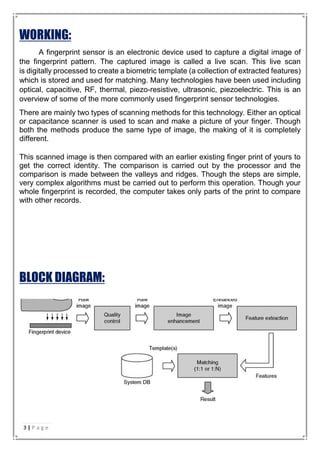
This seminar report discusses fingerprint sensors and their applications. It provides background on fingerprint identification and classification, then describes the main types of fingerprint sensors including capacitive, optical, thermal, pressure, radio frequency, and ultrasonic. It explains how fingerprint sensors work to capture and analyze fingerprint images. The report also outlines key applications of fingerprint sensors such as border control, driver's licenses, device unlocking, and biometric door locks. Finally, it discusses future applications involving linking fingerprint authentication to government identification cards and ATM security.








![ABOUT FINGER PRINTS:
Before going in detail about the technology used, it is very important to know about
the basics of our fingerprints. The basic information about fingerprint is that it is unique
for each person. Even a twin brother will not have the same fingerprint. Thus each
fingerprint is used to store a unique identifiable piece of information. The uniqueness
in each fingerprint is due to the peculiar genetic code of DNA in each person. This
code causes the formation of a different pattern of our fingerprint.
A fingerprint consists of ridges and valleys. They together provide friction for the skin.
The main identification of the skin is based upon the minutiae, which actually is the
location and direction of the ridge endings and splits along a ridge path. The image
shown below represents two types of minutiae as shown in FIG: 1(a)
FIG: 1(a) FIG: 1(b)
The image above [FIG: 1(b)] shows all the other characteristics of a fingerprint. These
characteristics may also be helpful during the process of minutiae extraction. The
unique information used for the identification includes the flow of the friction ridges,
the sequence and also the presence/absence of the individual friction ridge path
features.
4 | P a g e](https://image.slidesharecdn.com/seminarreportfinalcolour-170427211252/85/Report-on-Finger-print-sensor-and-its-application-10-320.jpg)
![TYPES OF FINGER PRINT:
Five main classes of fingerprints
o Arch [FIG: 2.1]
o Tented Arch [FIG: 2.2]
o Left Loop [FIG: 2.3]
o Right Loop [FIG: 2.4]
o Whorl [FIG: 2.5]
FIG: 2.1 FIG: 2.2
FIG: 2.3
FIG: 2.4 FIG: 2.5
5 | P a g e](https://image.slidesharecdn.com/seminarreportfinalcolour-170427211252/85/Report-on-Finger-print-sensor-and-its-application-11-320.jpg)