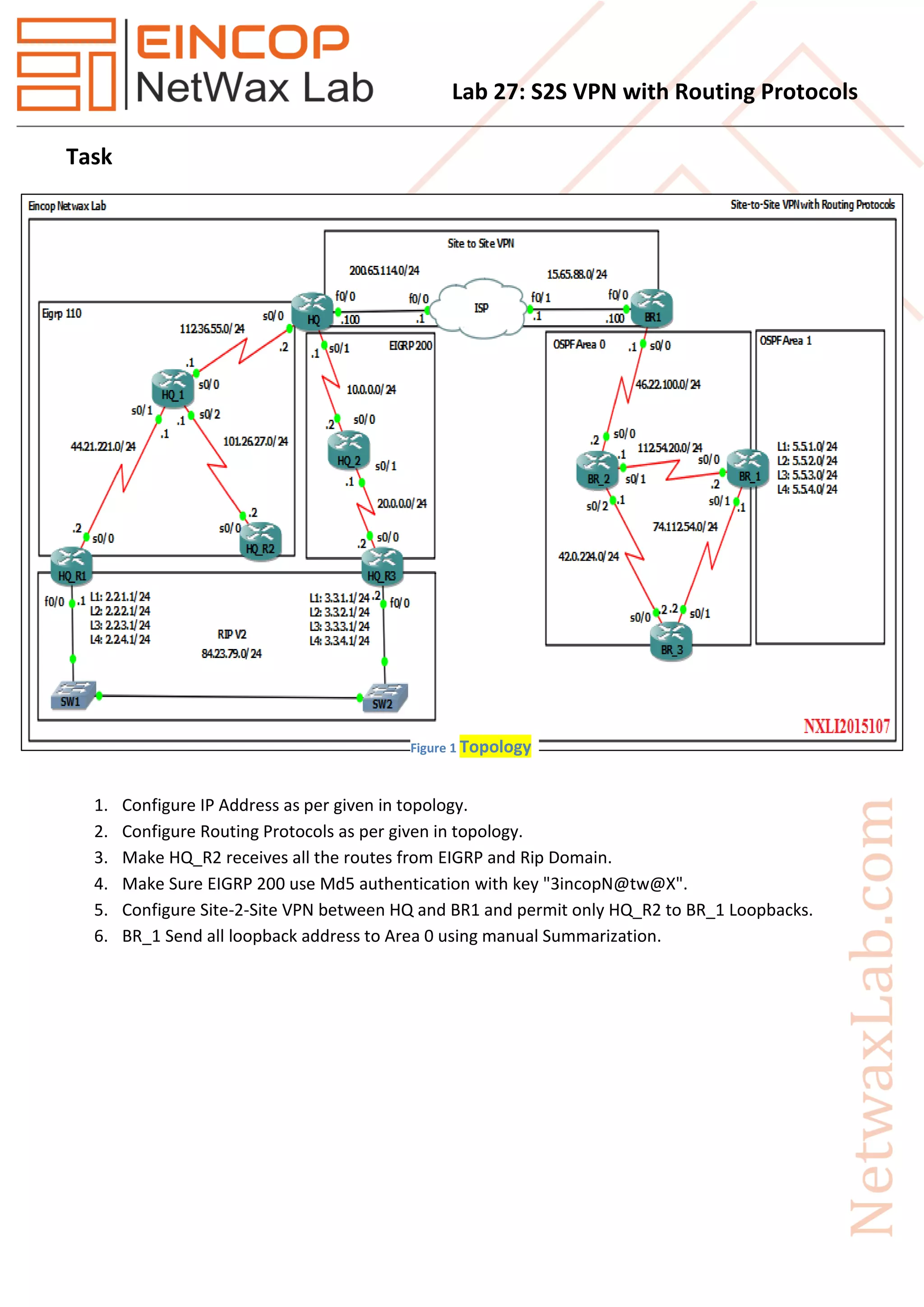
This document provides instructions for configuring routing protocols and a site-to-site VPN between HQ and BR1 networks. The tasks include: 1) configuring EIGRP and RIP routing with redistribution to ensure HQ_R2 learns all routes, 2) enabling MD5 authentication on EIGRP 200, 3) establishing an IPsec VPN between HQ and BR1 to permit access only to BR1 loopback addresses from HQ_R2, and 4) summarizing the BR1 loopback routes into OSPF area 0 on BR1.