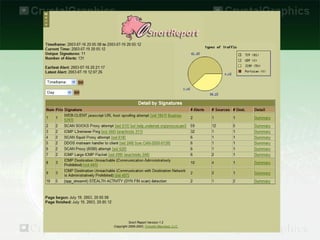
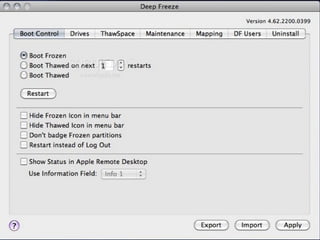
This document discusses network security and introduces several common network security tools. It begins by defining network security and explaining the importance of securing a network. It then profiles six security tools: Snort is an open-source network intrusion detection and prevention system that can detect attacks and probes. Ettercap is used for network protocol analysis and can intercept traffic, capture passwords, and conduct eavesdropping. Sam Spade is a network tool suite that finds public information about IP and DNS addresses. BackTrack is a Linux distribution focused on penetration testing. Hydra performs rapid dictionary attacks against network protocols. Deep Freeze makes computer configurations indestructible by wiping out any changes made during a session.