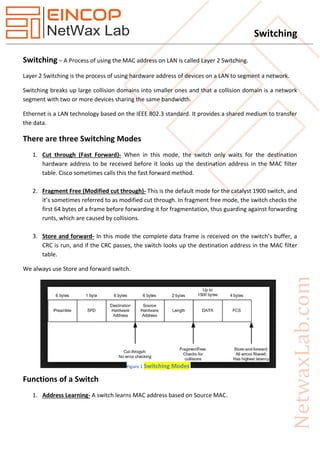
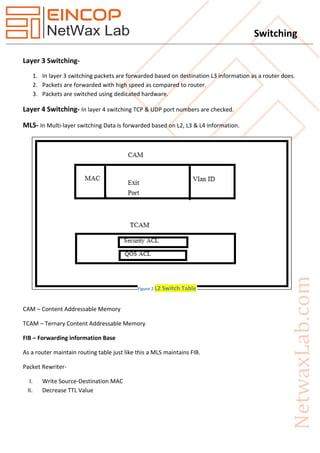
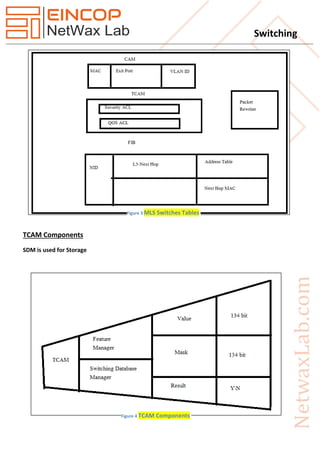
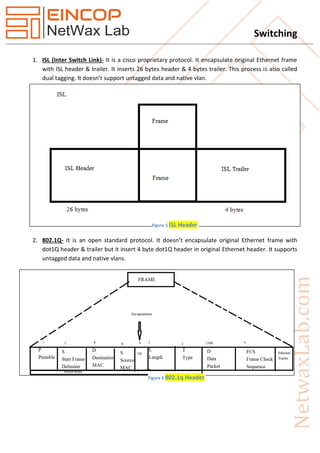
This document provides a comprehensive overview of switching, specifically focusing on Layer 2 switching, types of switches, and VLAN configurations. It describes the mechanics of different switching modes, such as cut-through and store-and-forward, as well as VLAN trunking protocols like ISL and 802.1Q. Additionally, it covers the roles of various protocols and systems in managing MAC address tables and VLAN configurations.