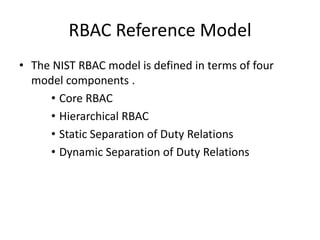
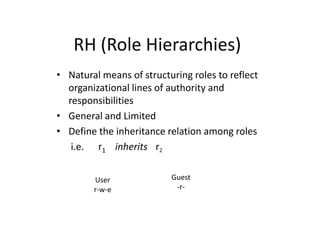
This document discusses role-based access control (RBAC). It defines the core components of RBAC, including users, roles, operations, objects, and permissions. It also describes hierarchical RBAC and how roles can inherit permissions and users from other roles. Finally, it covers separation of duties, both static and dynamic, which place constraints on role assignments to prevent conflicts of interest. RBAC aims to simplify security administration by defining permissions based on roles rather than individual users.



![Role-Based AC
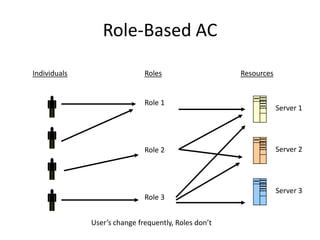
• A user has access to an object based on the assigned role.
• Roles are defined based on job functions.
• Permissions are defined based on job authority and
responsibilities within a job function.
• Operations on an object are invocated based on the
permissions.
• The object is concerned with the user’s role and not the user.
“Ideally, the [RBAC] system is clearly defined
and agile, making the addition of new
applications, roles, and employees as efficient
as possible”](https://image.slidesharecdn.com/rbac6576-121205031439-phpapp01/85/Rbac-7-320.jpg)