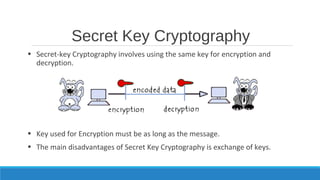
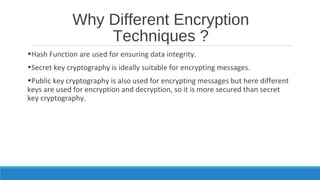
Cryptography is the practice of hiding information and involves techniques like secret key cryptography, public key cryptography, and hash functions. New trends in cryptography include elliptic curve cryptography, which uses points on elliptic curves to securely exchange keys, quantum cryptography which uses quantum effects for secure communication, and pairing based cryptography which pairs elements of groups to construct hybrid cryptosystems. The document discusses different encryption techniques, their drawbacks, and the need for new techniques that are more secure against attacks.