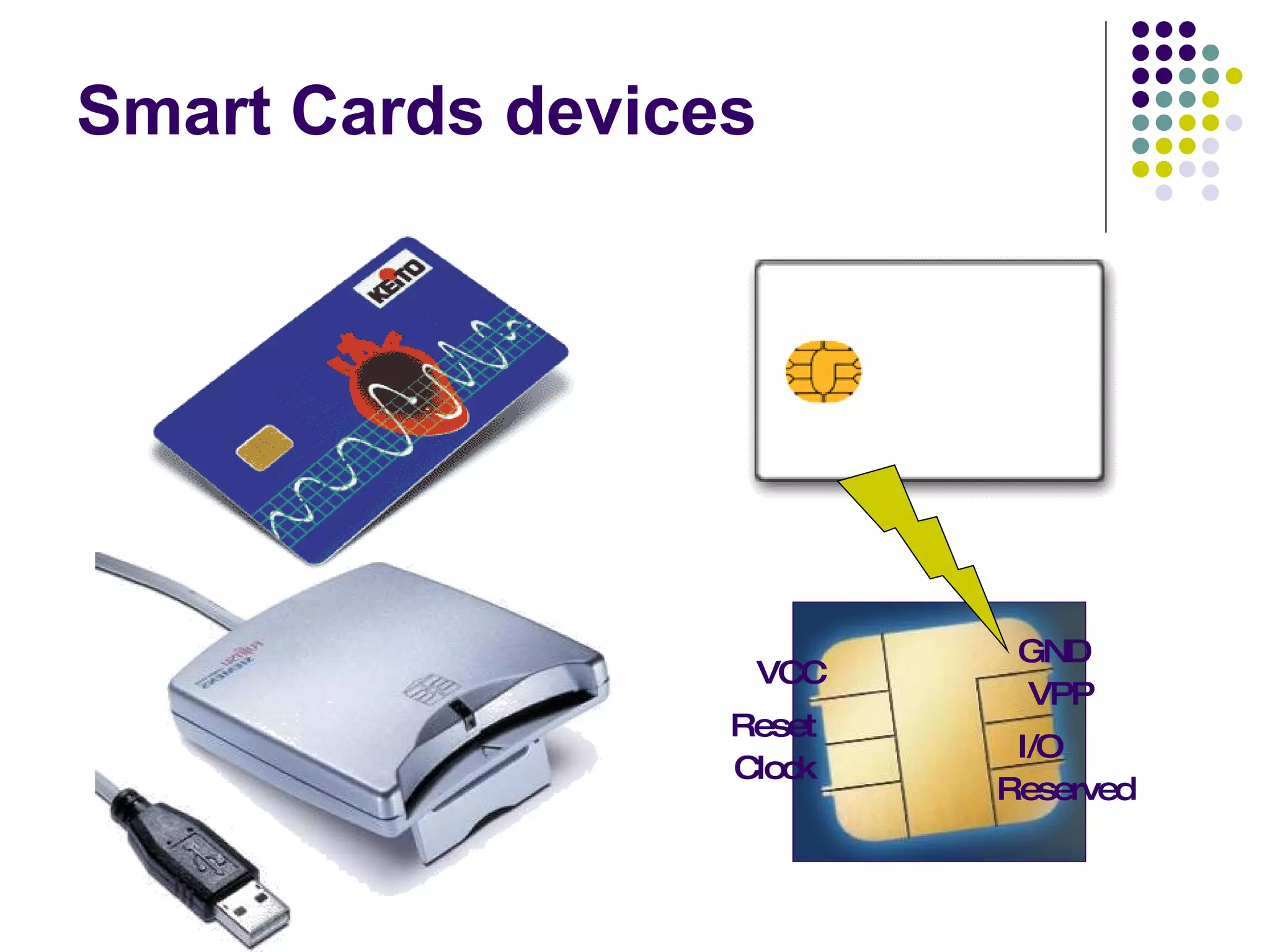
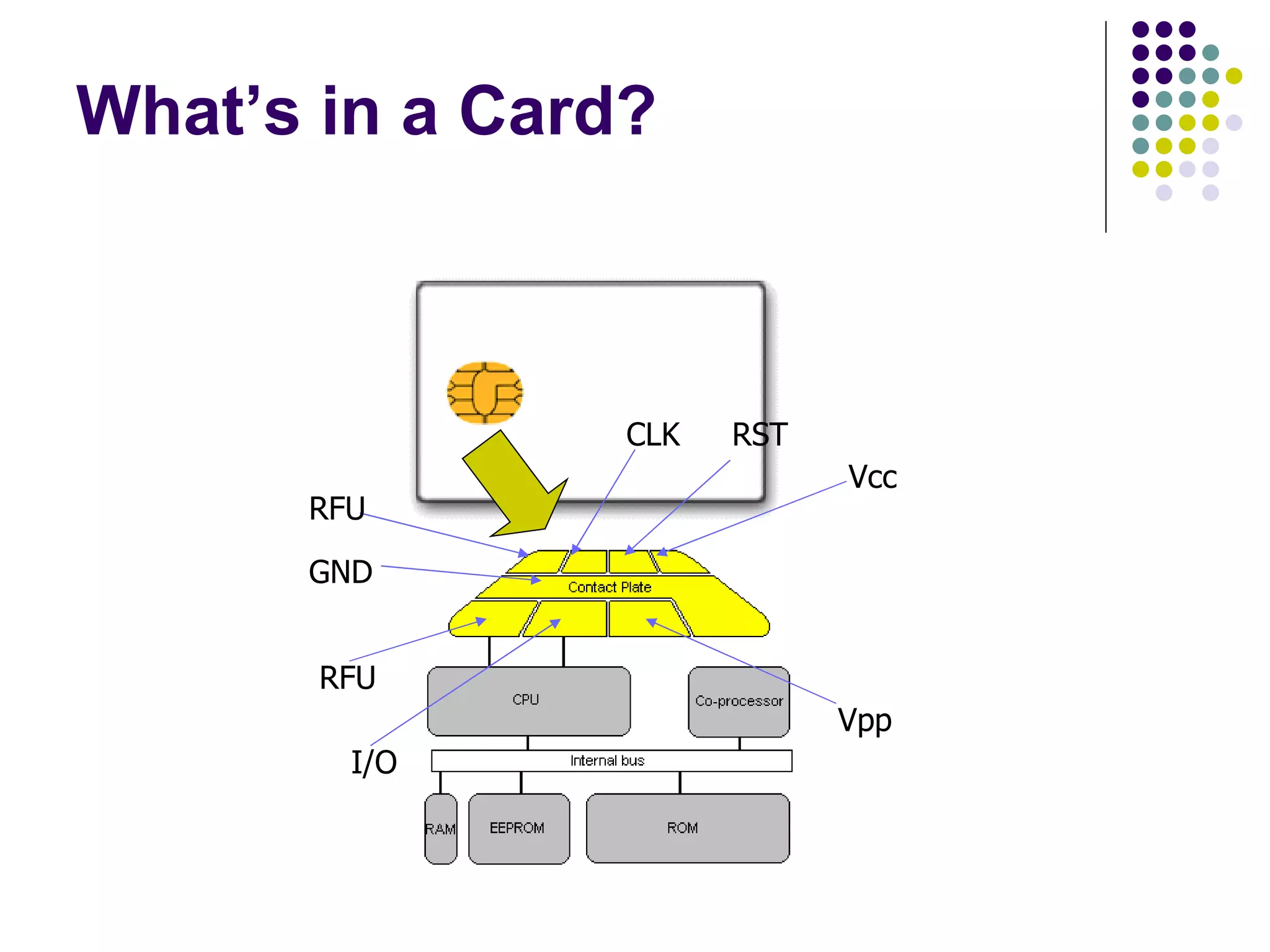
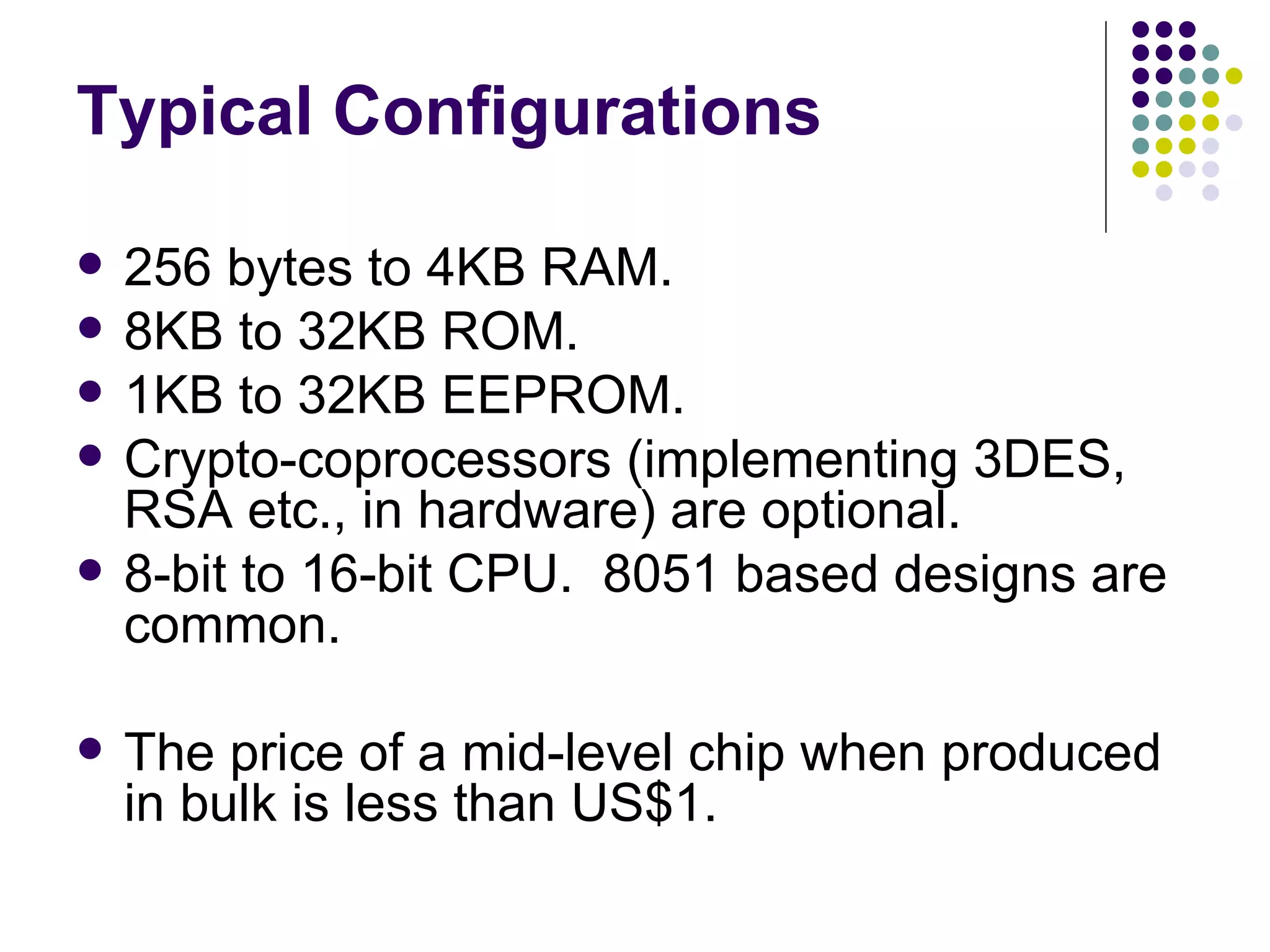
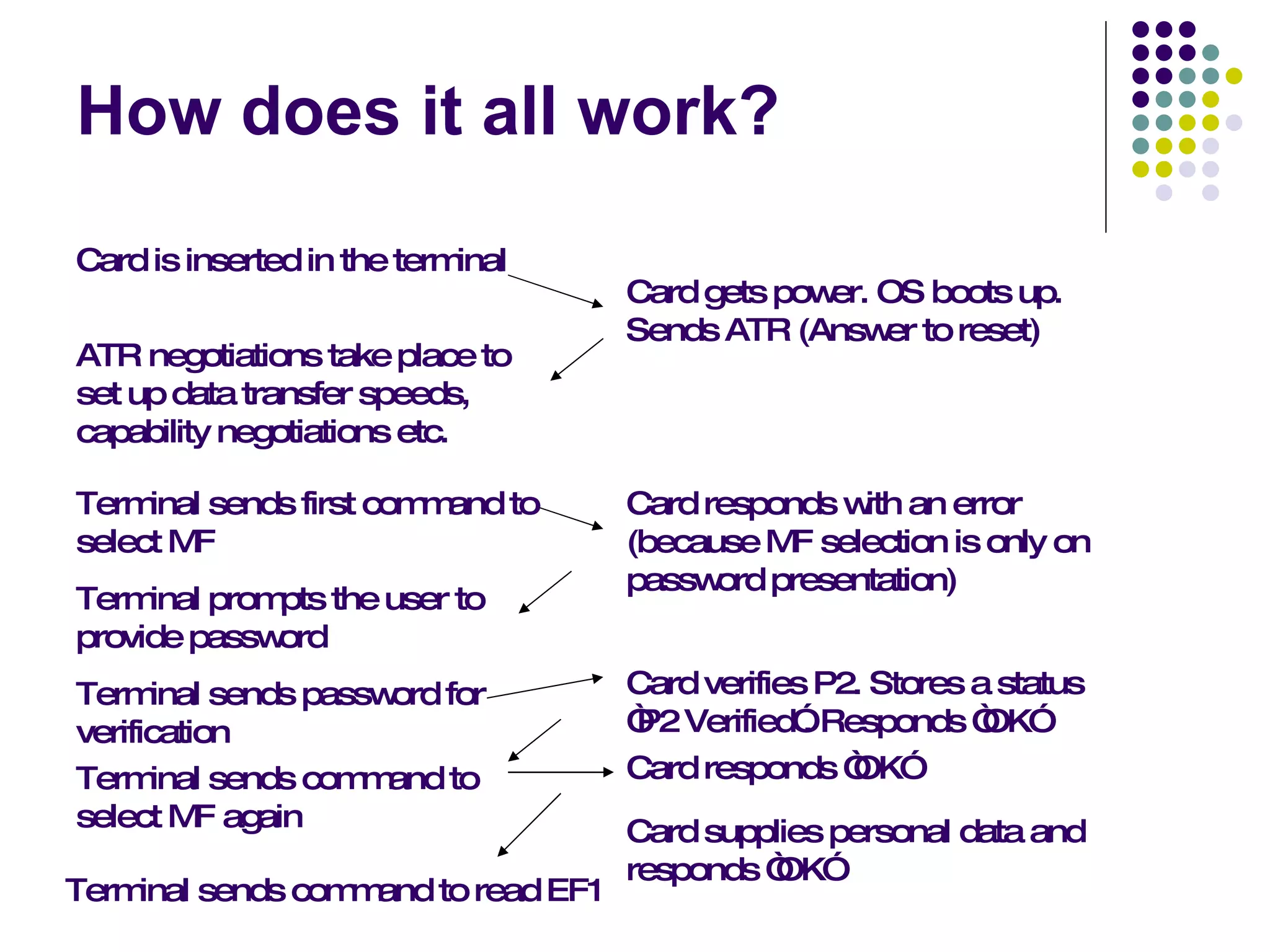
Smart cards are portable devices that contain memory and a microprocessor. They provide security through the use of encrypted keys and authentication mechanisms. Smart cards can store various amounts of RAM, ROM and EEPROM. They communicate with card readers through standardized protocols and provide security through password verification, cryptographic challenges, and biometric identification stored on the card. Typical smart card applications include access control of files and cryptographic authentication.