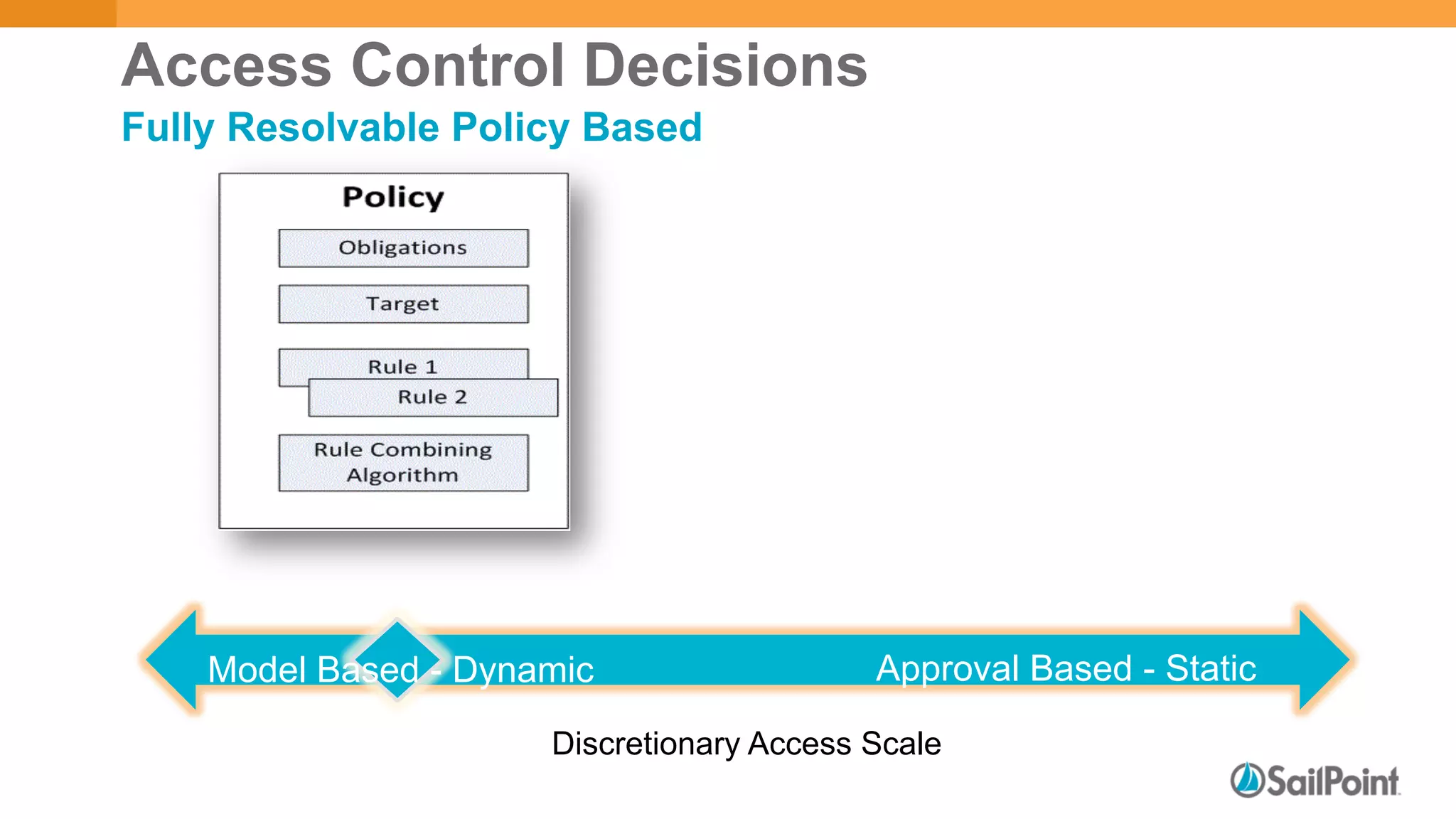
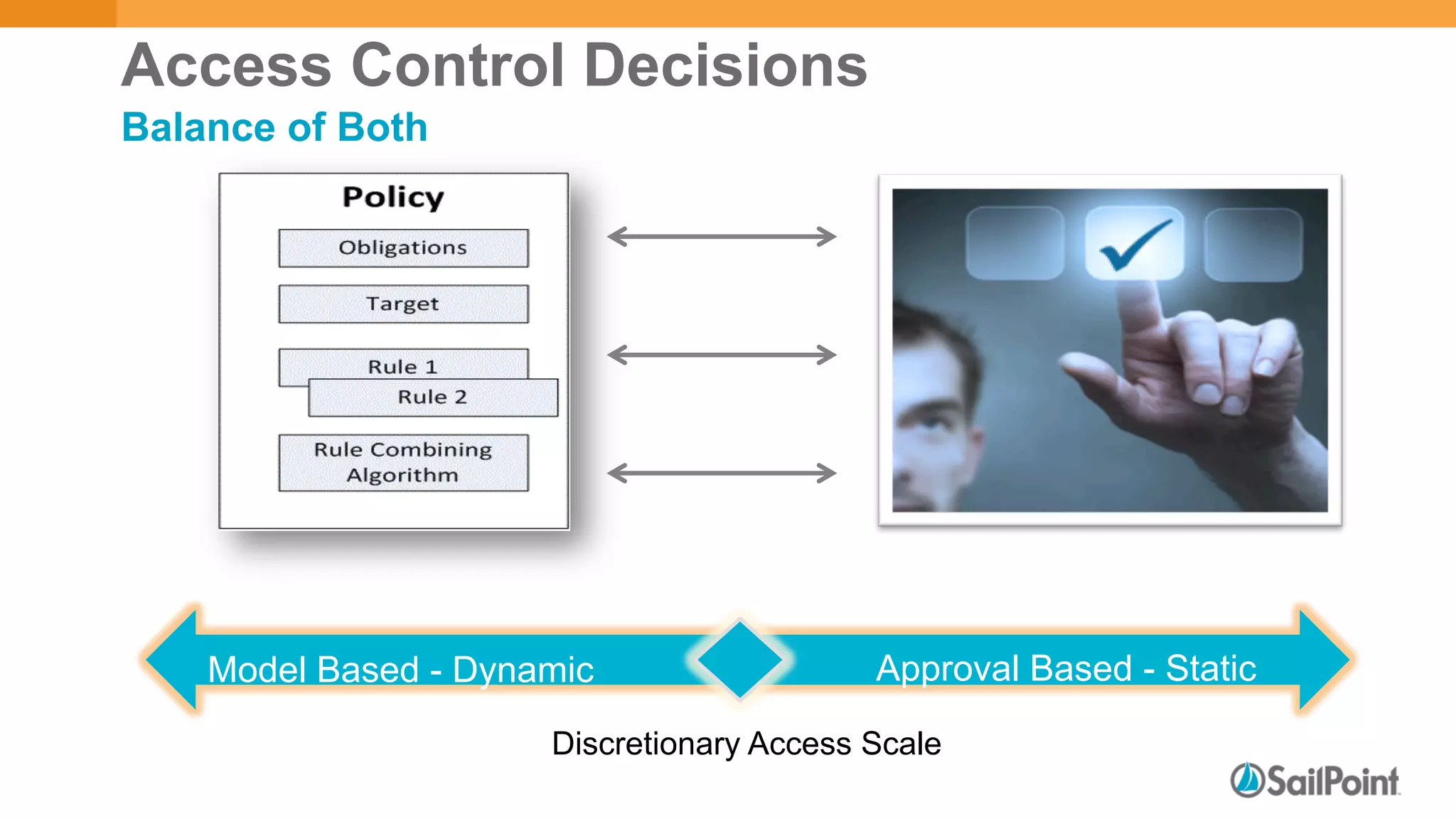
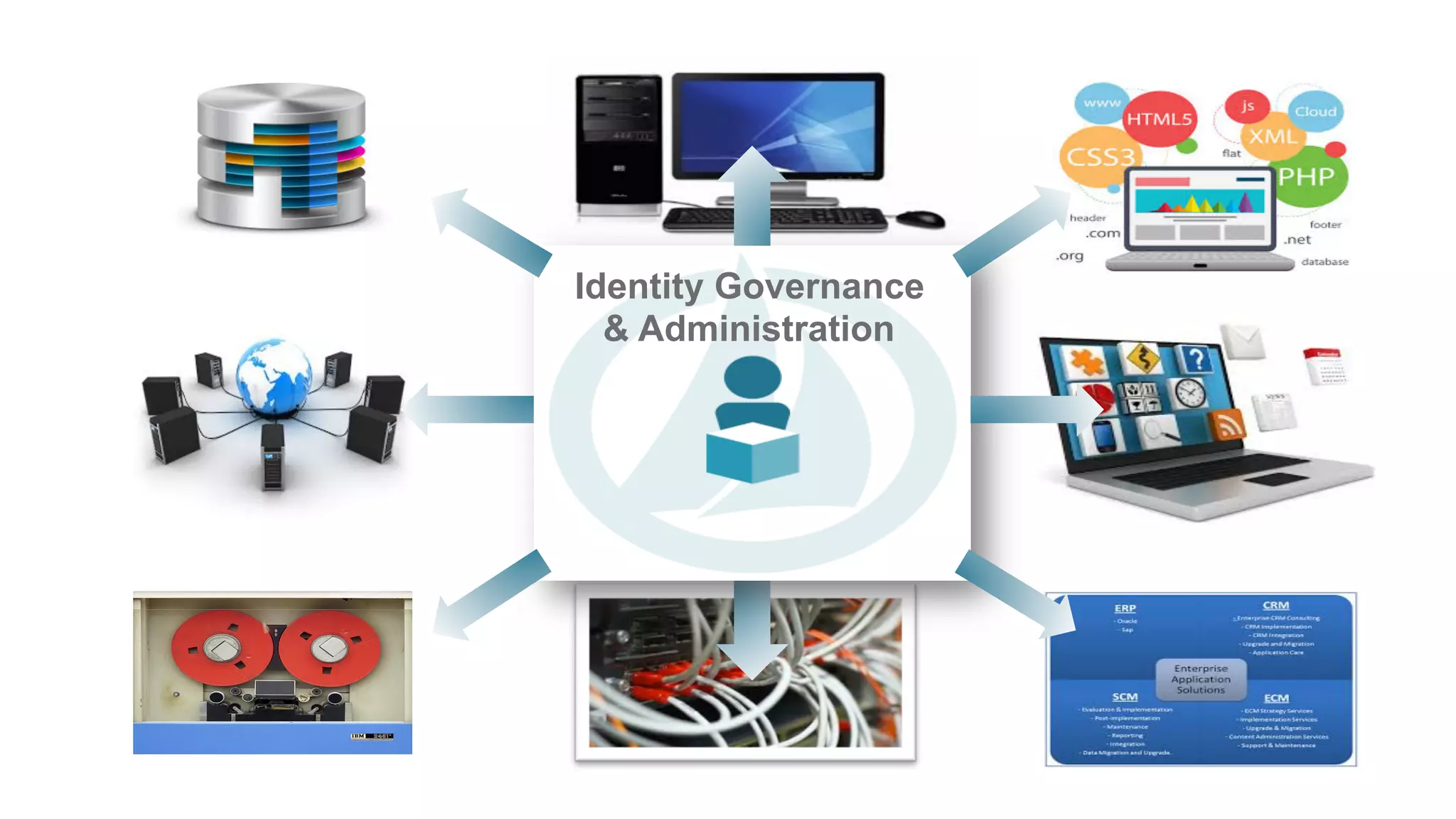
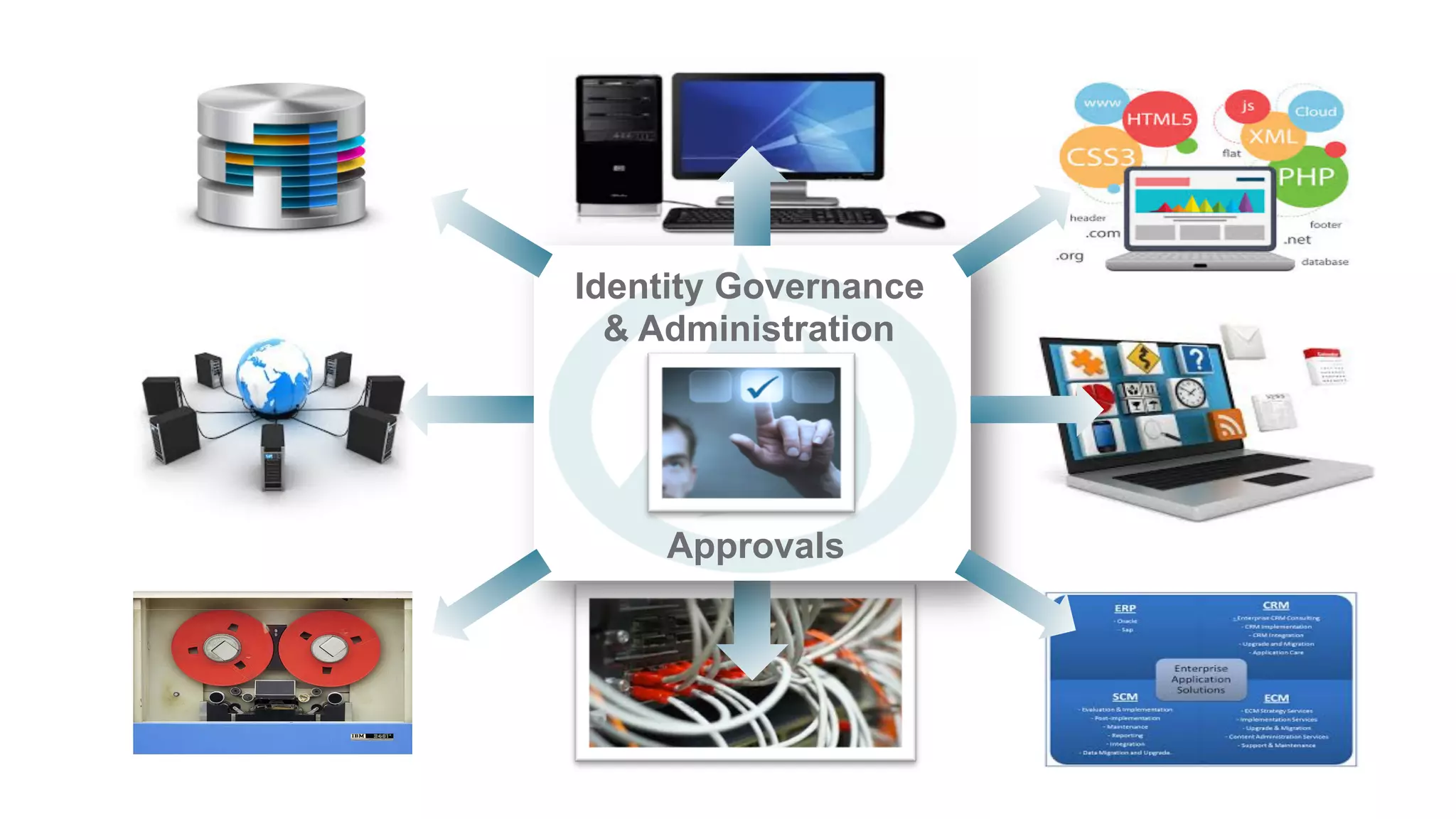
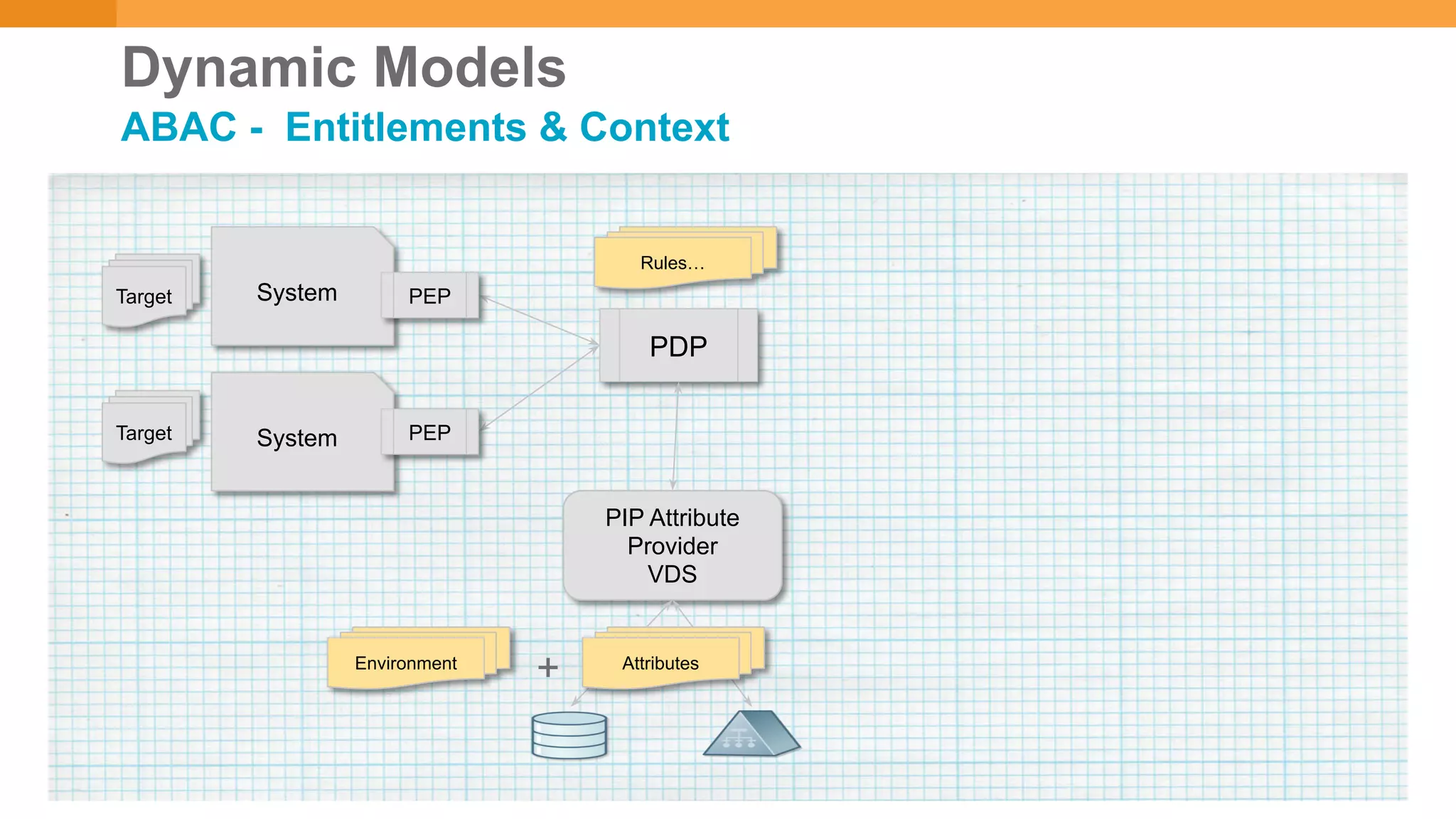
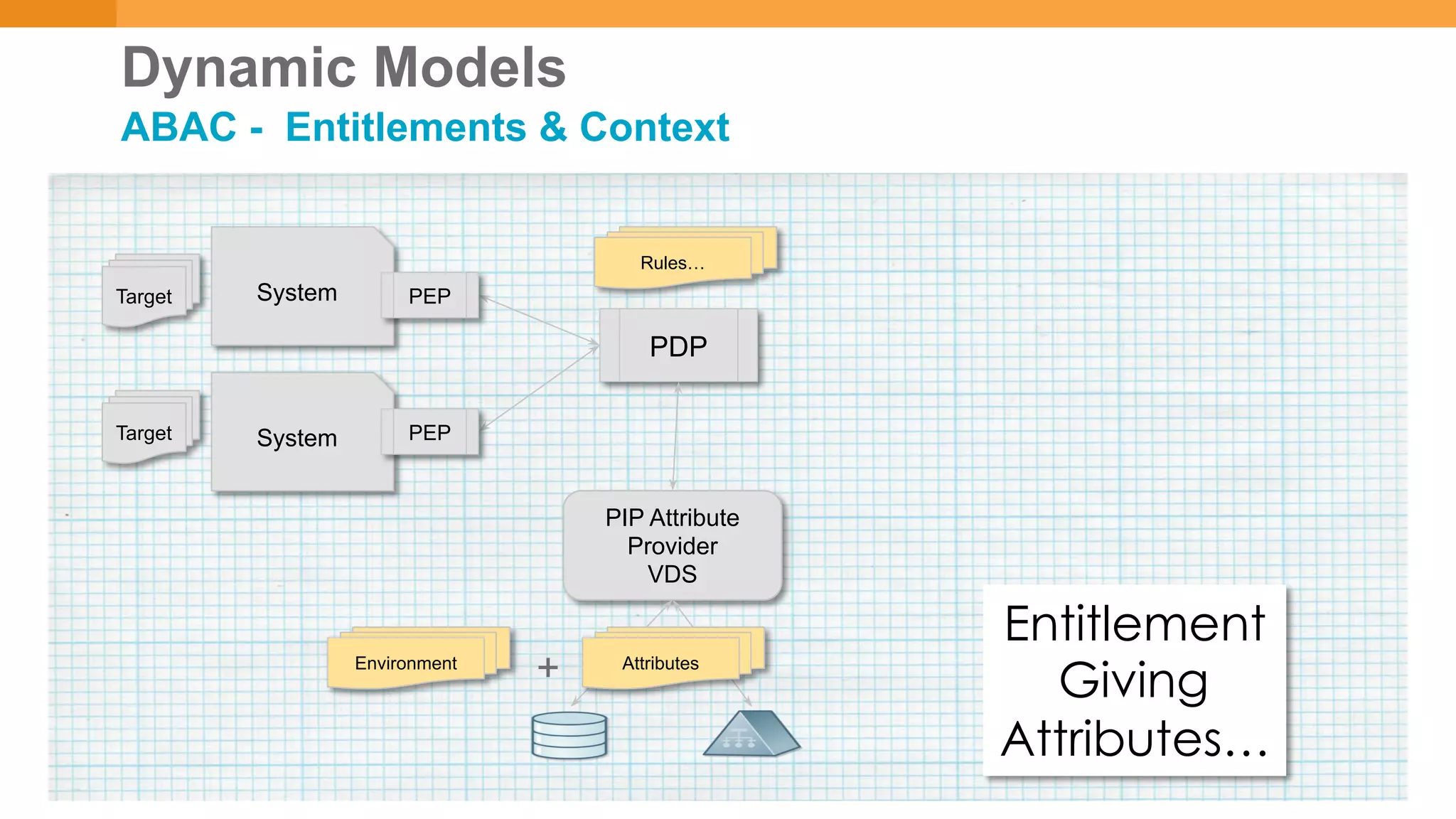
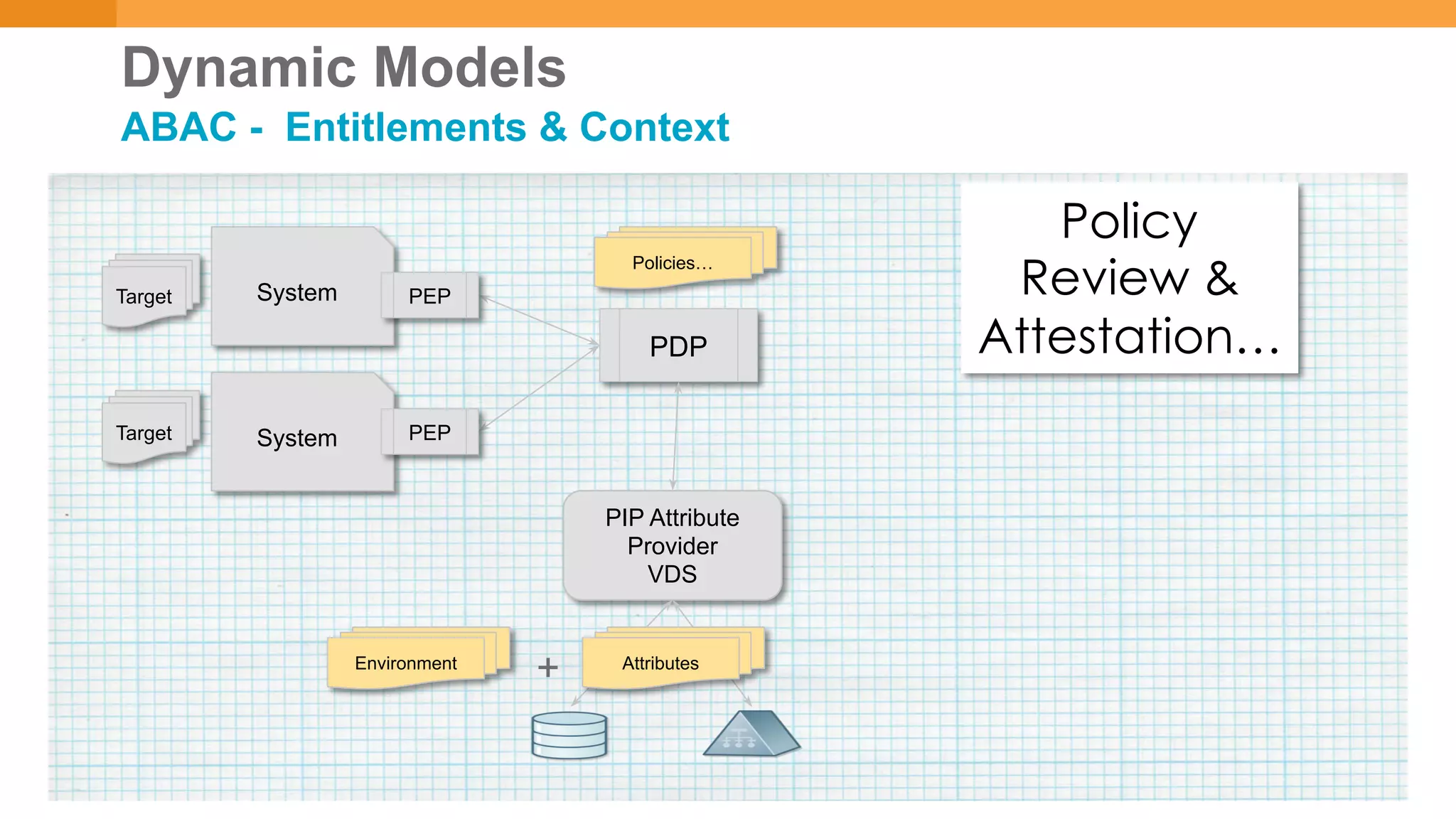
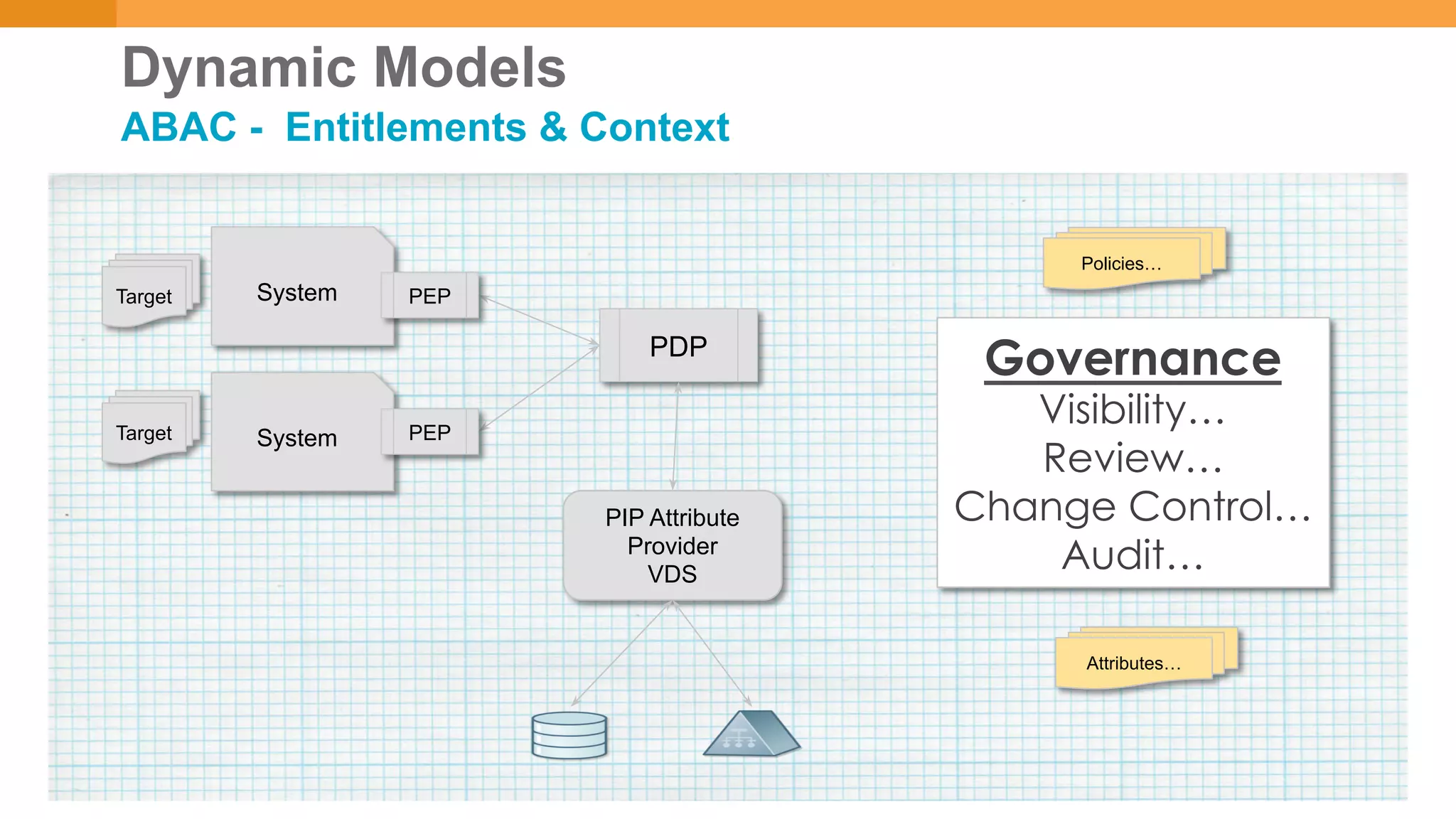
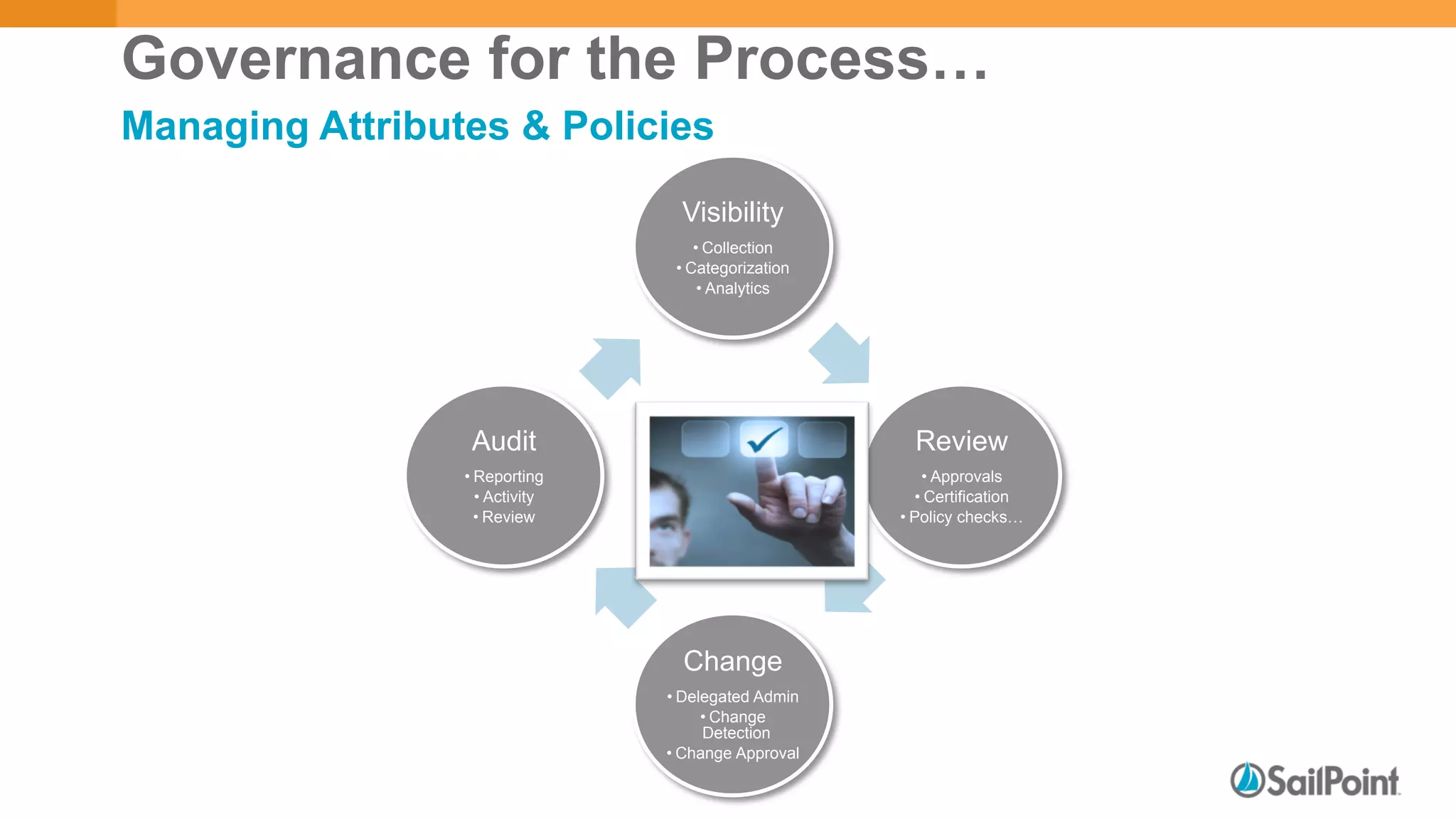
The document discusses discretionary access management, outlining its definition, application, and varying models such as static, dynamic, and blended approaches. It highlights best practices in managing authorization and the importance of governance in access control systems. Additionally, it emphasizes attributes and policies' role in ensuring effective entitlement management.