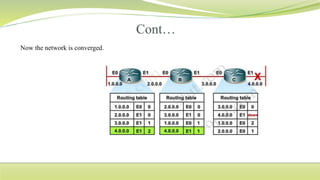
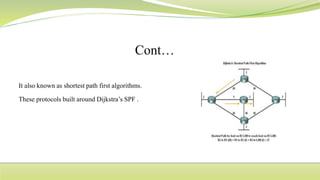
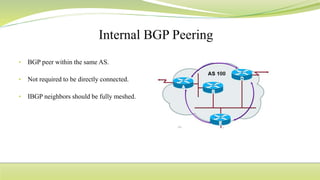
The document provides a comprehensive overview of routing protocols, including static and dynamic routing, their advantages and disadvantages, and various types of routing algorithms used in networks. It discusses important protocols such as RIP, EIGRP, OSPF, BGP, and details related concepts like MANET, address resolution, and routing tables. The text highlights how routing is essential for pathfinding in networks, the importance of metrics, and the significance of administrative distance in routing processes.