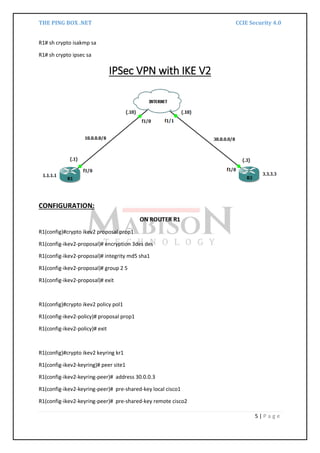
An IPSec VPN is configured between routers R1 and R2 using RSA signatures for authentication. NTP and a CA server are also configured to synchronize time and authenticate certificates between the routers. IKEv2 is then used to configure an IPSec VPN between routers R1 and R3 using pre-shared keys for authentication.