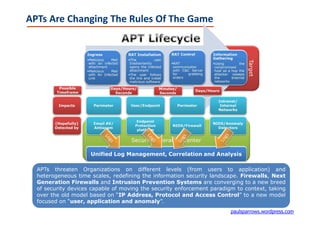
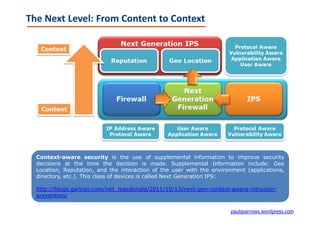
The document discusses the evolution of security technologies, emphasizing the need to transition from content-based security models to context-aware systems due to the increasing sophistication of malware and advanced persistent threats (APTs). It highlights the role of next-generation intrusion prevention systems (NG-IPS) and web application firewalls (WAFs) in defending against contemporary cyber threats, while also pointing out the importance of addressing human vulnerabilities as a primary focus in cybersecurity. The document concludes with references to previous writings on security advancements and the significance of adapting to a changing threat landscape.