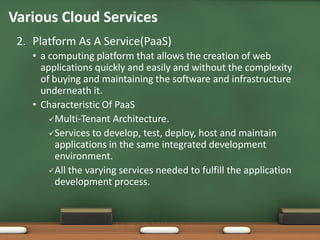
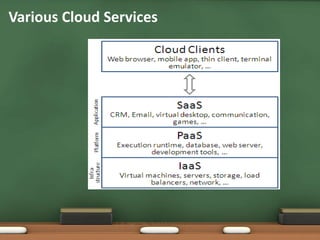
This document discusses security as a service (SECaaS) in cloud computing. It begins by explaining other common cloud service models like SaaS, PaaS, IaaS, and STaaS. It then defines SECaaS as a business model where large service providers integrate security services like authentication, antivirus, intrusion detection, and security event management into a corporate infrastructure on a subscription basis. The document lists the top 10 cloud service providers and reasons why cloud-based security is required. It outlines common areas covered by SECaaS like identity and access management, data loss prevention, and network security. Finally, it provides examples of specific SECaaS products and services offered by vendors.