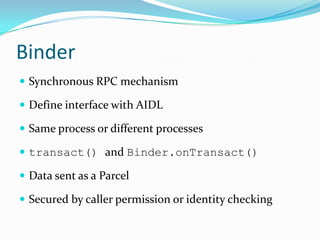
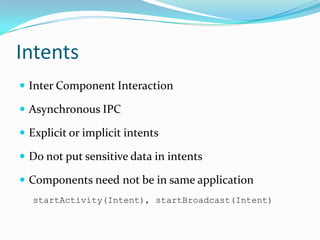
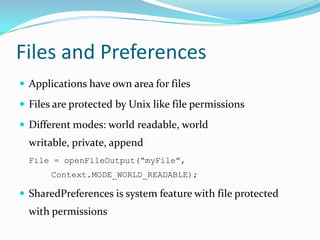
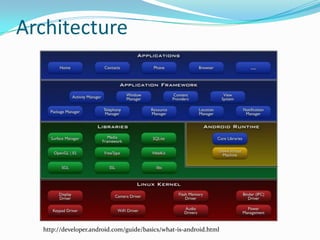
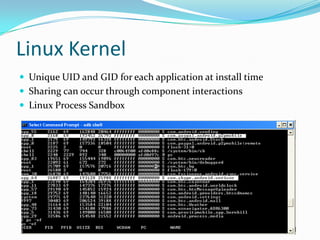
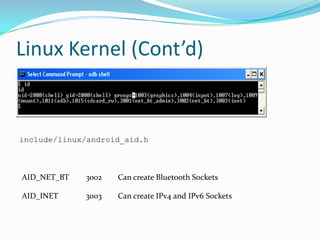
The document provides a comprehensive overview of the Android security model, detailing its architecture, permissions, and components involved in app security. It emphasizes the importance of understanding Android security for developers, covering concepts like application signing, intent management, and external storage encryption. Additionally, it outlines best practices for securing sensitive data and permissions through the AndroidManifest.xml file.












![Content ProviderAllow applications to share dataDefine permissions for accessing <provider>Content providers use URI schemsContent://<authority>/<table>/[<id>]](https://image.slidesharecdn.com/understandingandroidsecuritymodel-110304193331-phpapp01/85/Understanding-android-security-model-16-320.jpg)