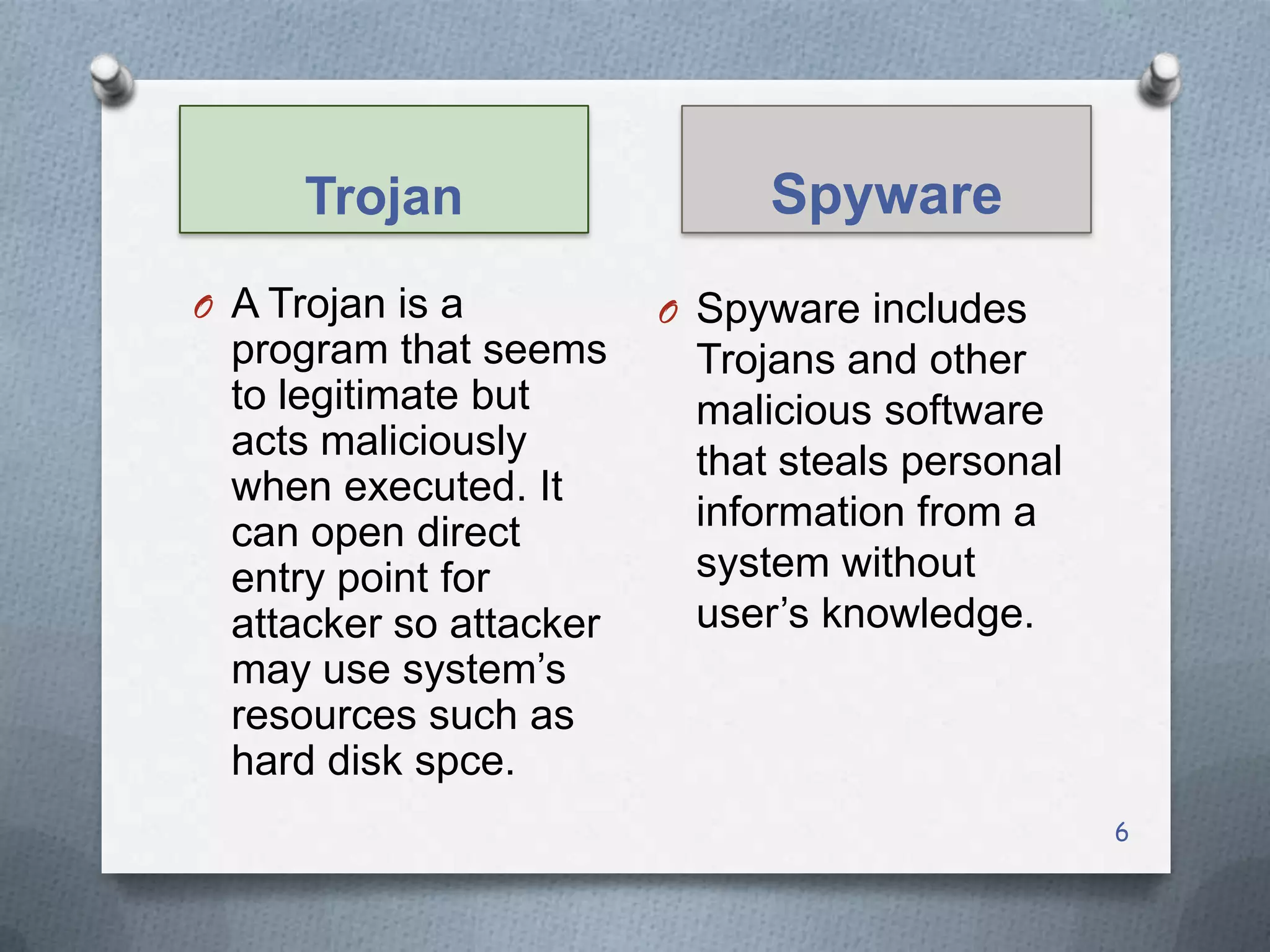
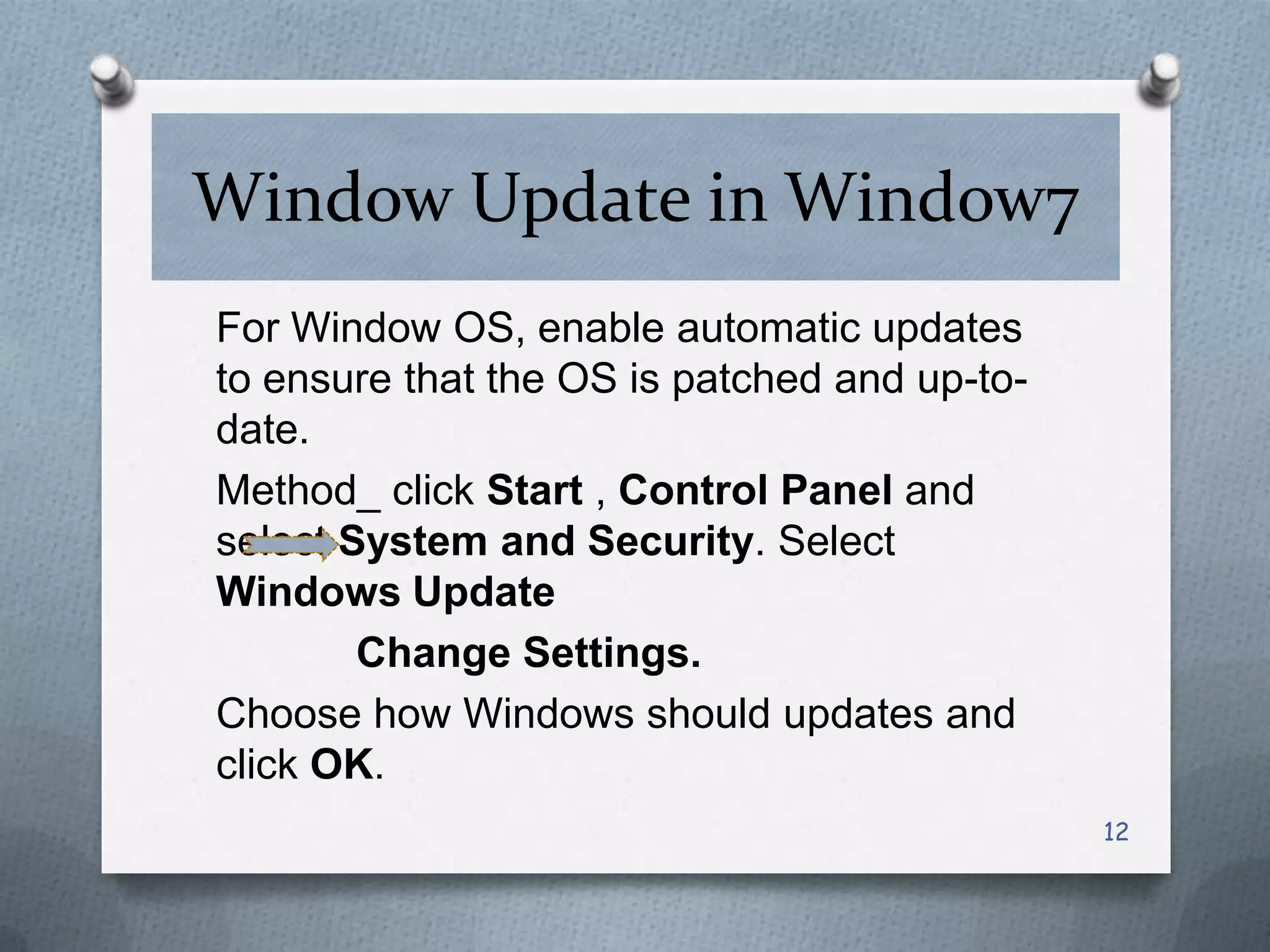
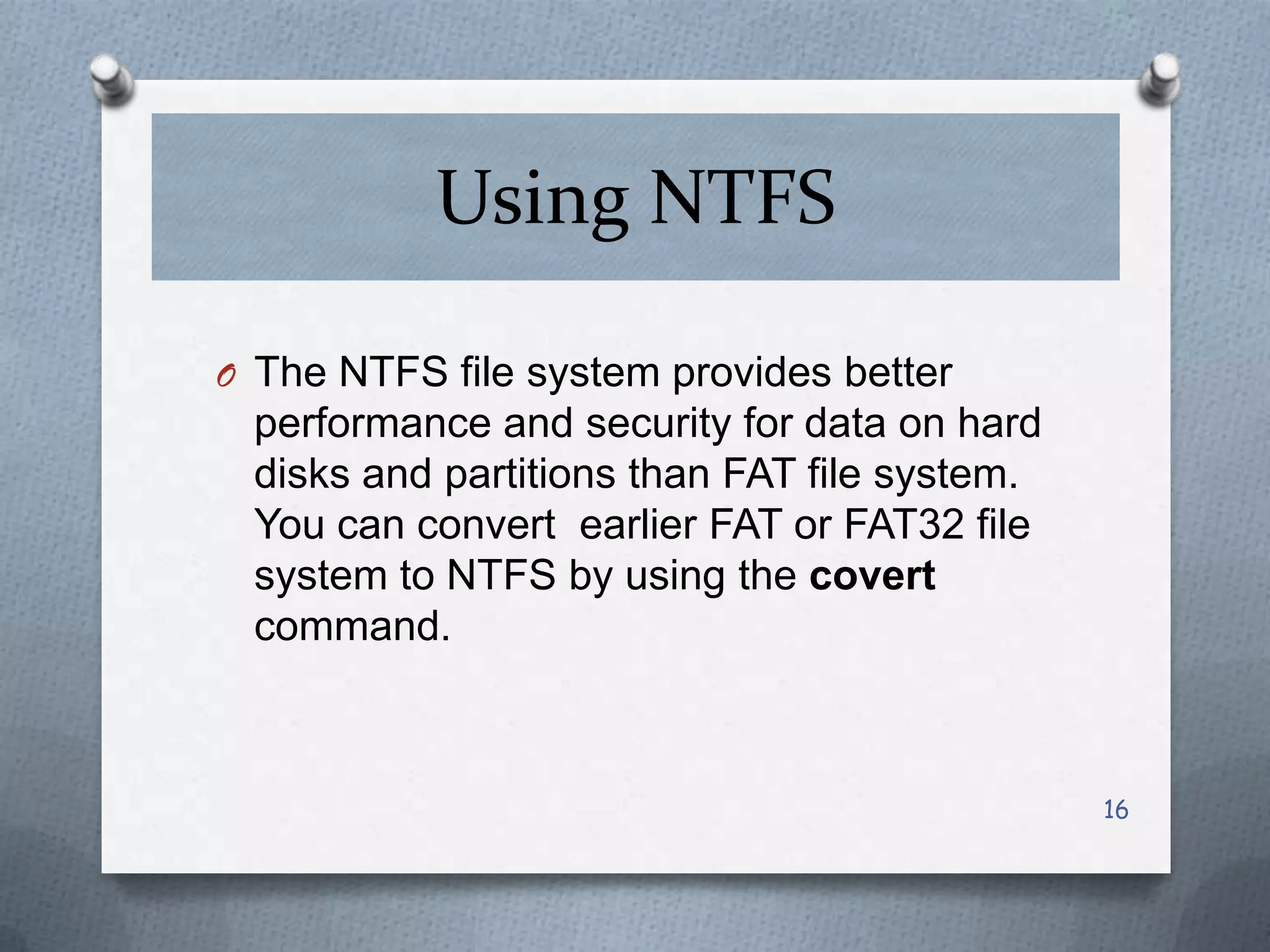
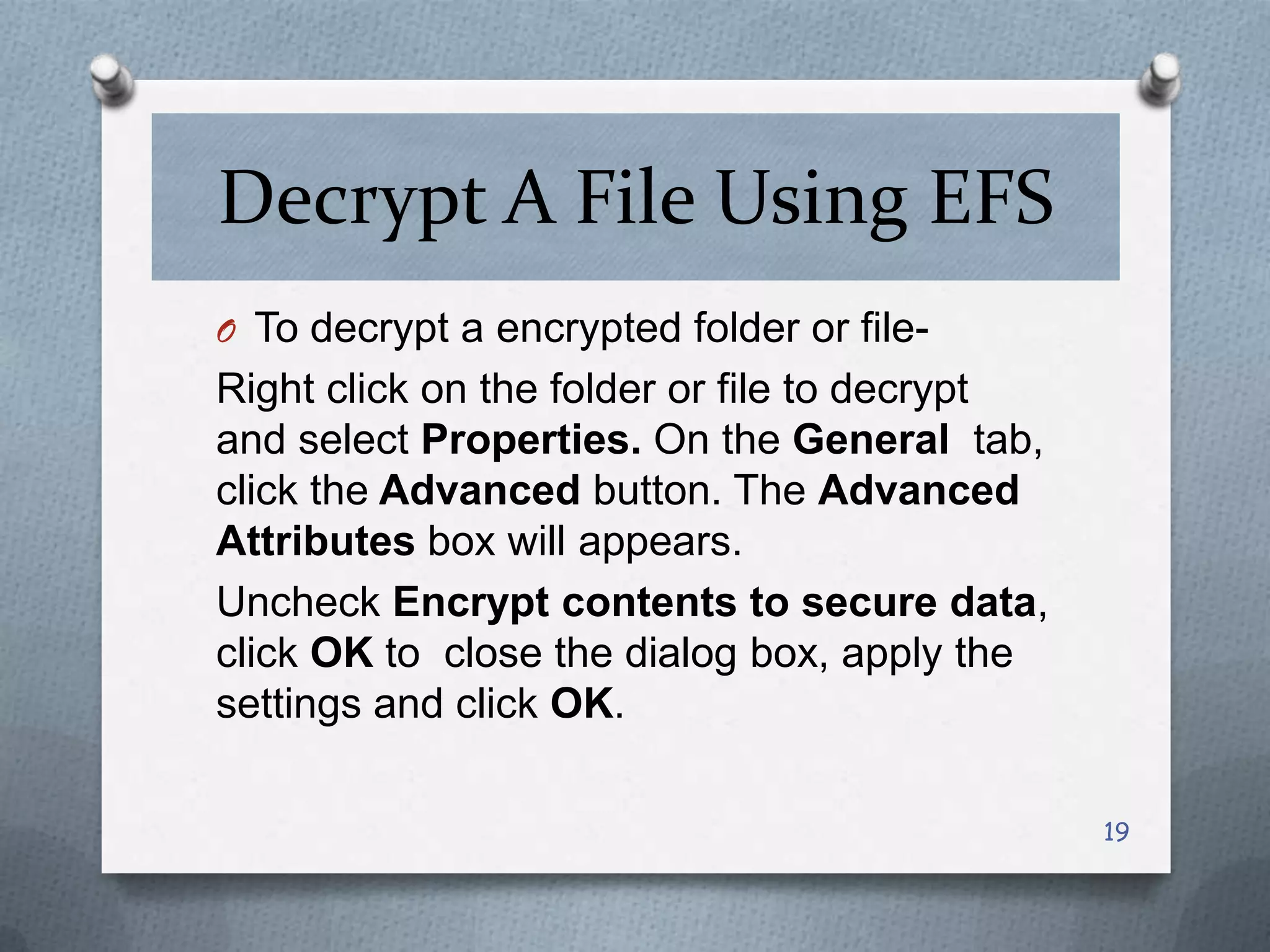
This document discusses various threats to computer system security and methods to protect Windows operating systems. It describes viruses, Trojans, spyware and techniques like password cracking that pose security risks. It then provides guidelines for securing Windows, such as enabling the firewall, configuring strong passwords, and keeping the system updated. Methods are outlined for features like BitLocker encryption and NTFS formatting to enhance security. Overall the document aims to raise awareness of cyber threats and share best practices for protecting Windows computers.