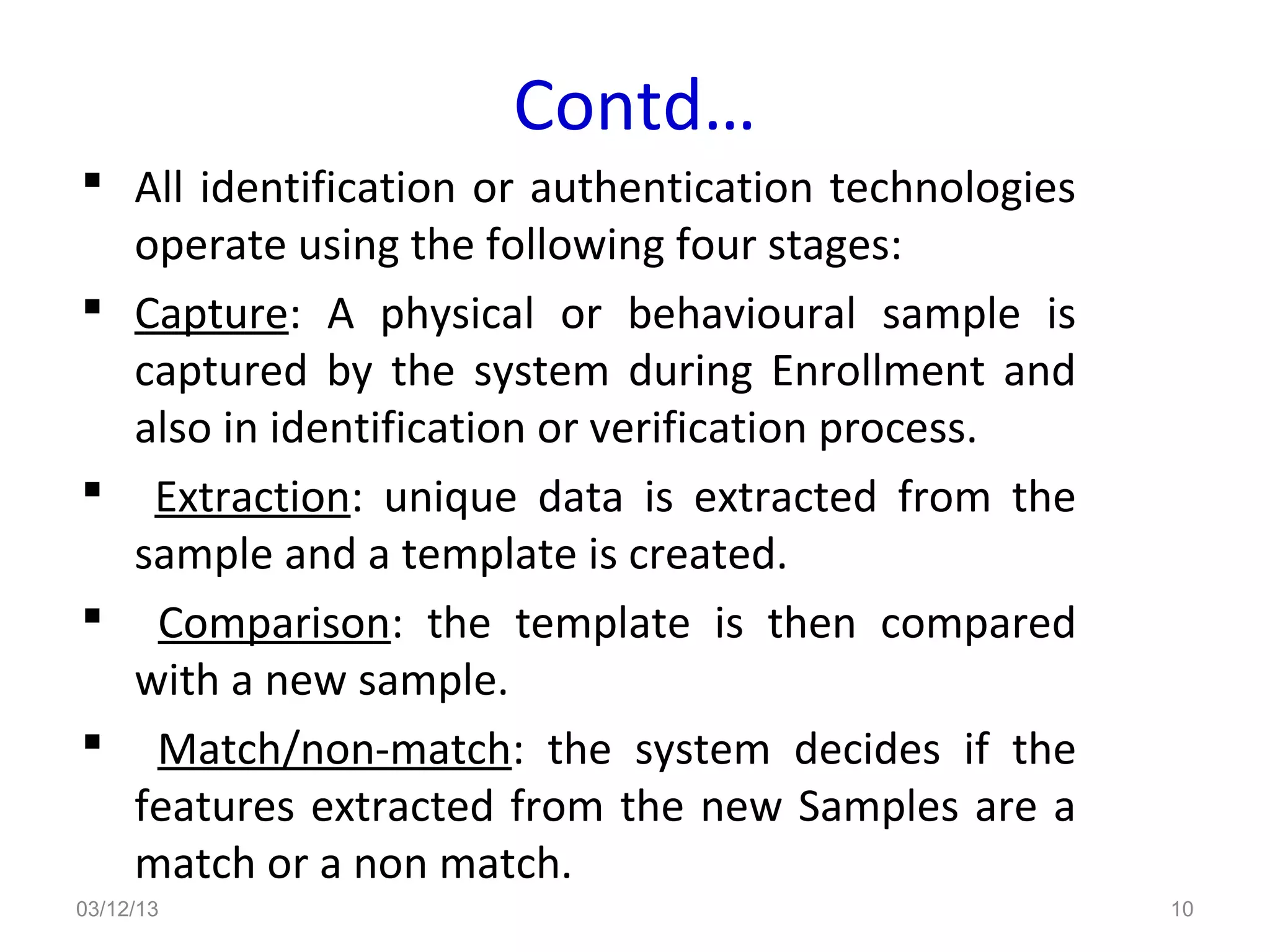
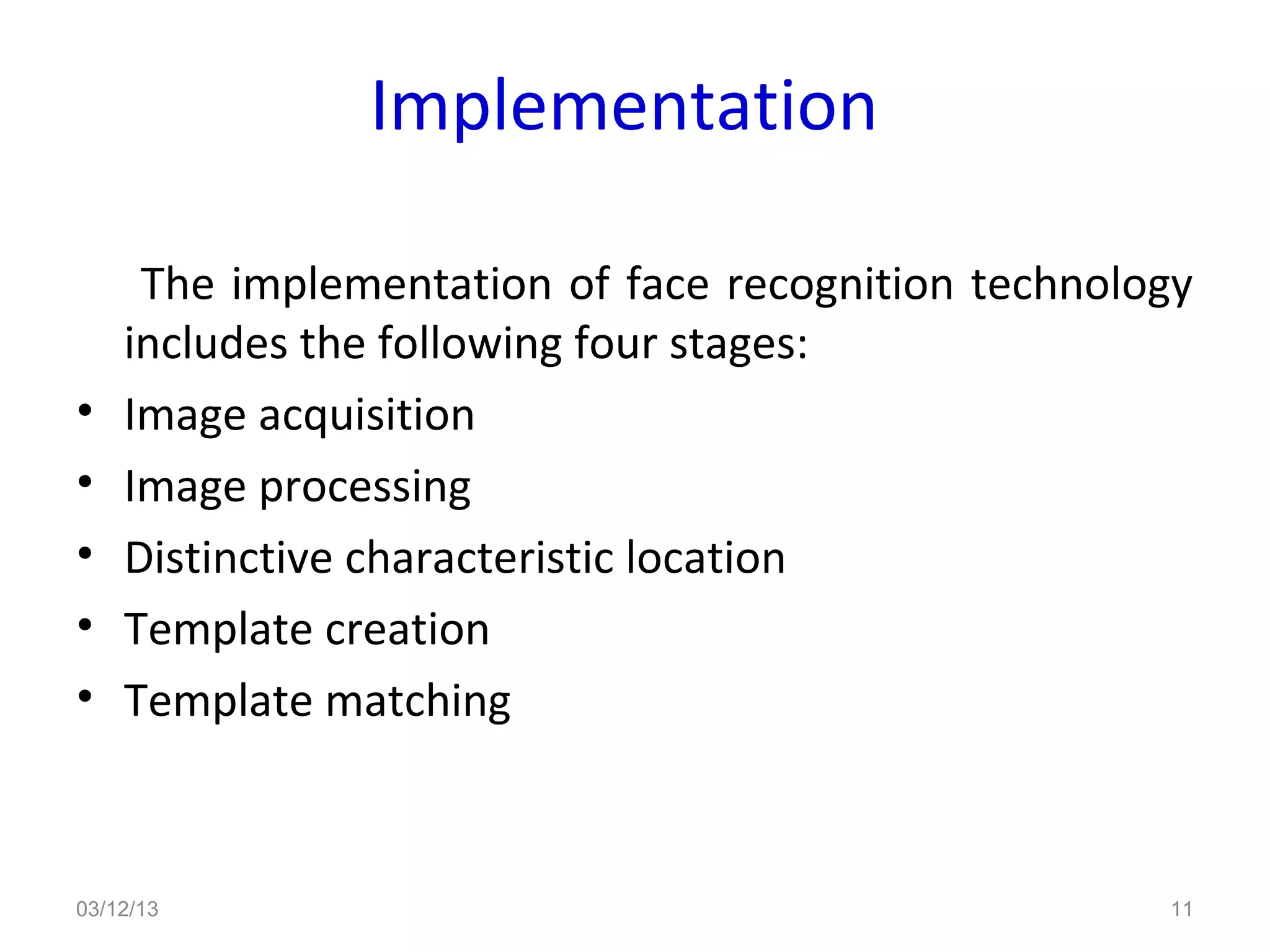
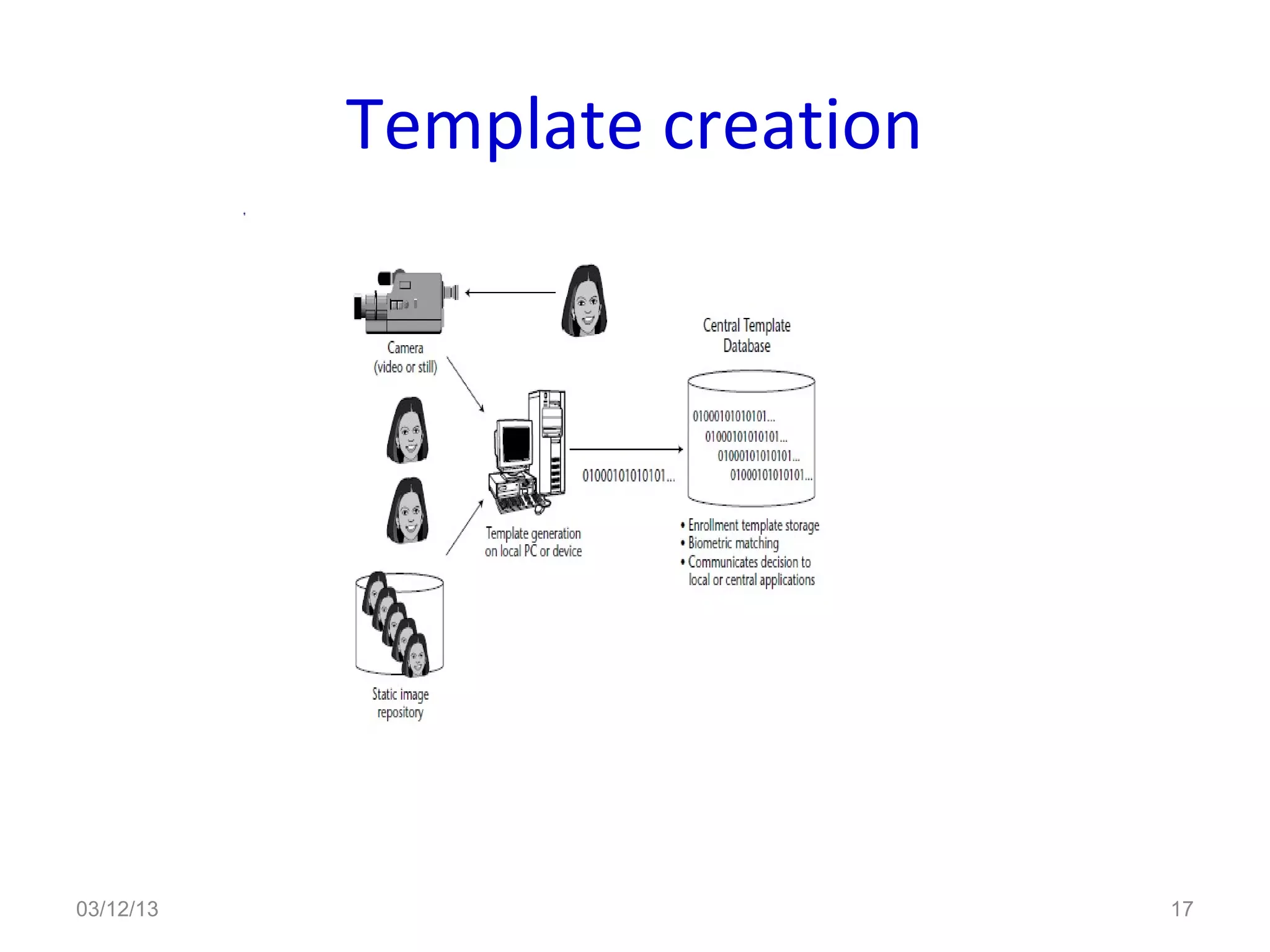
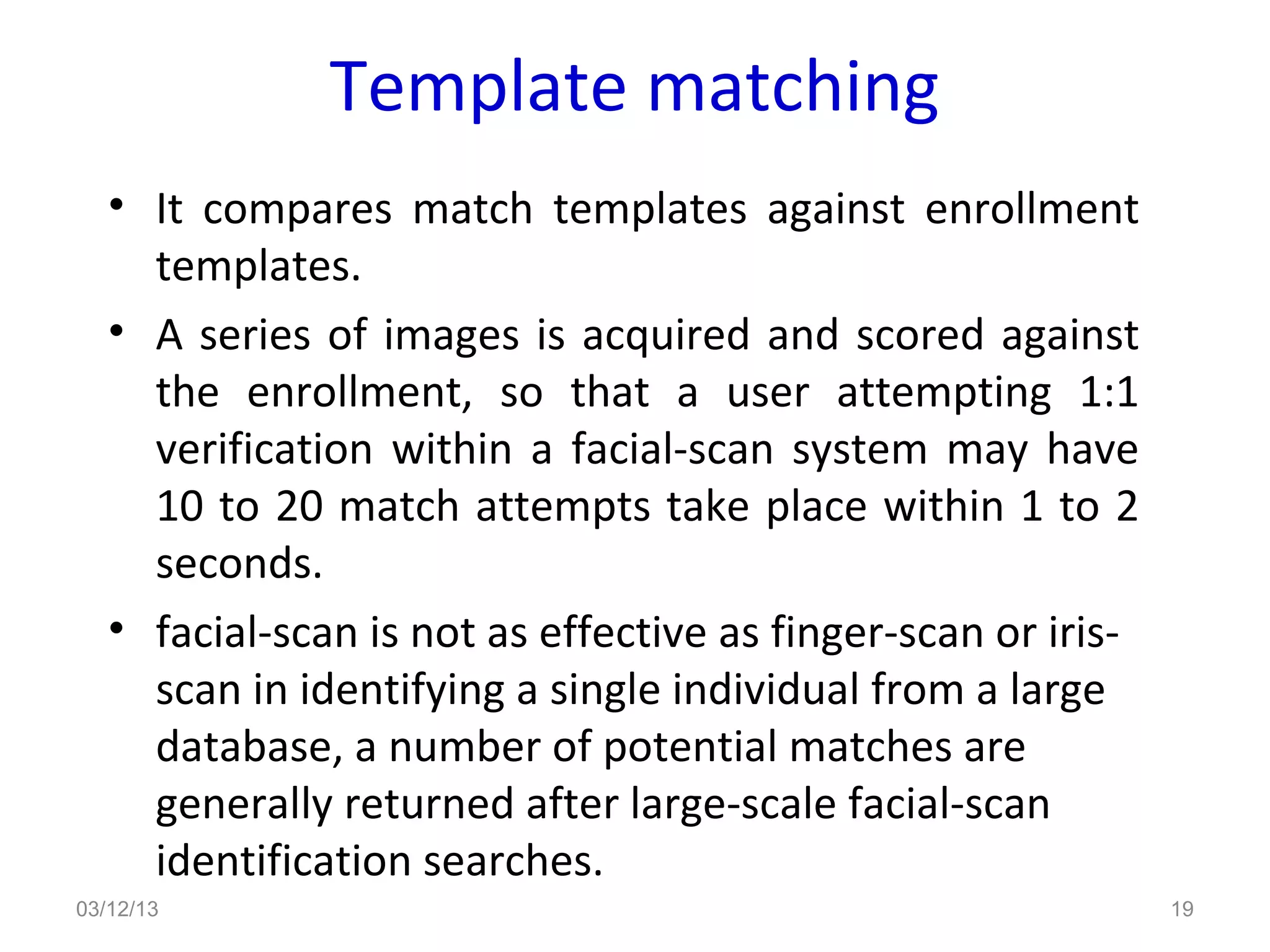
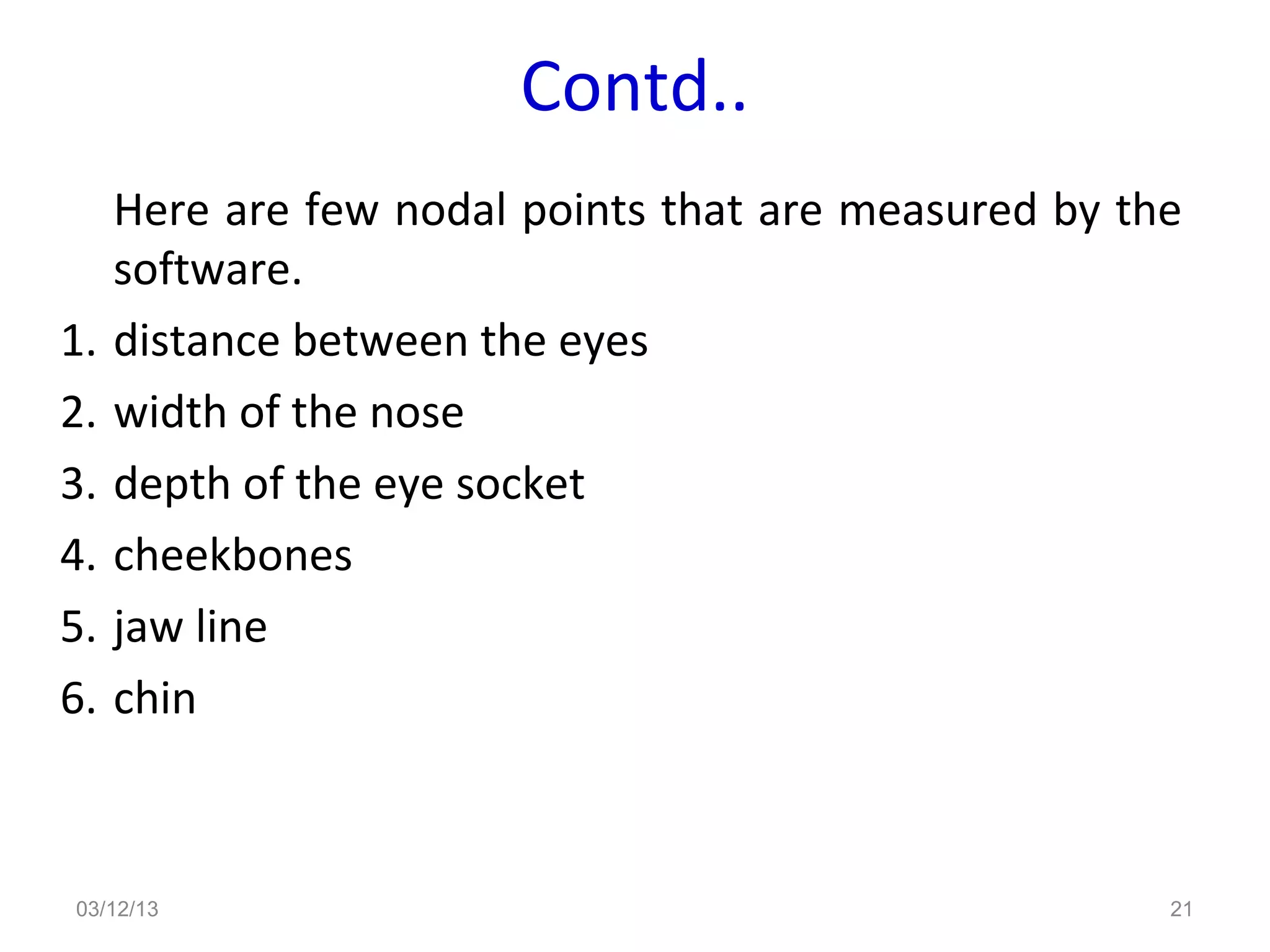
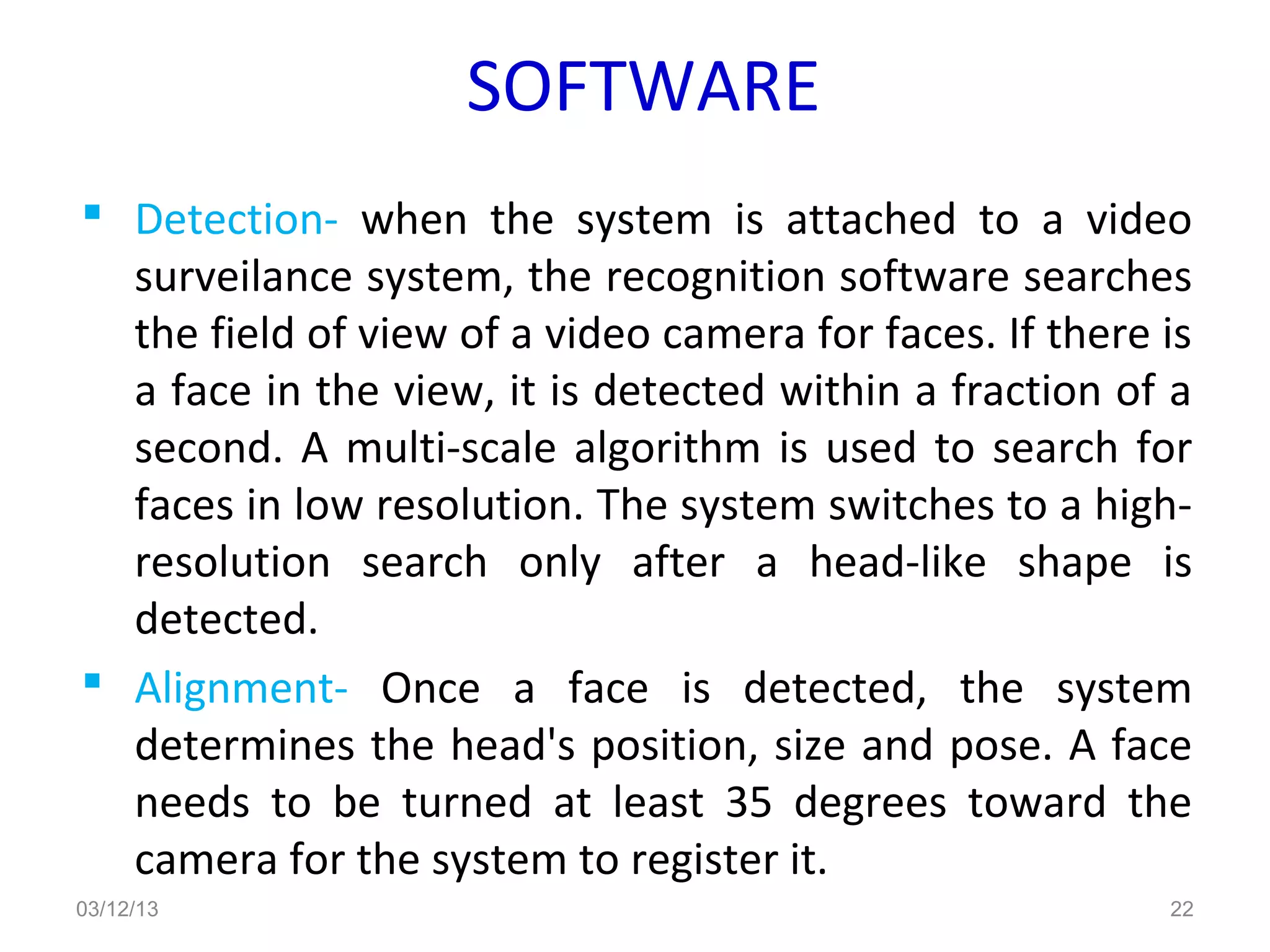
This document provides an overview of facial recognition technology. It discusses the history of facial recognition, how the technology works by detecting nodal points on faces and creating faceprints for identification. It also covers implementations, comparing images to templates to verify or identify individuals, and applications in security and surveillance. Strengths are its non-invasive nature, but it can be impacted by changes in appearance.