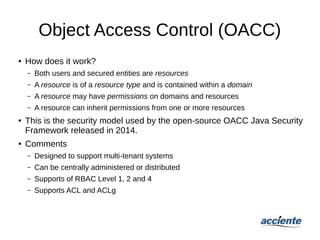
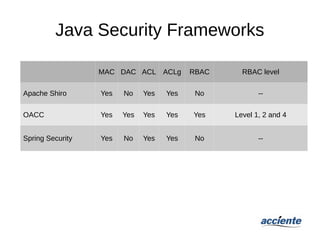
The document provides an overview of application security authorization models, detailing various historical contexts and frameworks such as mandatory access control (MAC), discretionary access control (DAC), role-based access control (RBAC), attribute-based access control (ABAC), and object access control (OACC). It distinguishes between authorization and authentication, explaining how different models grant or deny user access to resources. The document emphasizes the operational mechanisms and applications of these models, as well as their pros and cons in managing user permissions.