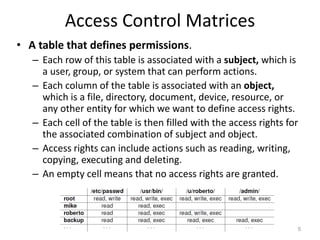
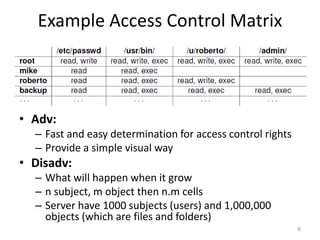
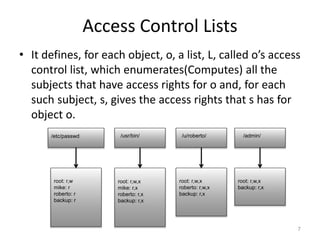
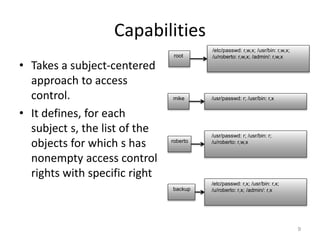
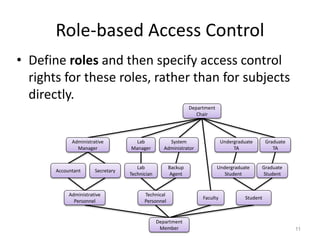
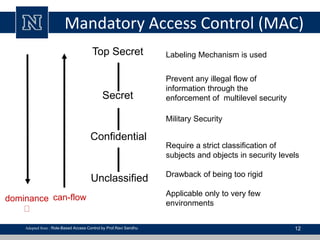
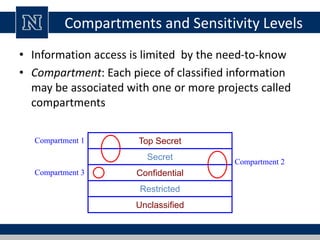
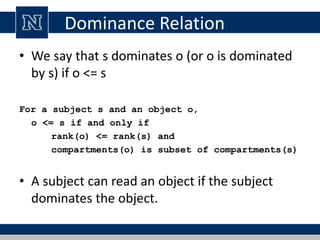
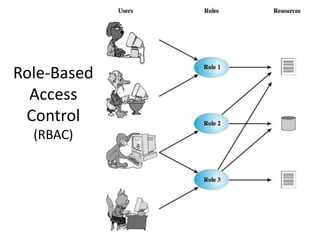
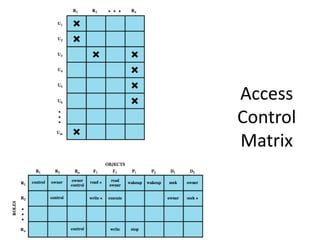
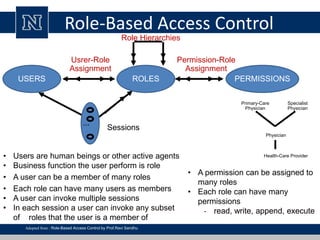
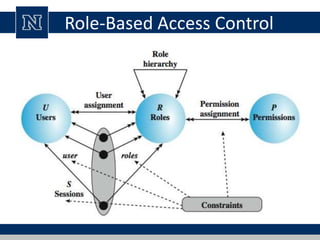
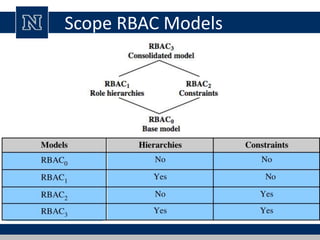
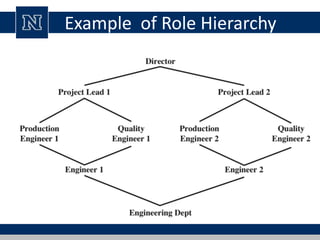
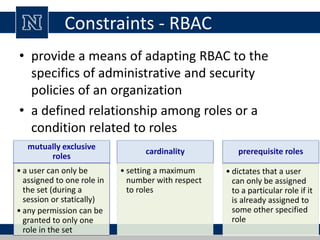
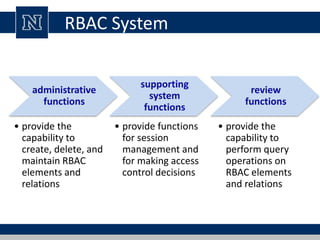
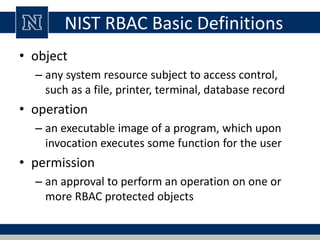
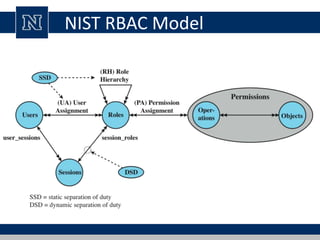
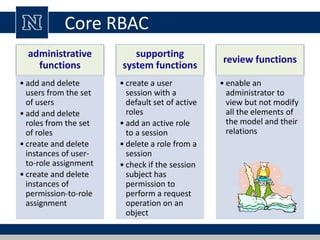
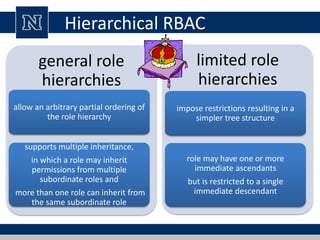
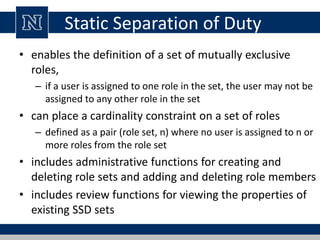
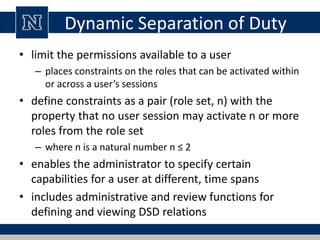
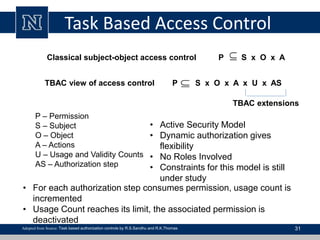
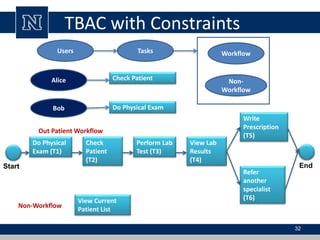
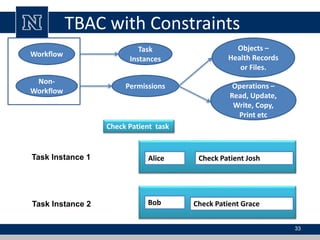
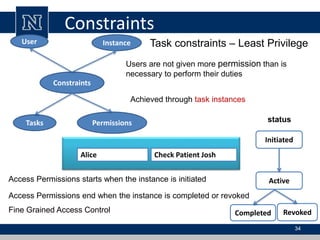
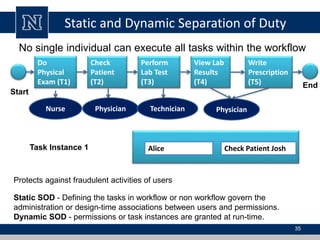
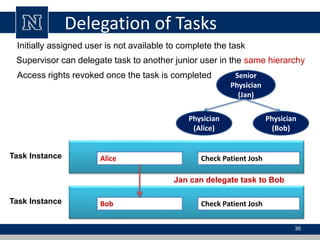
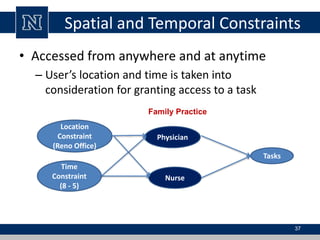
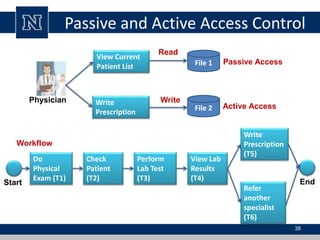
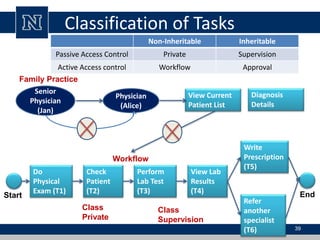
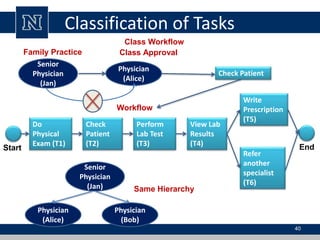
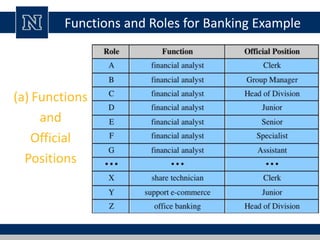
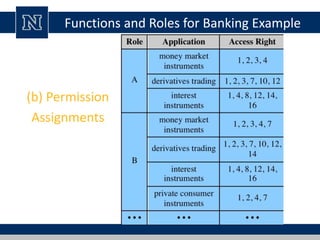
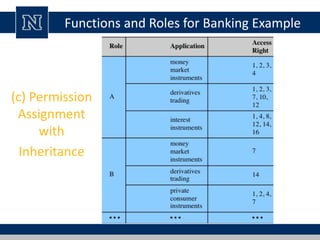
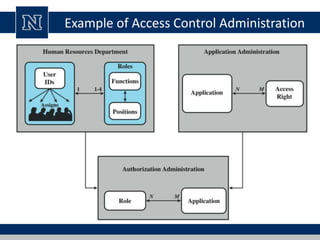
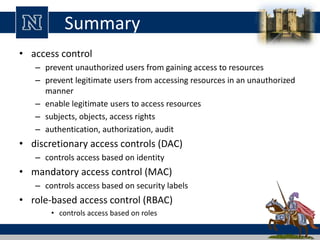
This document discusses various access control models and concepts. It begins by defining access control as the prevention of unauthorized use of resources, controlling who can access a resource, under what conditions, and what they are allowed to do. It then covers different access control models and concepts in detail including access control matrices, access control lists, capabilities, role-based access control (RBAC), mandatory access control (MAC), and separation of duty constraints. RBAC is described as defining roles and associated permissions rather than assigning permissions directly to users. Hierarchical and static/dynamic separation of duty extensions to the core RBAC model are also summarized.