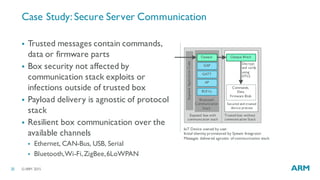
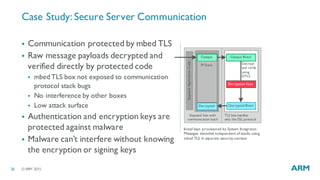
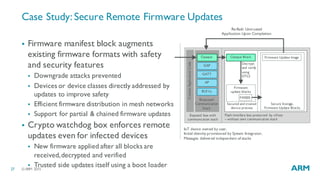
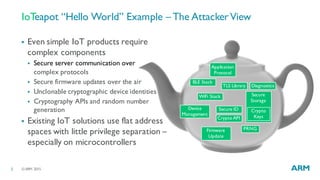
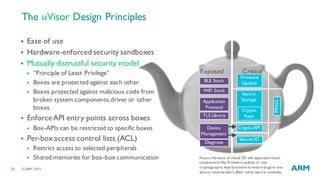
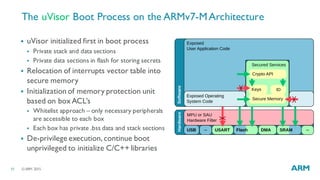
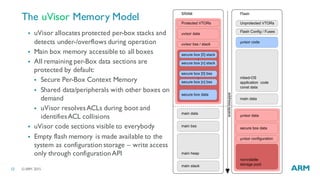
The document discusses the vulnerabilities in traditional flat security models for Internet of Things (IoT) devices and proposes a more resilient approach using the uvisor framework to create secure, isolated code compartments. It highlights the importance of dynamic security, remote recovery, and updates to combat potential attacks, while ensuring efficient communication and firmware management. The document also details architectural principles and case studies demonstrating secure server communication and malware recovery strategies.





![©ARM 201514
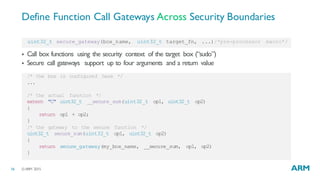
Enable uVisor and Share Peripherals Across Boxes
#include <uvisor-lib/uvisor-lib.h>
/* create background ACLs for the main box */
static const UvBoxAclItem g_background_acl[] = {
{UART0, sizeof(*UART0), UVISOR_TACL_PERIPHERAL},
{UART1, sizeof(*UART1), UVISOR_TACL_PERIPHERAL},
{PIT, sizeof(*PIT), UVISOR_TACL_PERIPHERAL},
};
/* set uvisor mode (enable) */
UVISOR_SET_MODE_ACL(UVISOR_ENABLED, g_background_acl);
#include <uvisor-lib/uvisor-lib.h>
/* set uvisor mode (enable) */
UVISOR_SET_MODE(UVISOR_ENABLED);
§ enable uVisor – optionally with shared peripherals across boxes:](https://image.slidesharecdn.com/resilientiotsecuritytheendofflatsecuritymodels-151119152041-lva1-app6892/85/Resilient-IoT-Security-The-end-of-flat-security-models-14-320.jpg)
![©ARM 201515
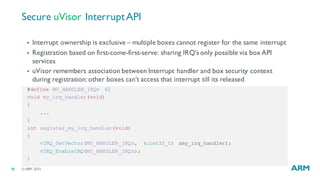
Setting up Protected Sandboxes
/* create private box context */
typedef struct {
uint8_t secret[SECRET_SIZE];
bool initialized;
} BoxContext;
/* create ACLs for the module */
static const UvBoxAclItem g_box_acl[] = {
{RNG, sizeof(*RNG), UVISOR_TACL_PERIPHERAL}, /* a peripheral */
};
/*required stack size */
#define BOX_STACK_SIZE 0x100
/* configure secure box compartment */
UVISOR_BOX_CONFIG(my_box_name, g_box_acl, BOX_STACK_SIZE, BoxContext);](https://image.slidesharecdn.com/resilientiotsecuritytheendofflatsecuritymodels-151119152041-lva1-app6892/85/Resilient-IoT-Security-The-end-of-flat-security-models-15-320.jpg)