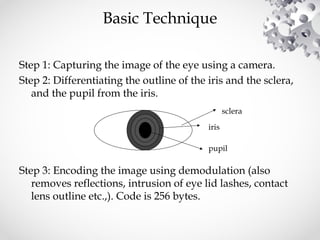
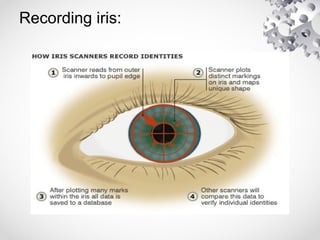
The document summarizes iris recognition as a biometric authentication method. It discusses how the iris is unique and stable over time, making it suitable for identification. The basic technique involves capturing an eye image, localizing the iris, and encoding patterns in the iris to generate a code for matching. Advantages include speed, accuracy and the iris being difficult to forge. Current applications include smartphone unlocking and border security. Future uses could help identify patients in hospitals and provide officer safety during traffic stops.