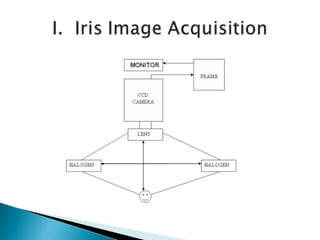
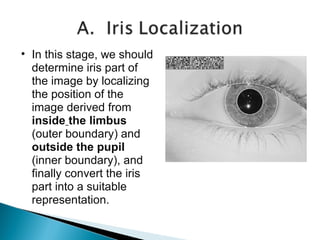
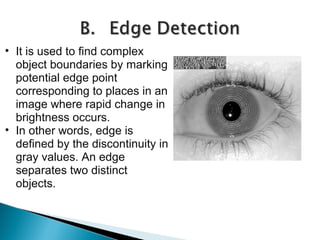
Mantra Softech is an Indian company that develops biometric security solutions including iris scanners. The presentation discusses the company profile, how iris scanners work, their advantages, applications, and software requirements. It explains that iris scanners capture images of the iris, analyze patterns in the iris, and encode the patterns in an iris code for identification purposes.