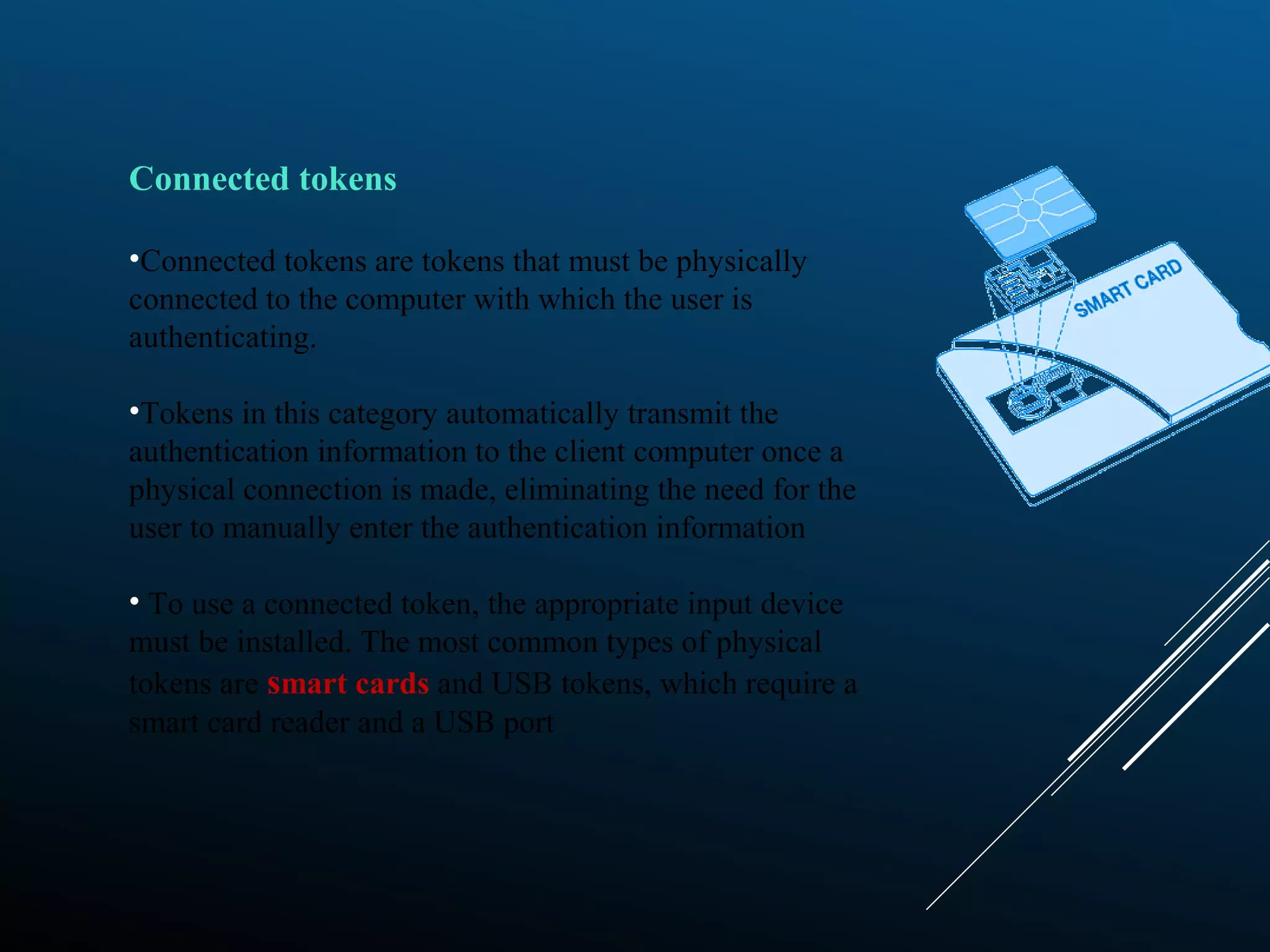
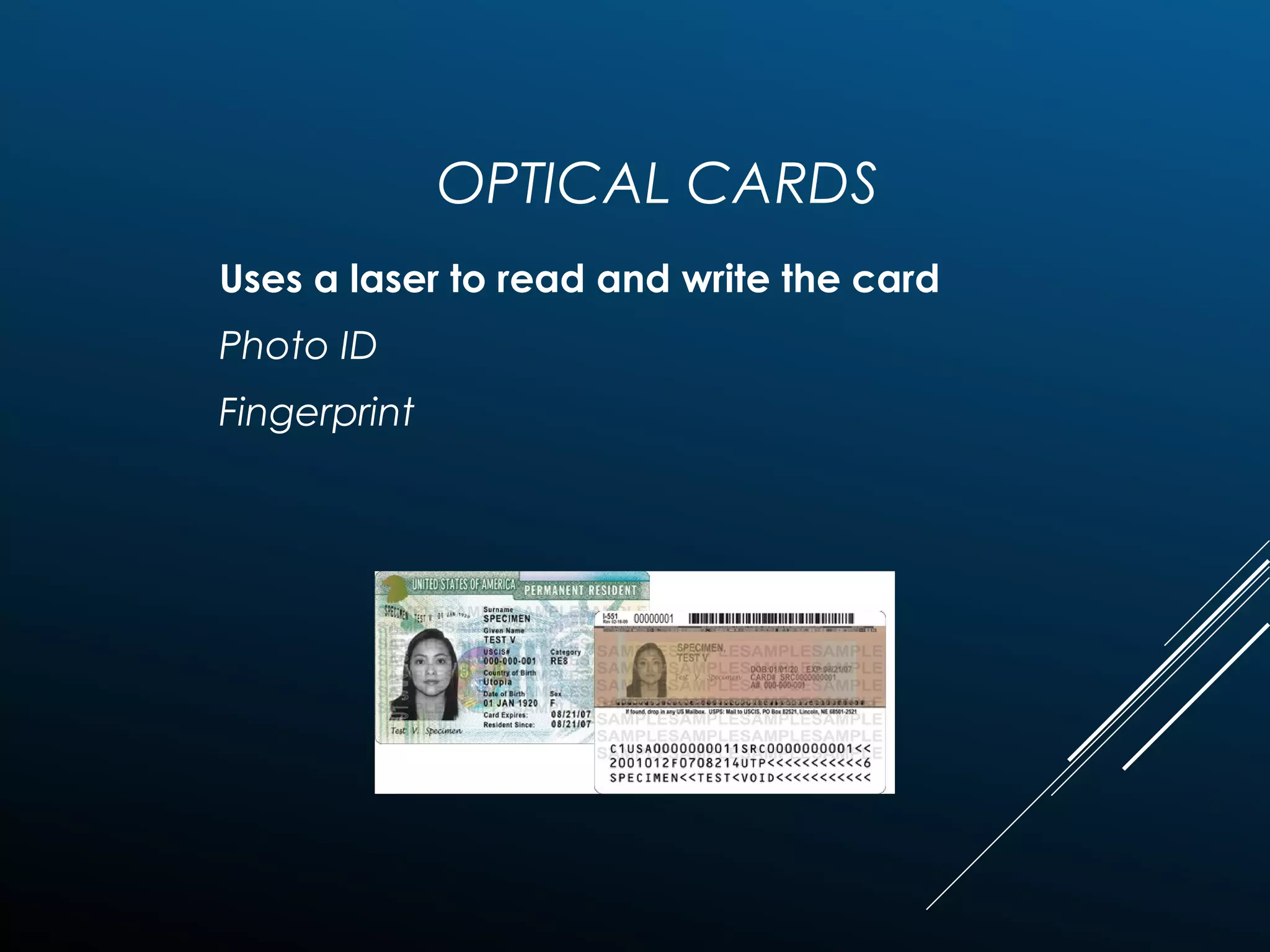
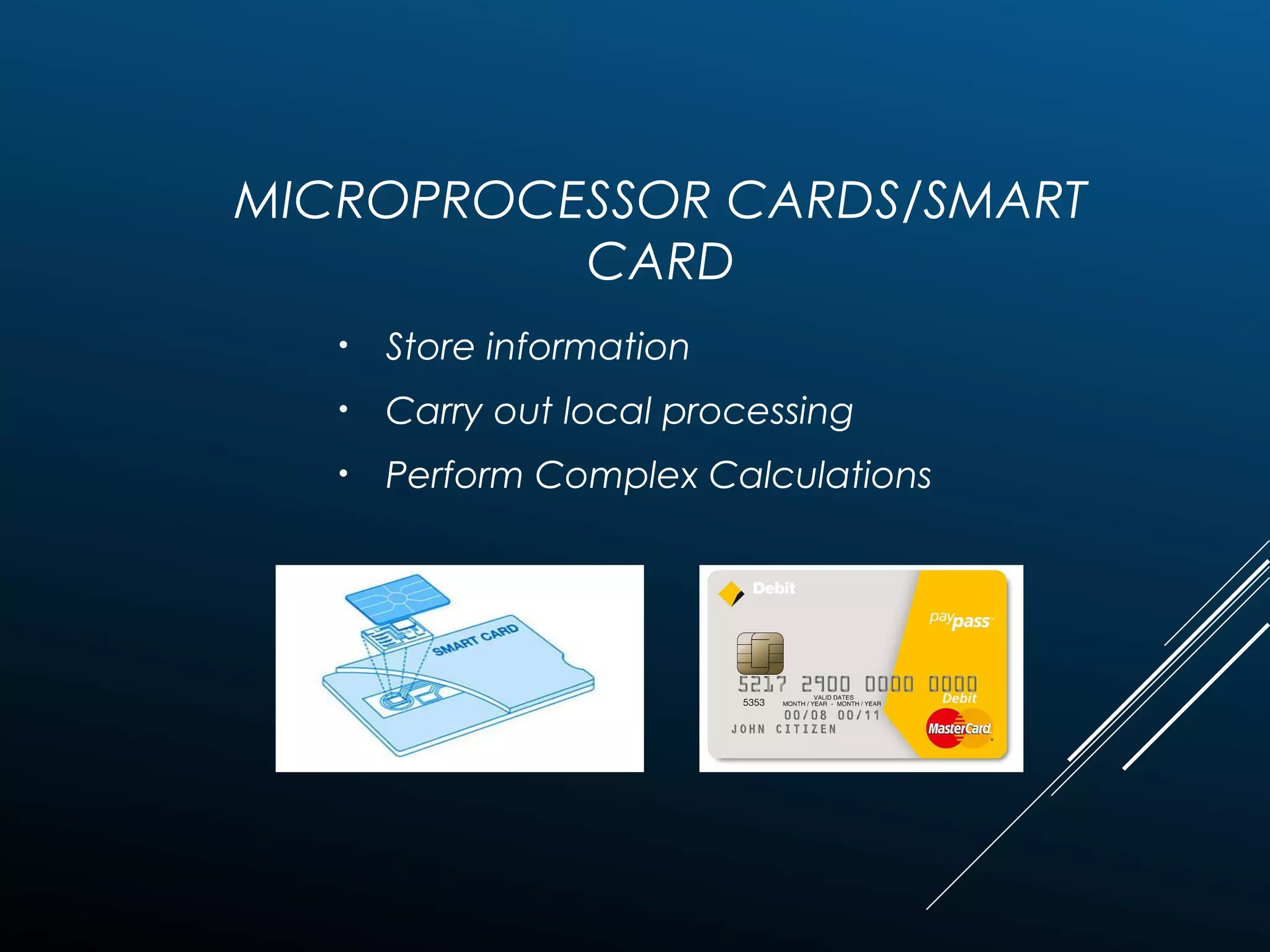
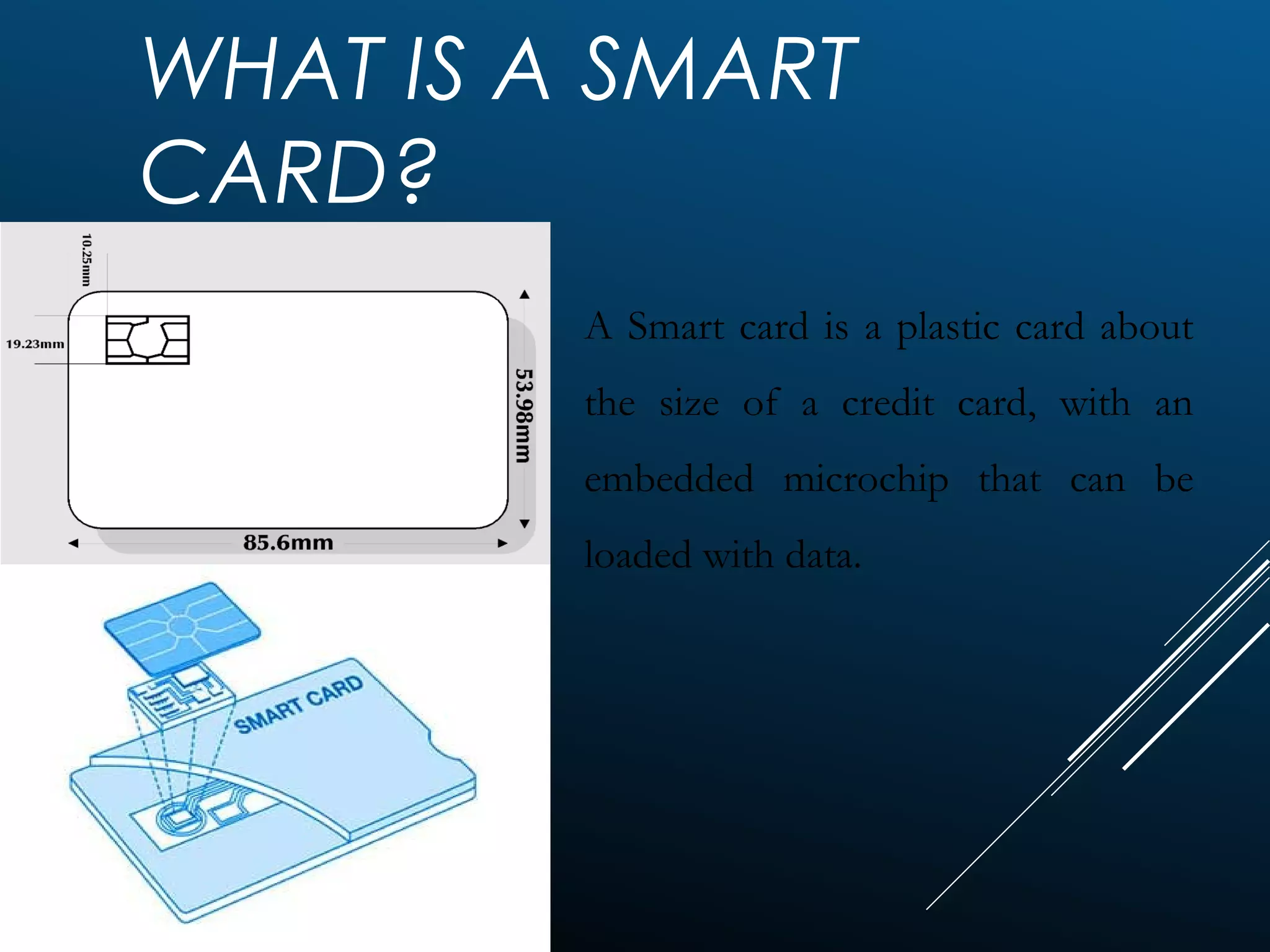
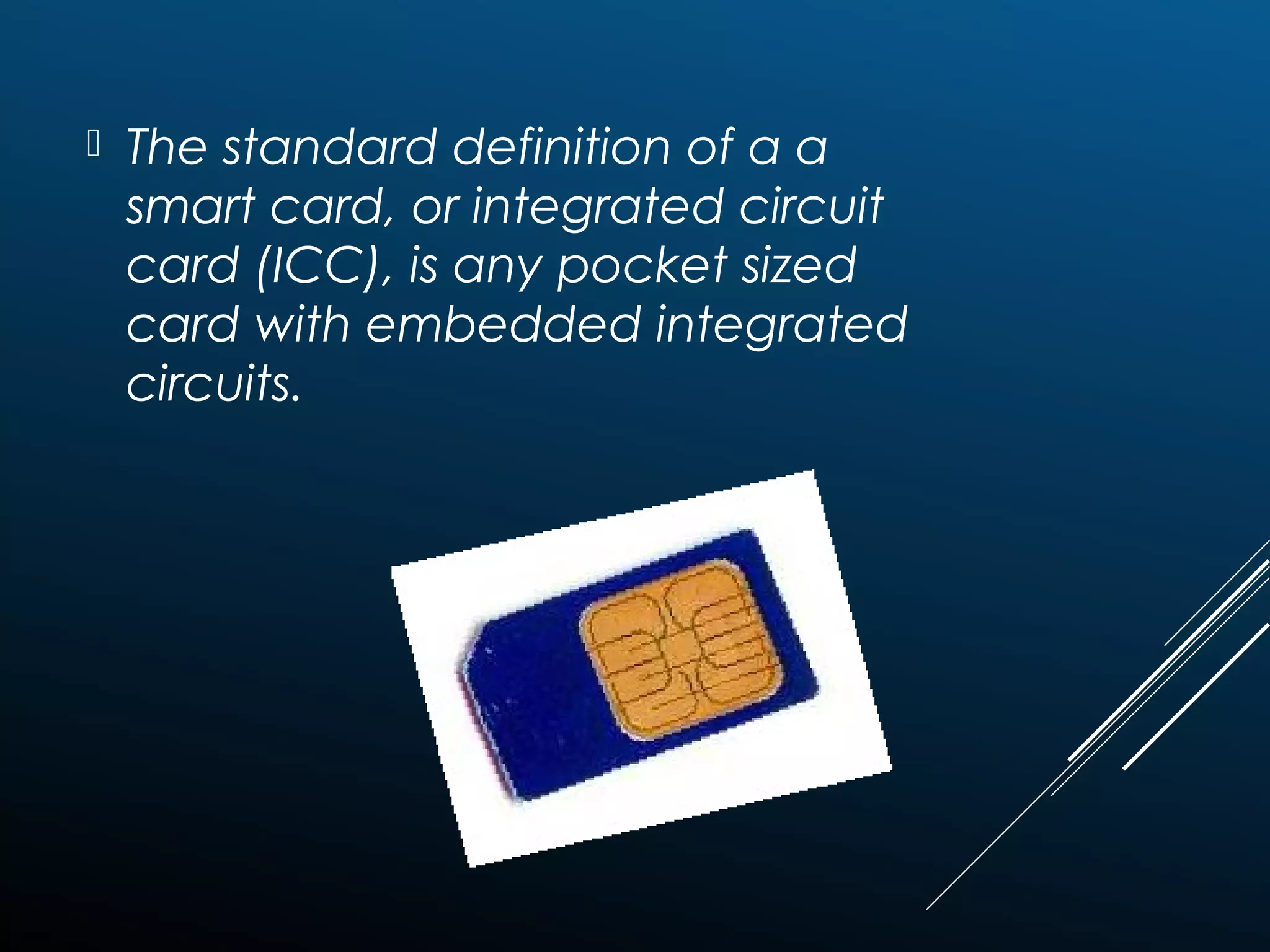
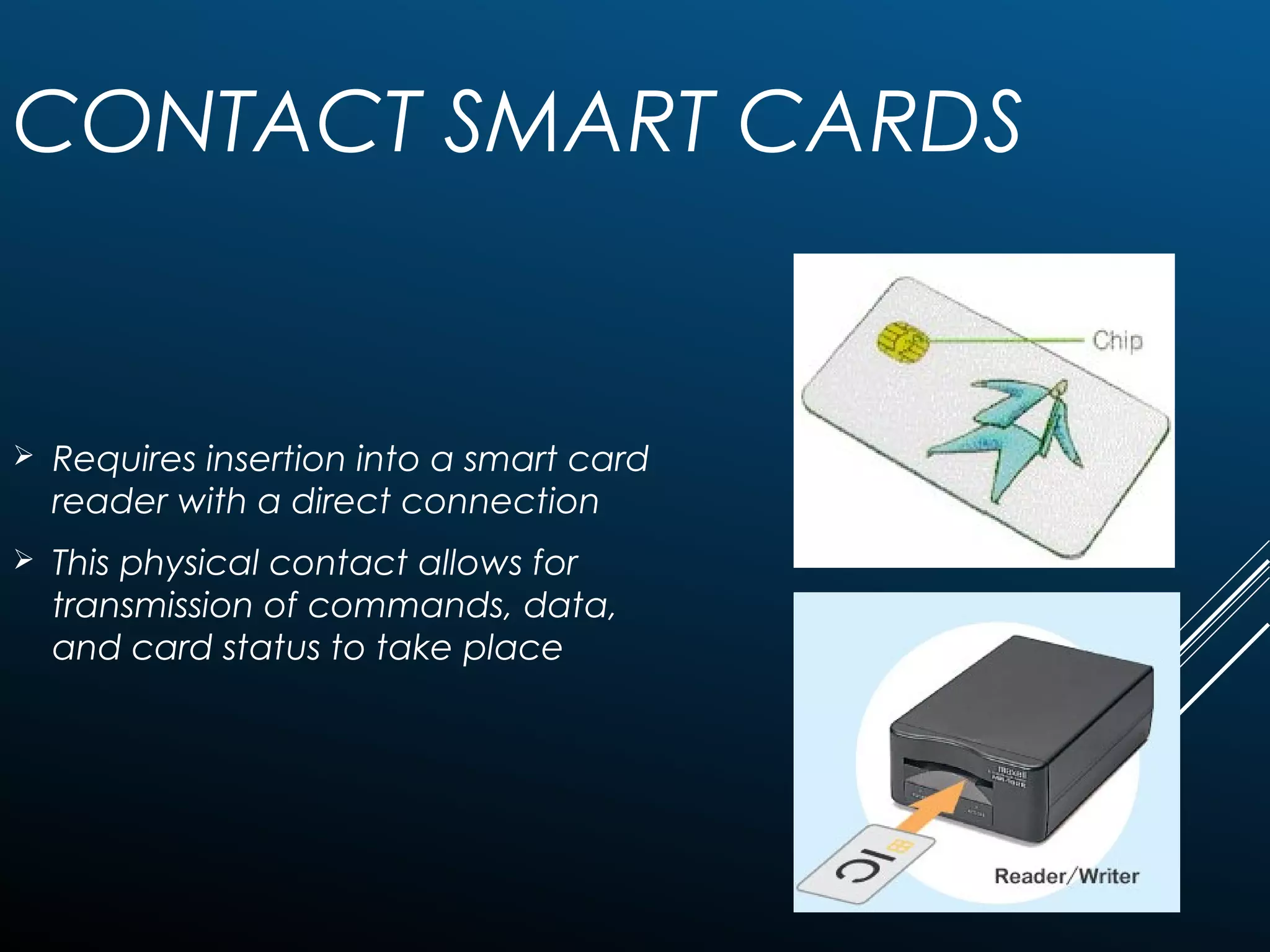
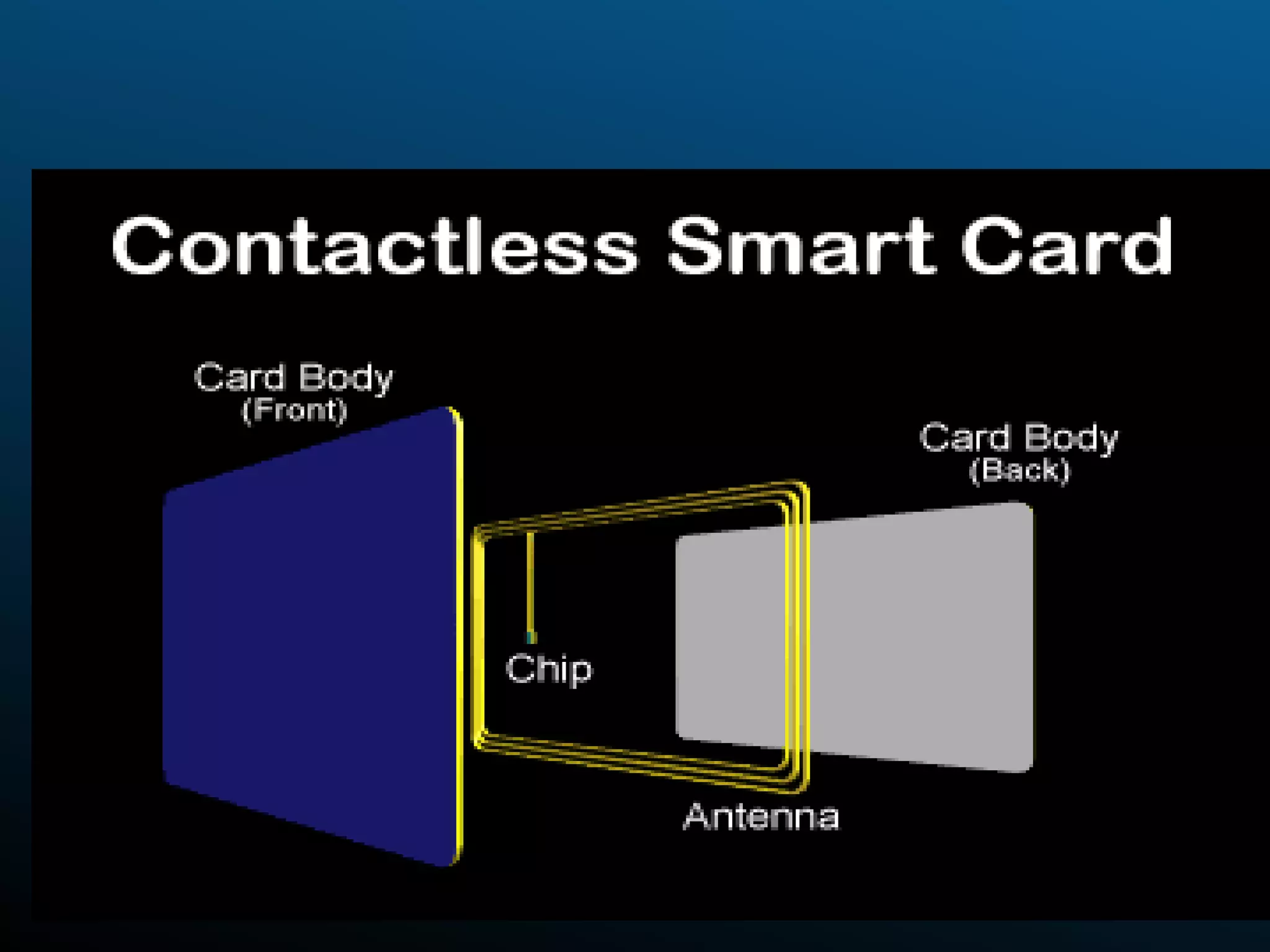
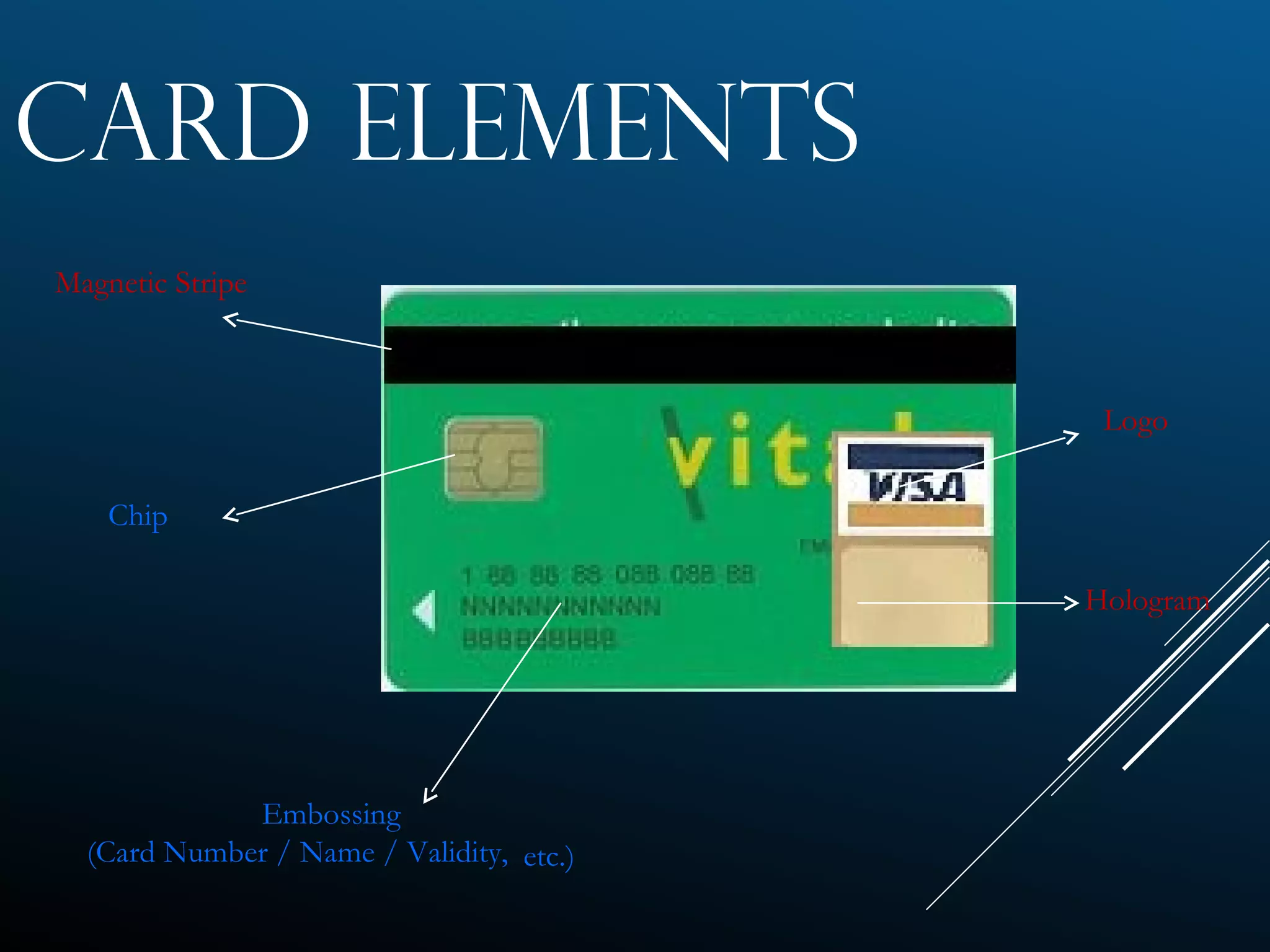
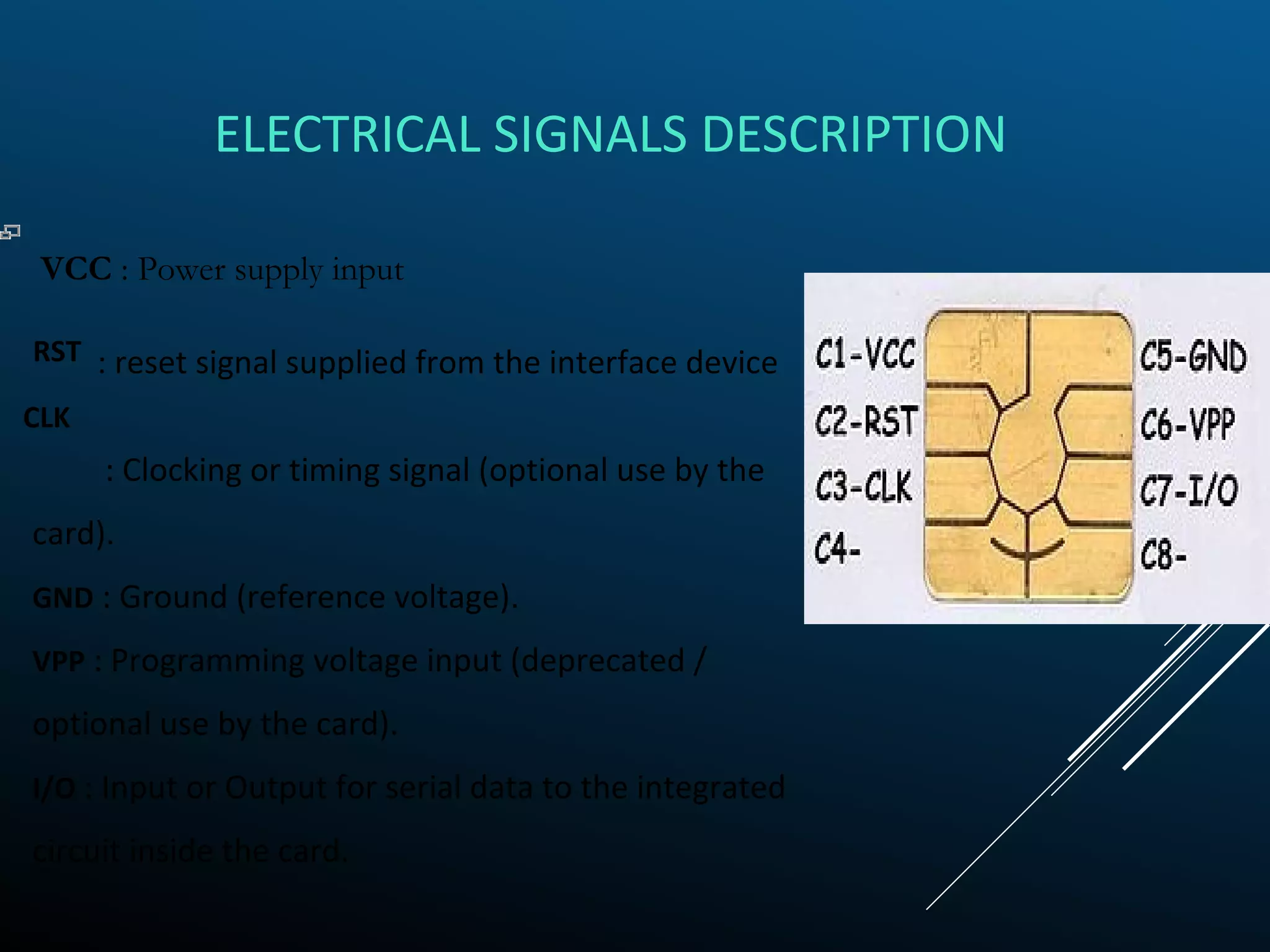
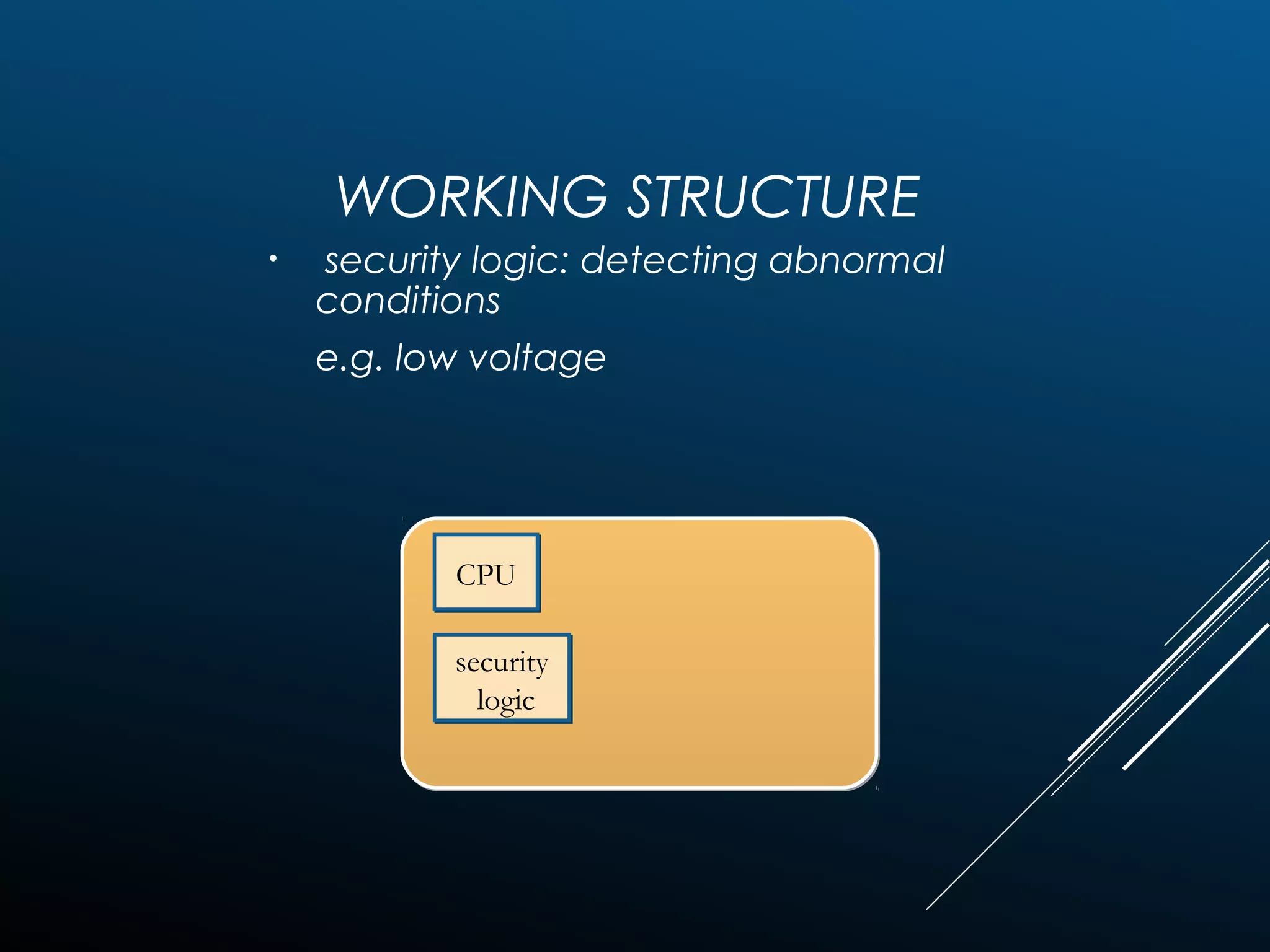
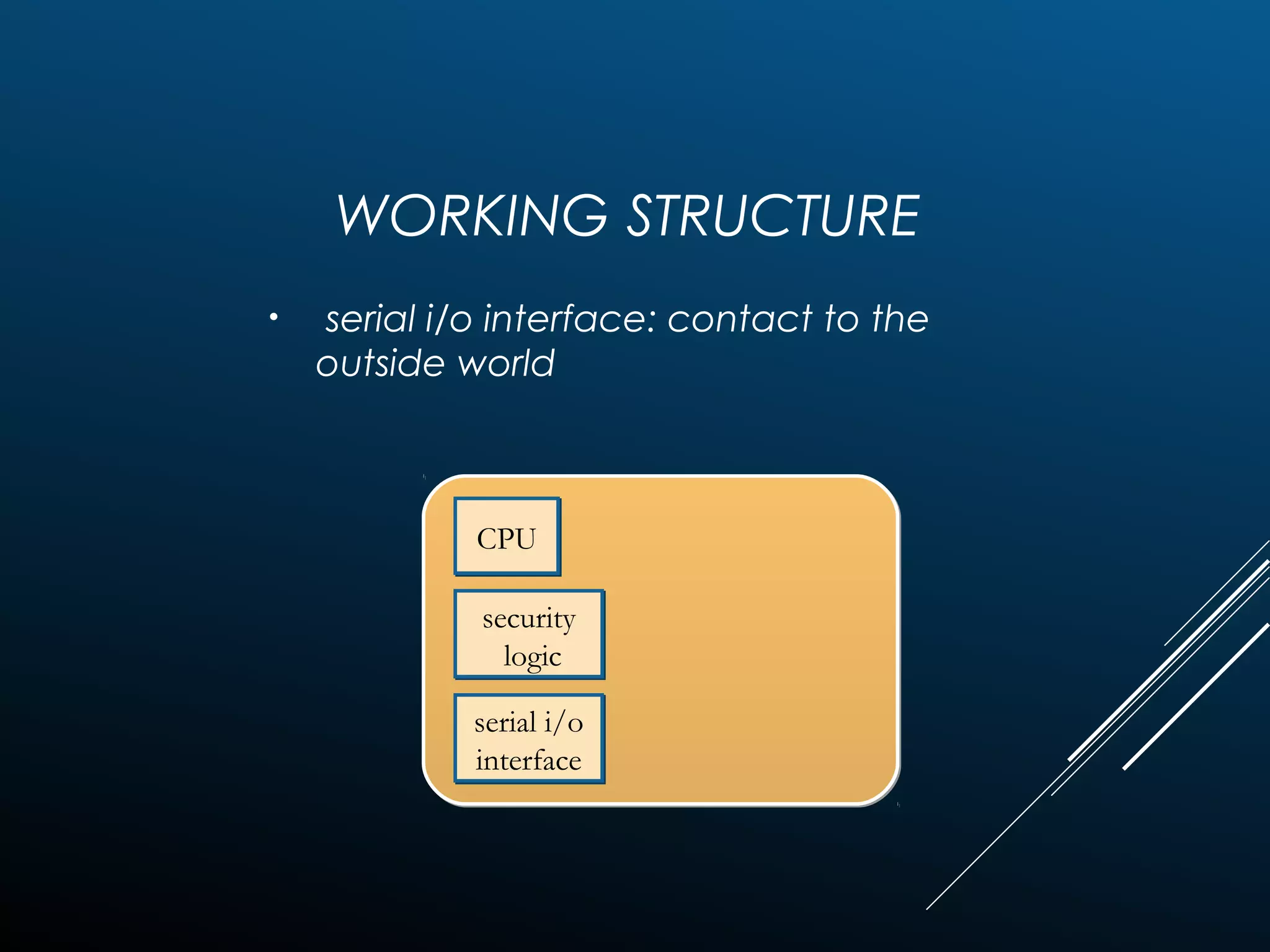
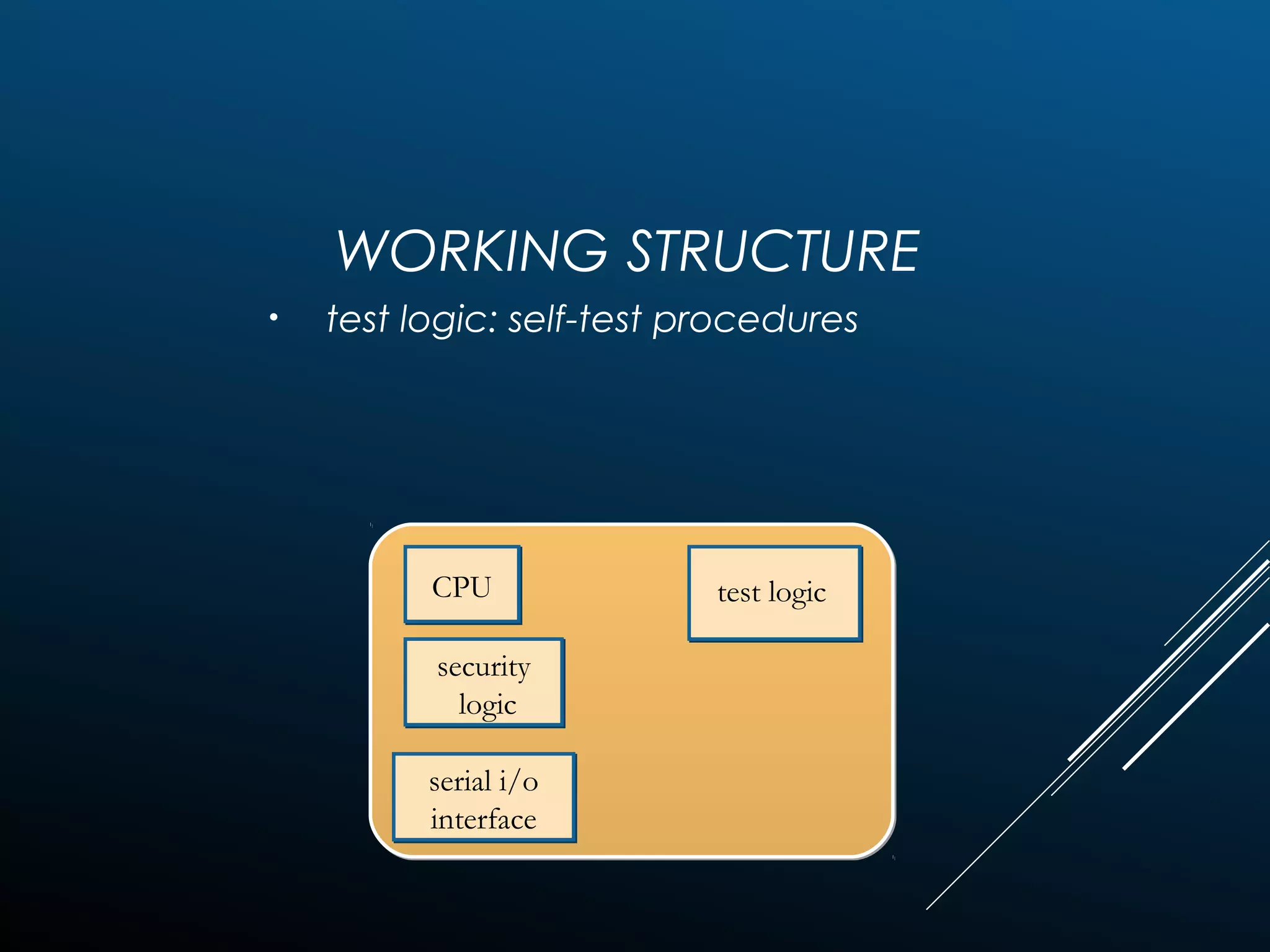
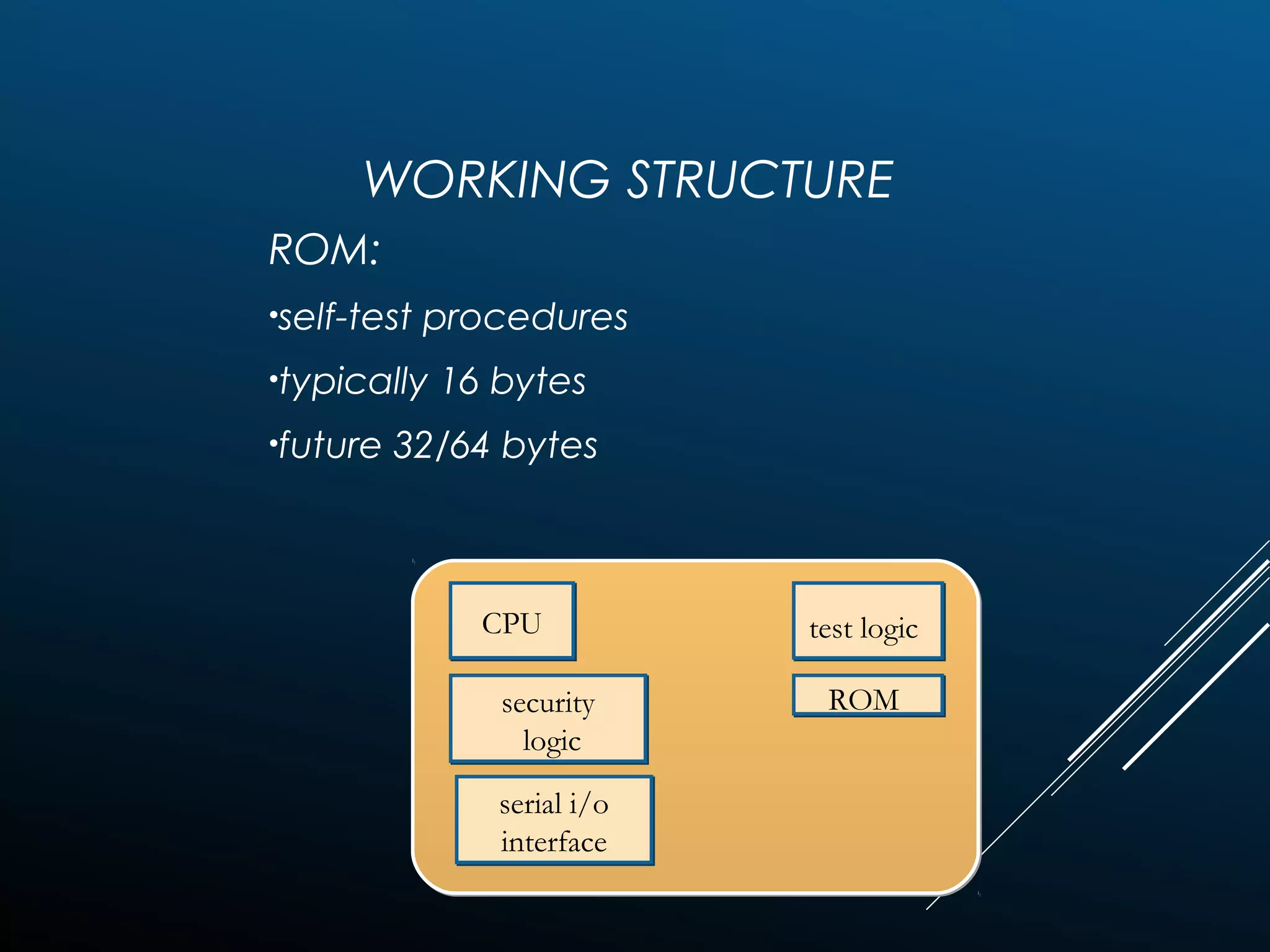
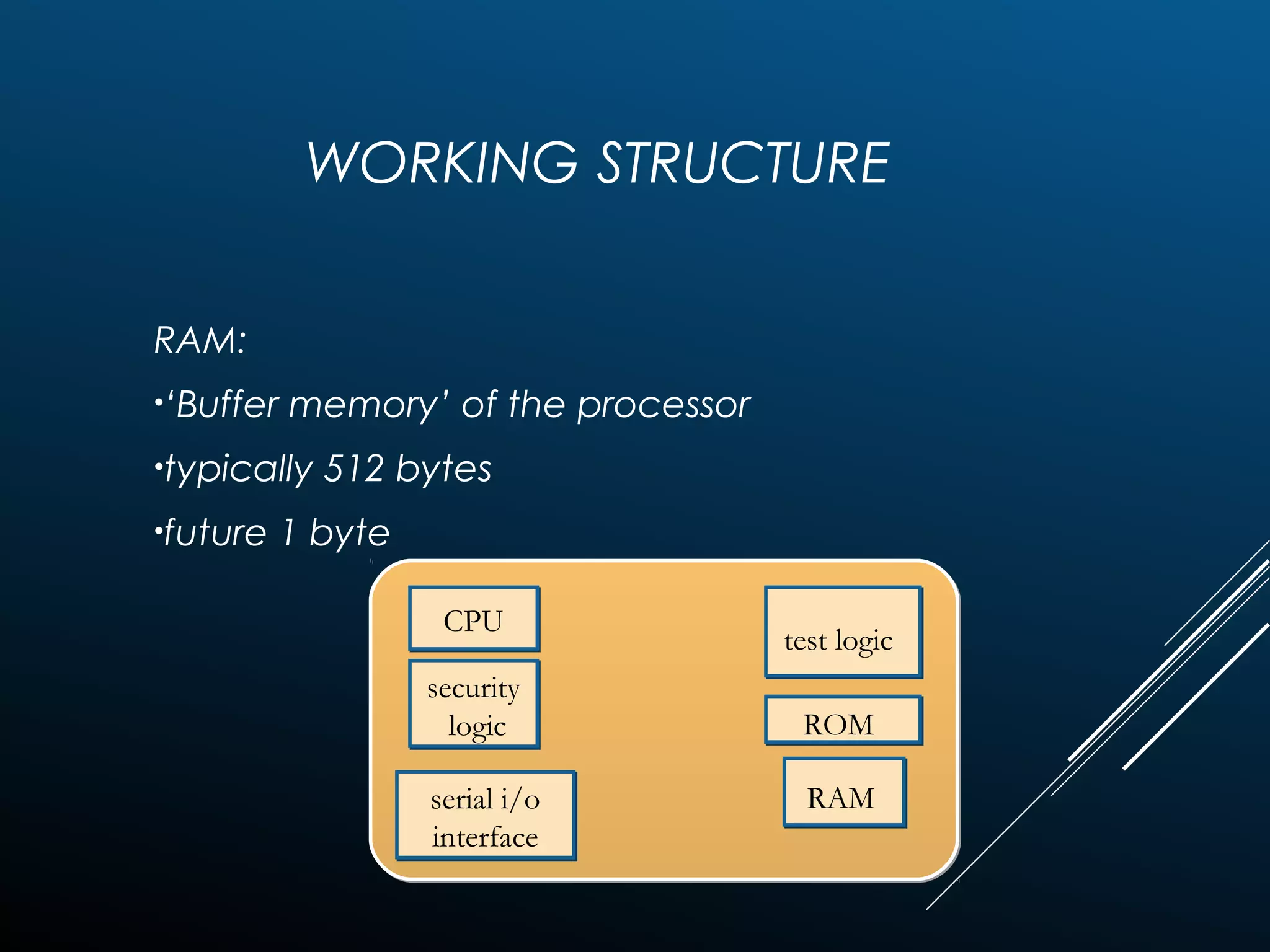
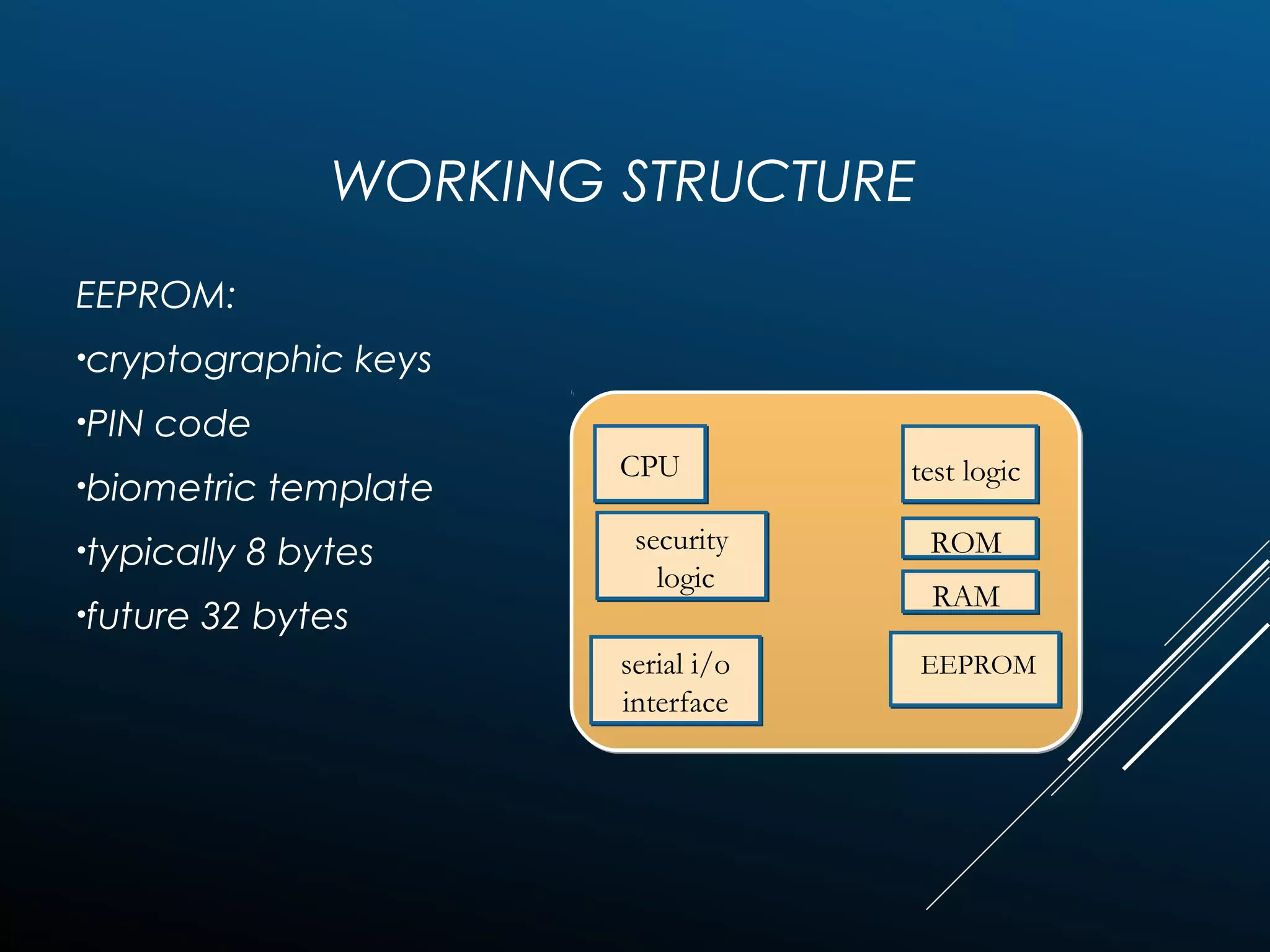
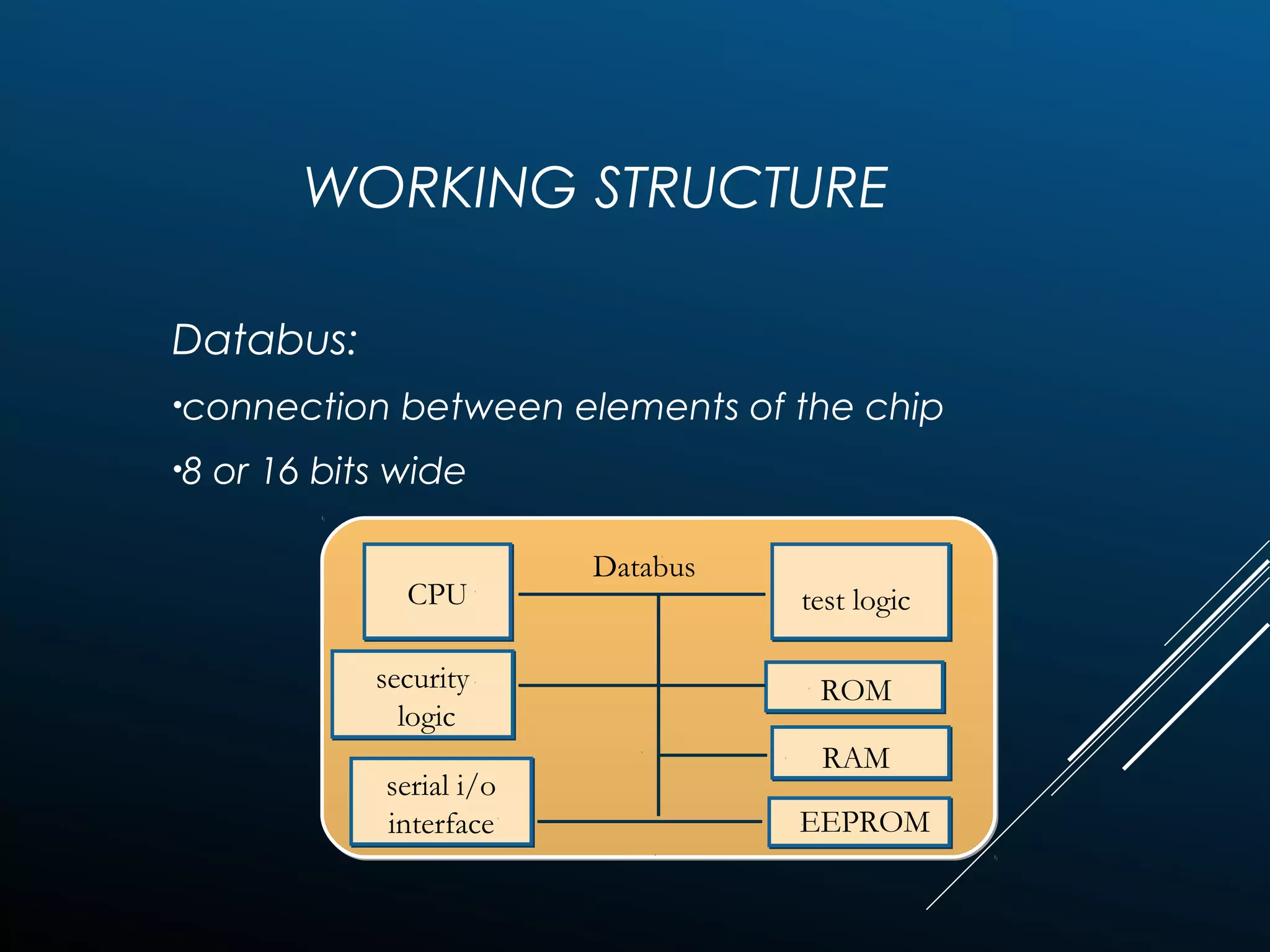
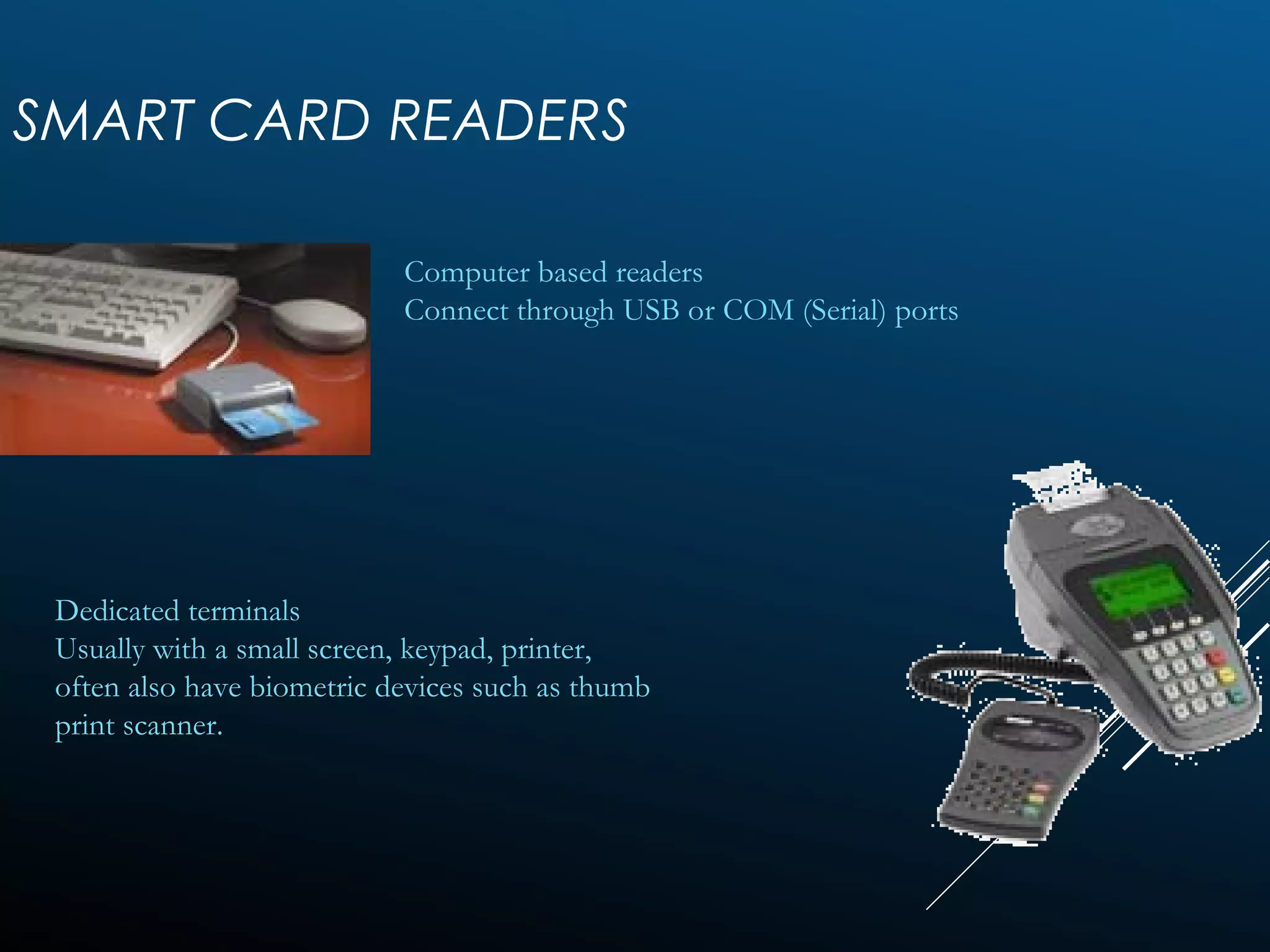
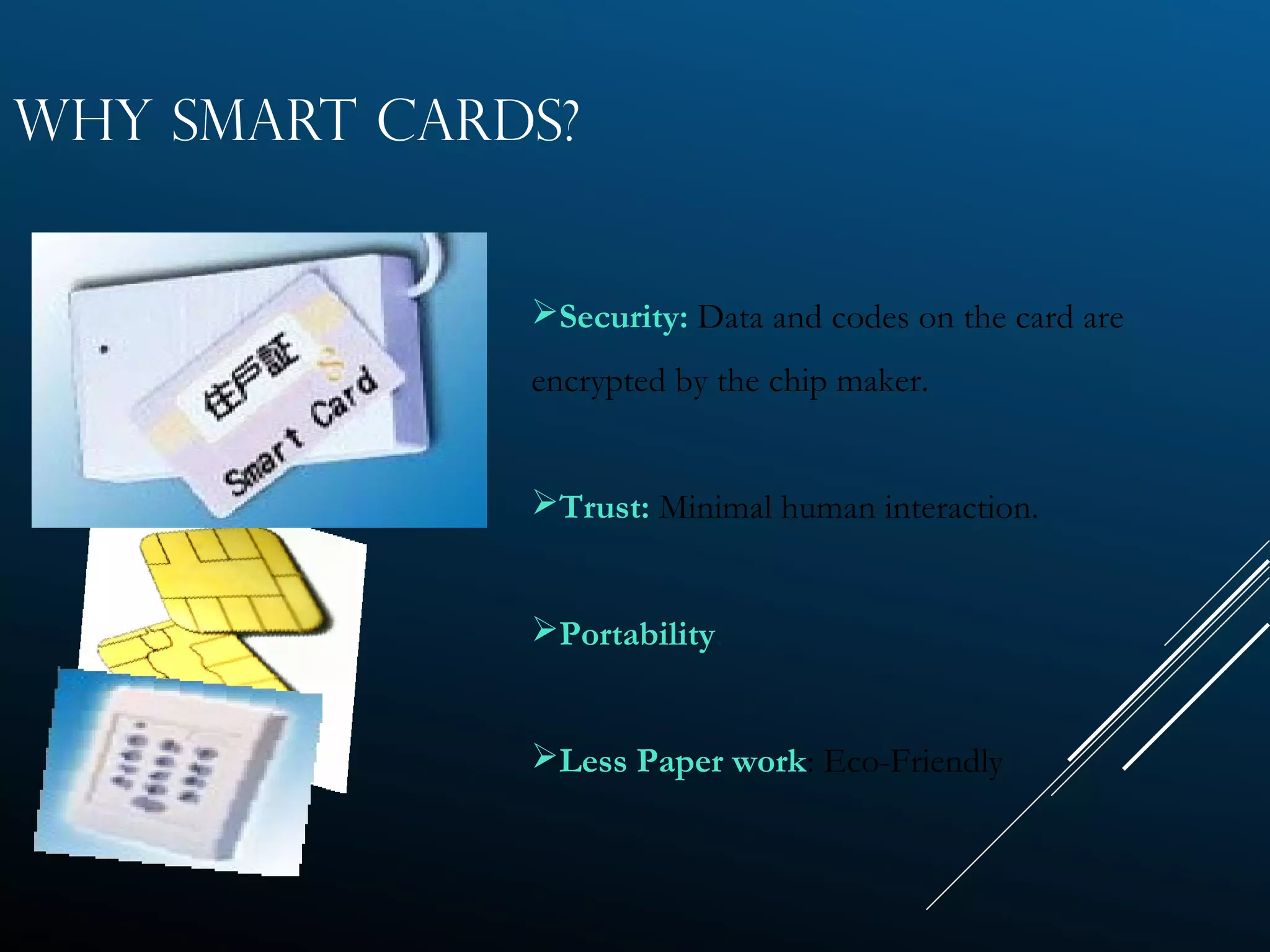
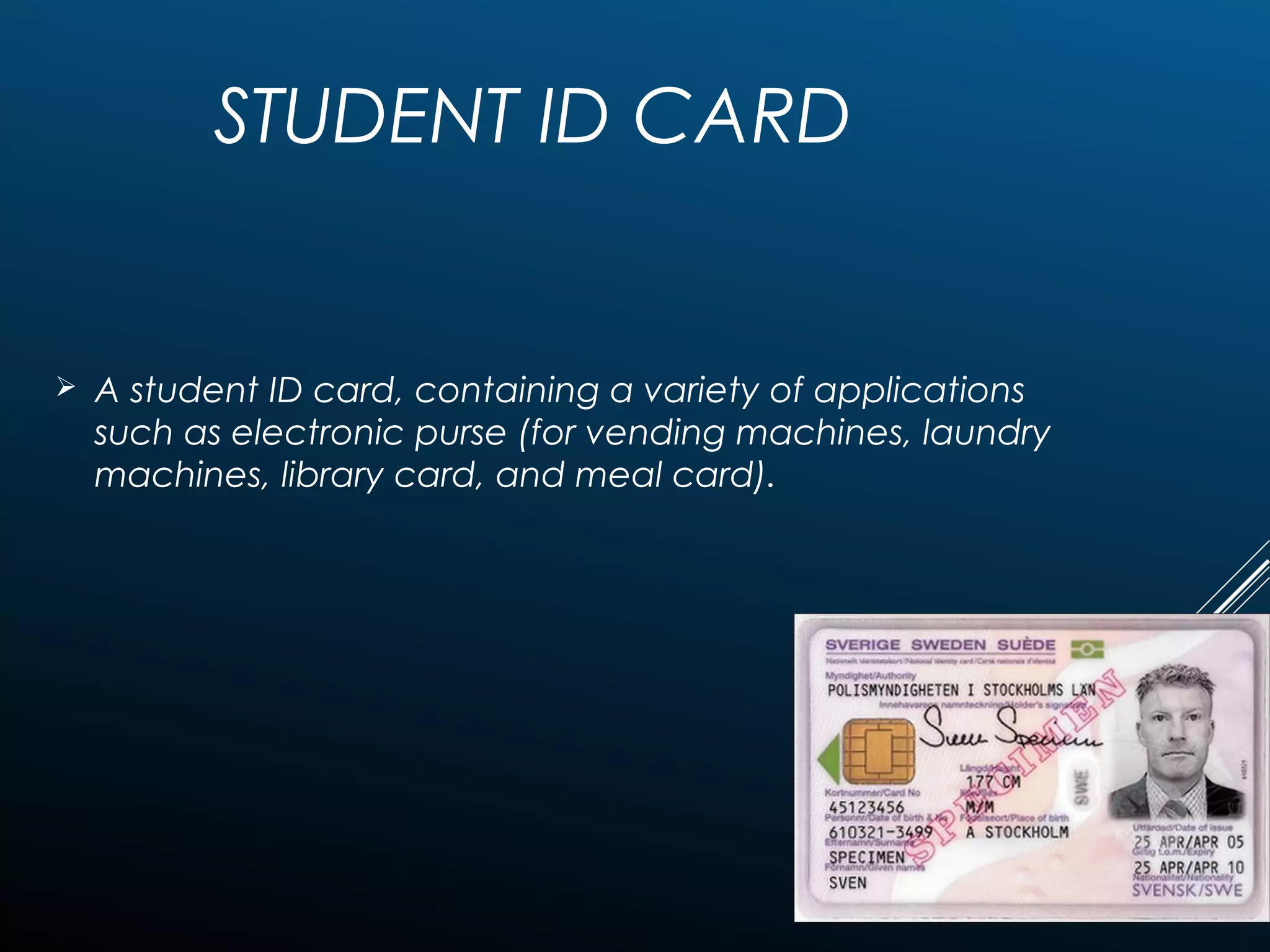
Authentication tokens are used to prove one's identity electronically. They can be hardware or software based, and use passwords, cryptographic keys, or biometric data to authenticate users. Time-synchronized one-time password tokens generate new passwords constantly, while algorithm-based tokens use complex math to generate unguessable one-time passwords. Connected tokens transmit authentication data automatically when connected, while disconnected tokens require manual entry of generated passwords. Smart cards are a type of disconnected token that store and process data using an embedded microchip, providing secure multi-factor authentication through passwords, cryptography, and potentially biometric data.