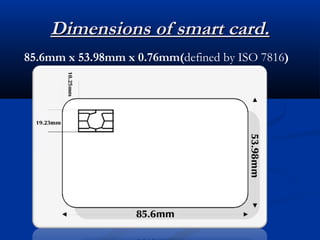
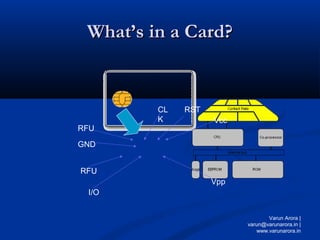
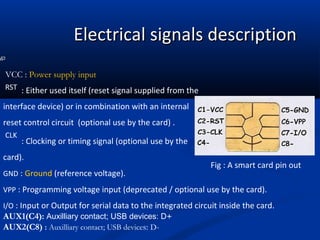
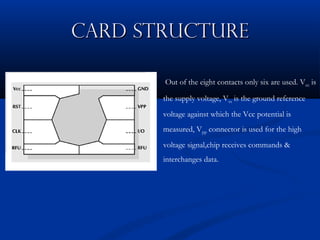
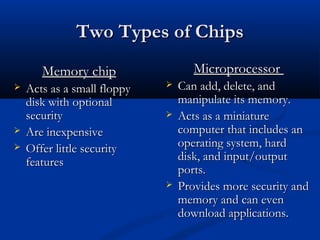
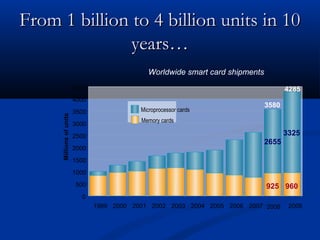
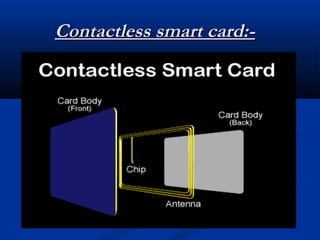
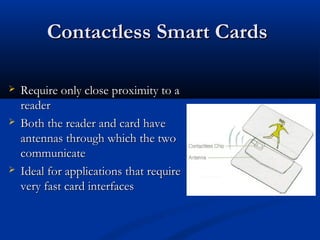
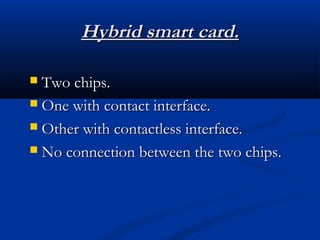
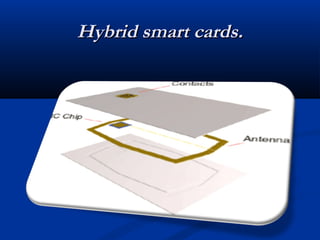
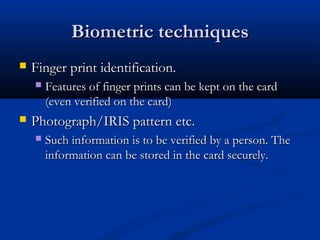
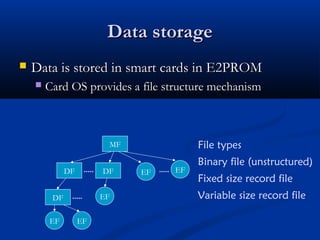
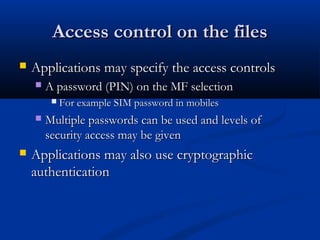
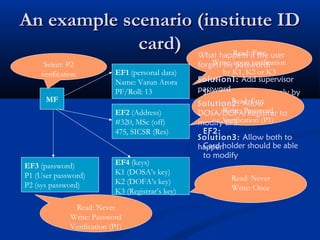
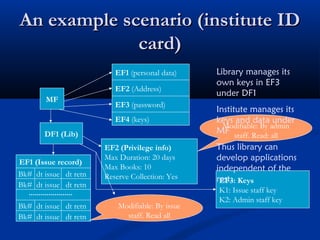
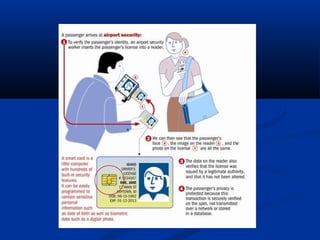
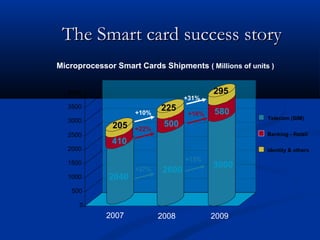
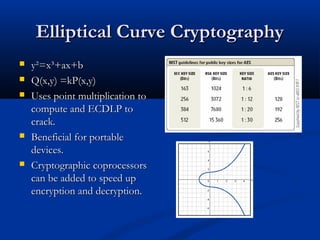
Smart cards are plastic cards with embedded microchips that can store large amounts of data securely. They provide stronger security than magnetic stripe cards by using encryption and requiring PINs for access. Common uses of smart cards include payment, identification, transportation cards, and SIM cards. They allow for multiple applications on a single card and can be updated remotely, making them a convenient technology for the future.