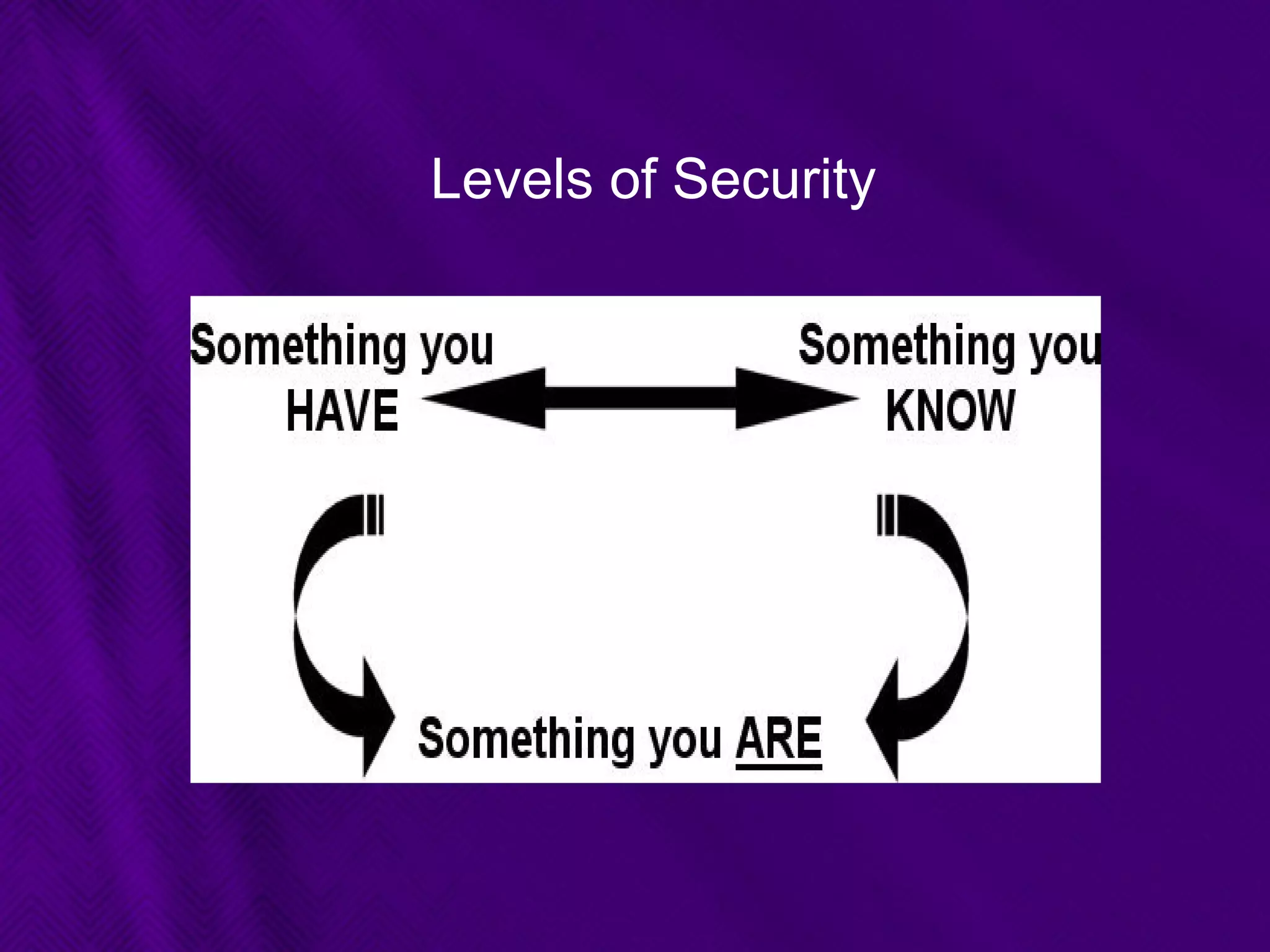
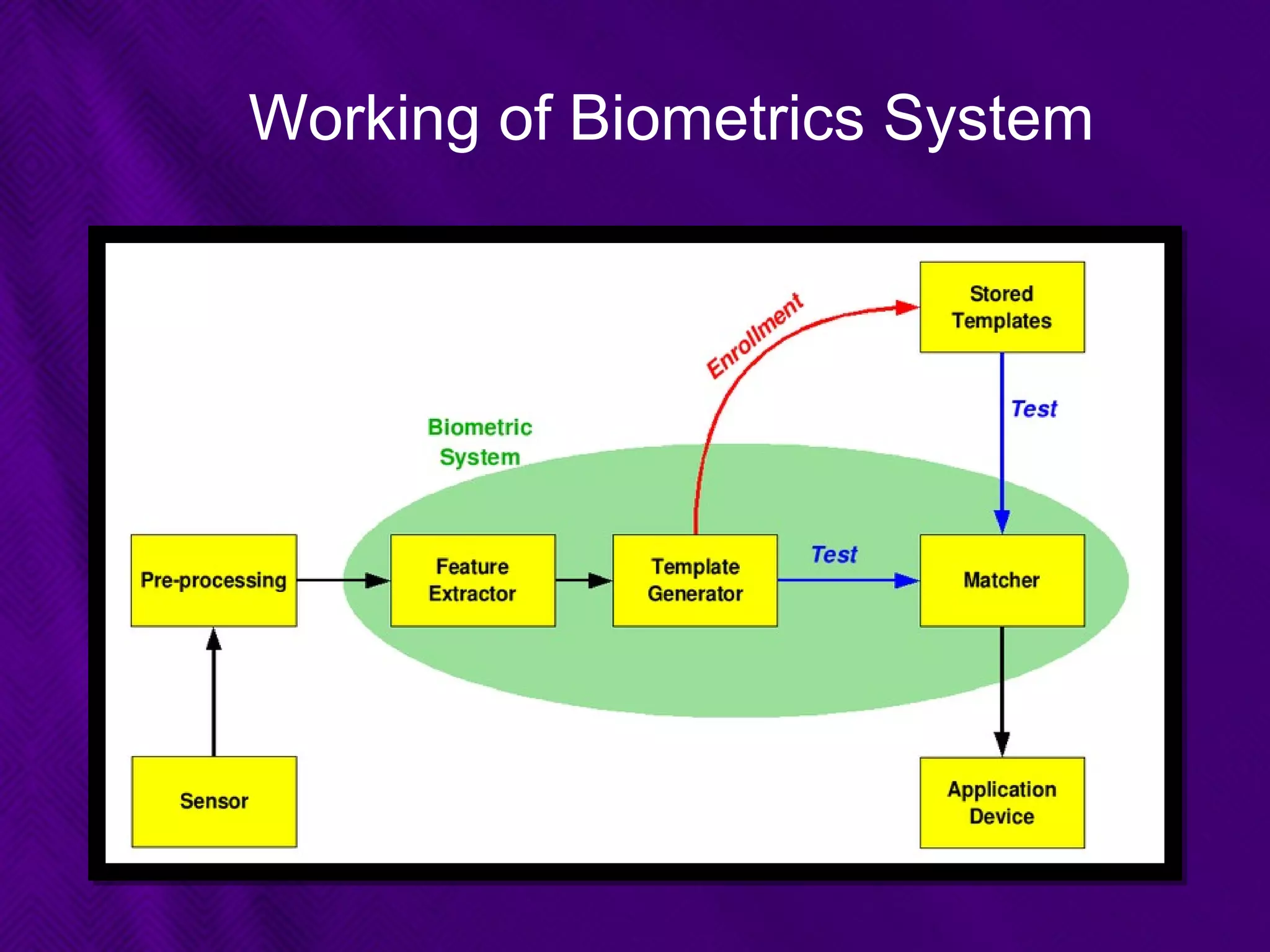
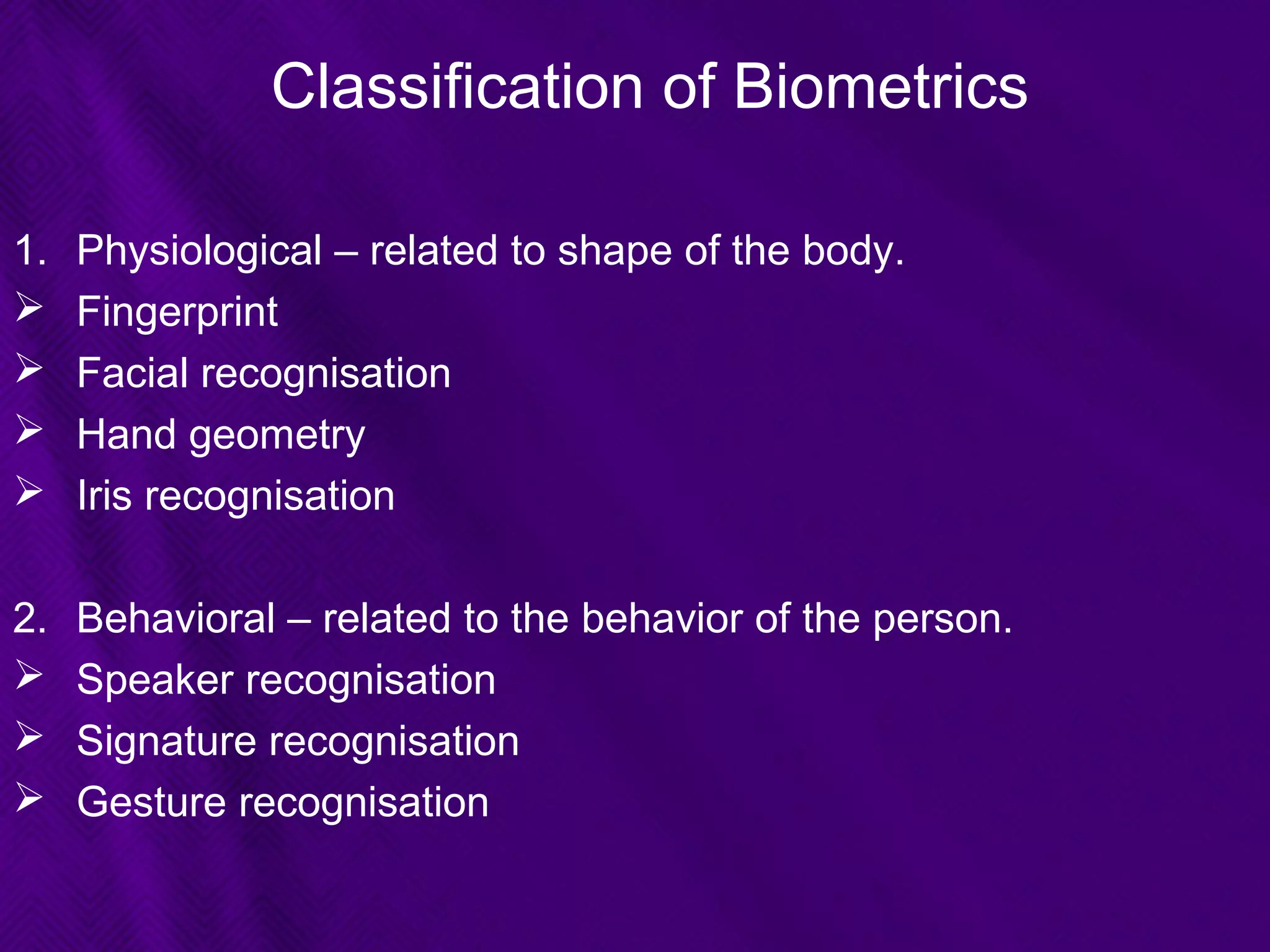
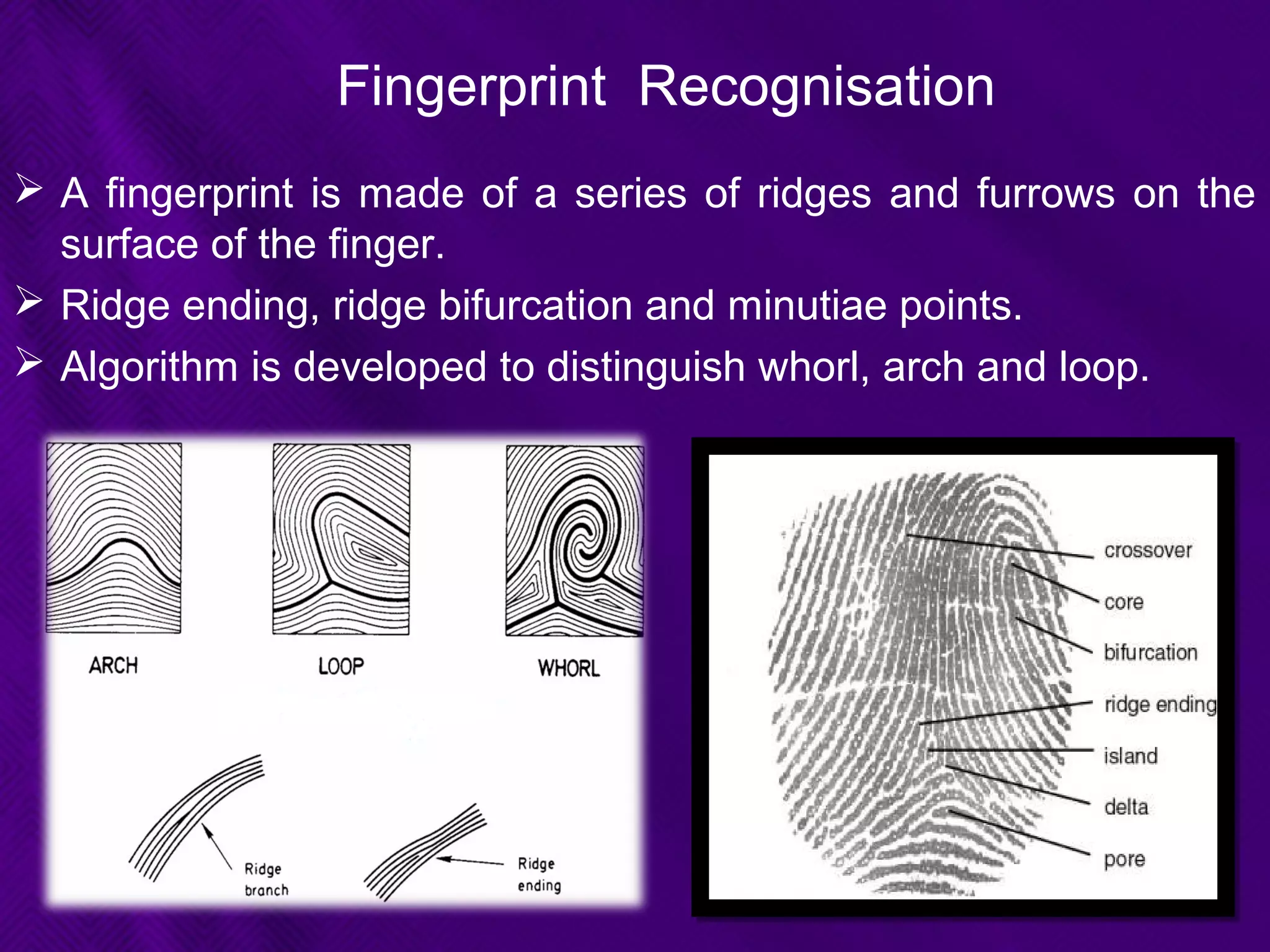
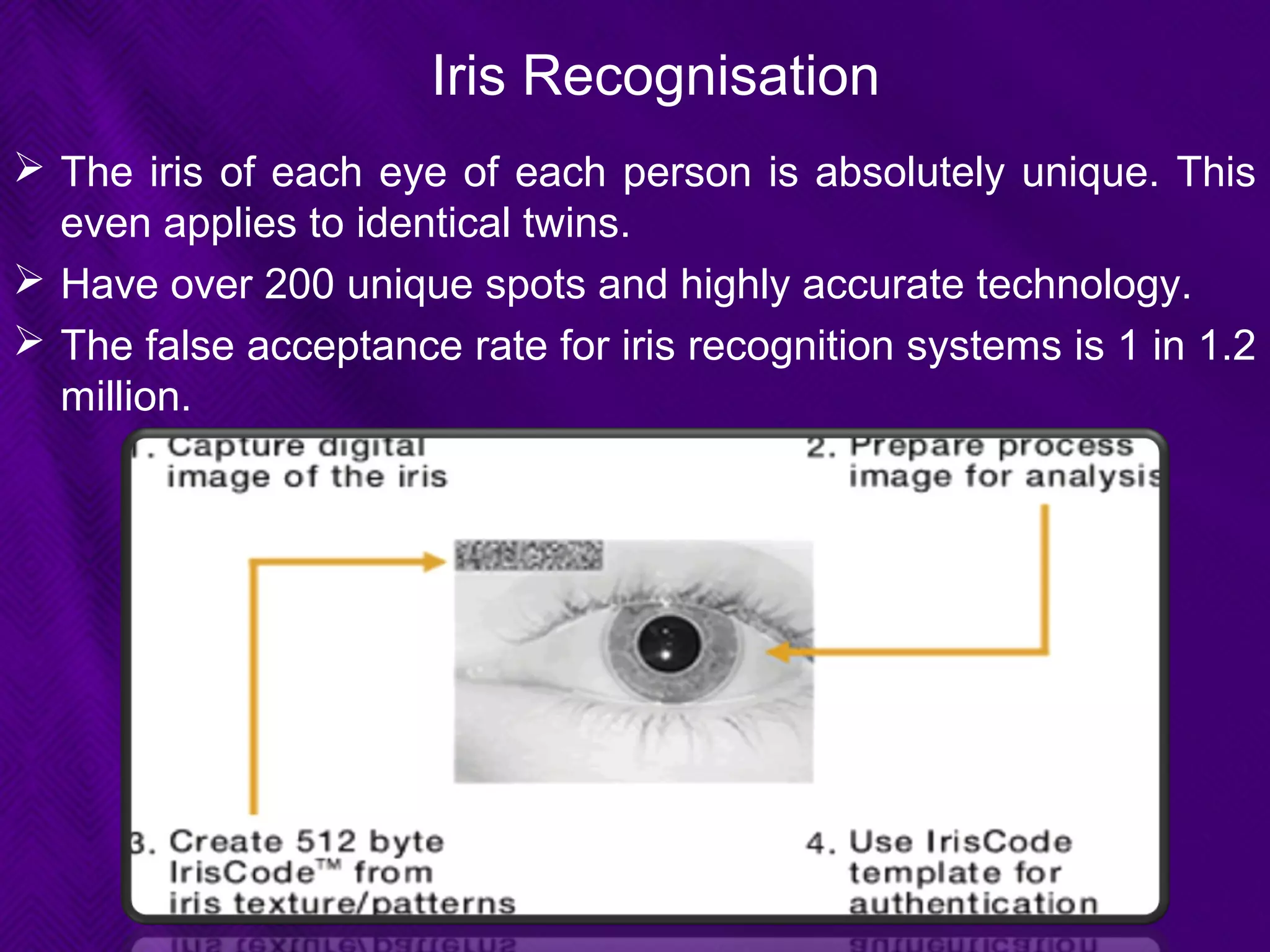
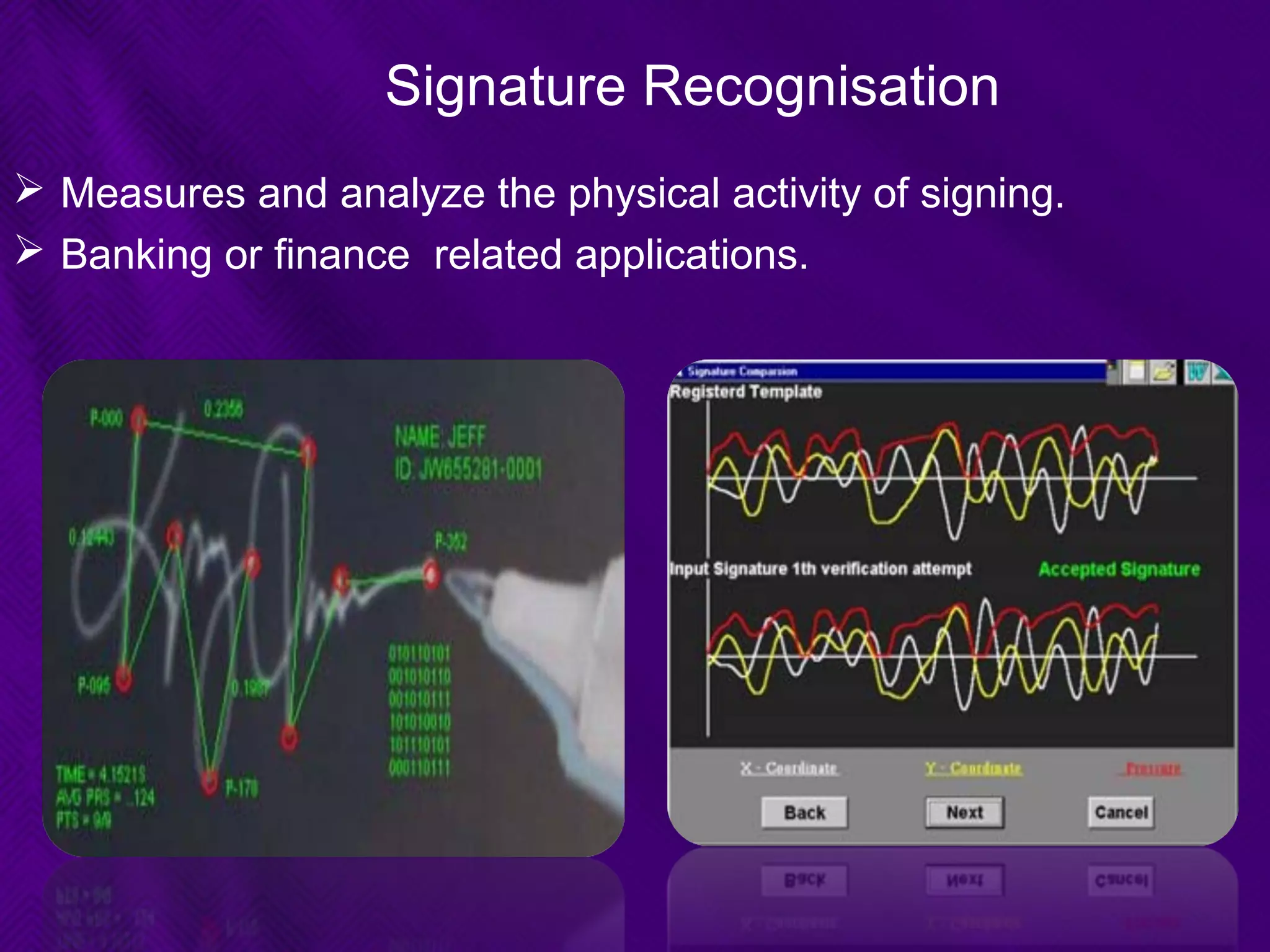
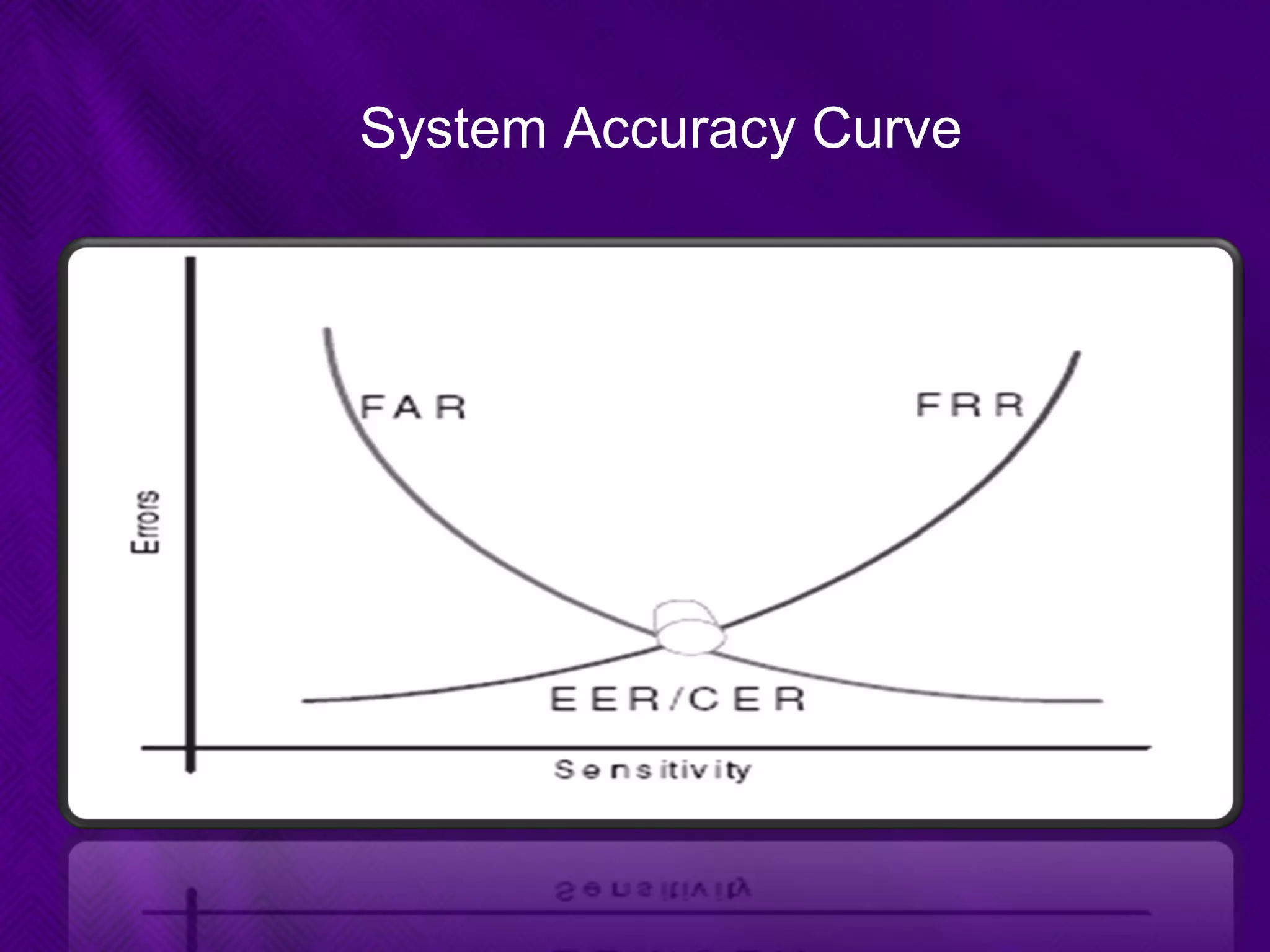
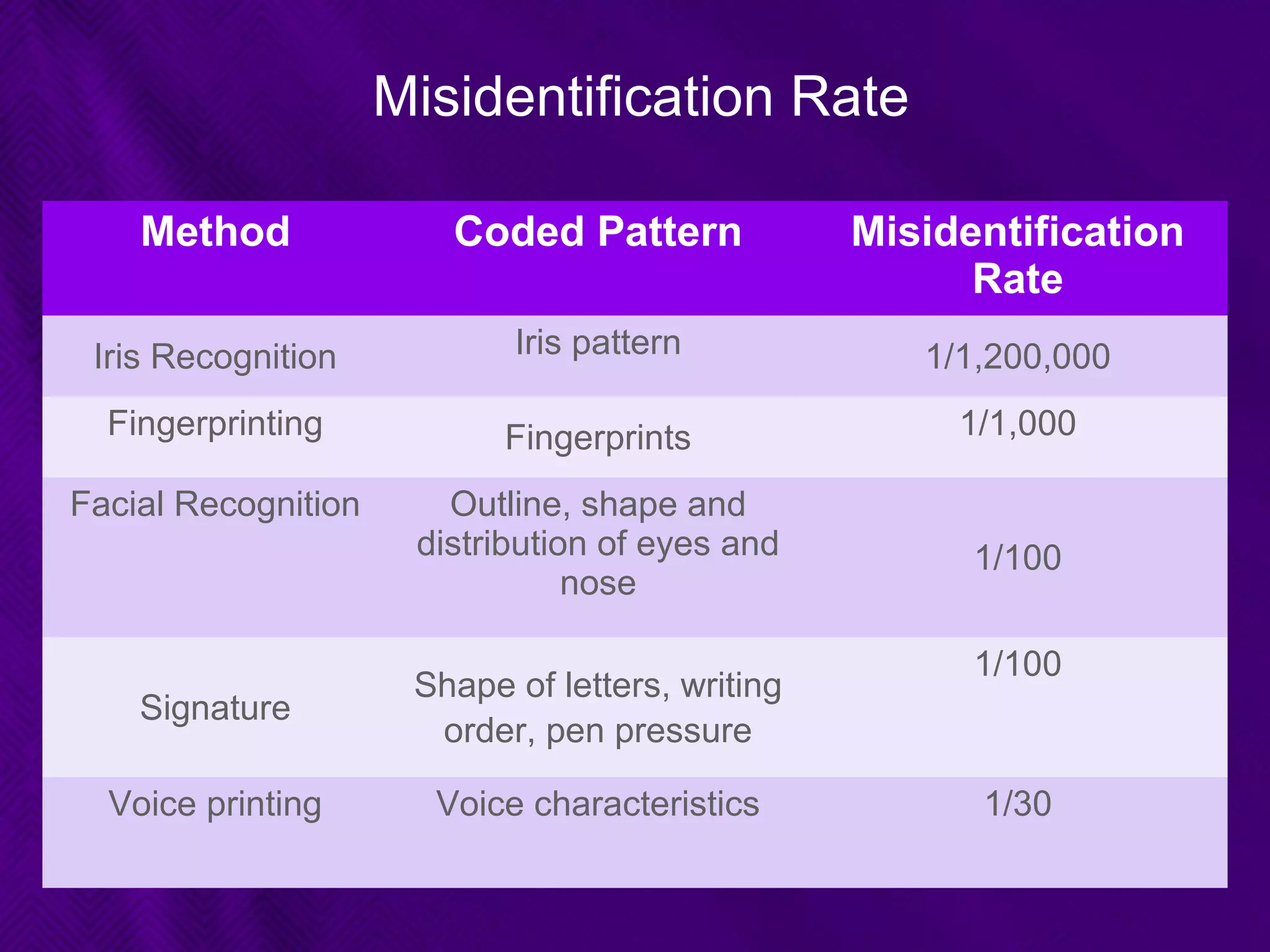
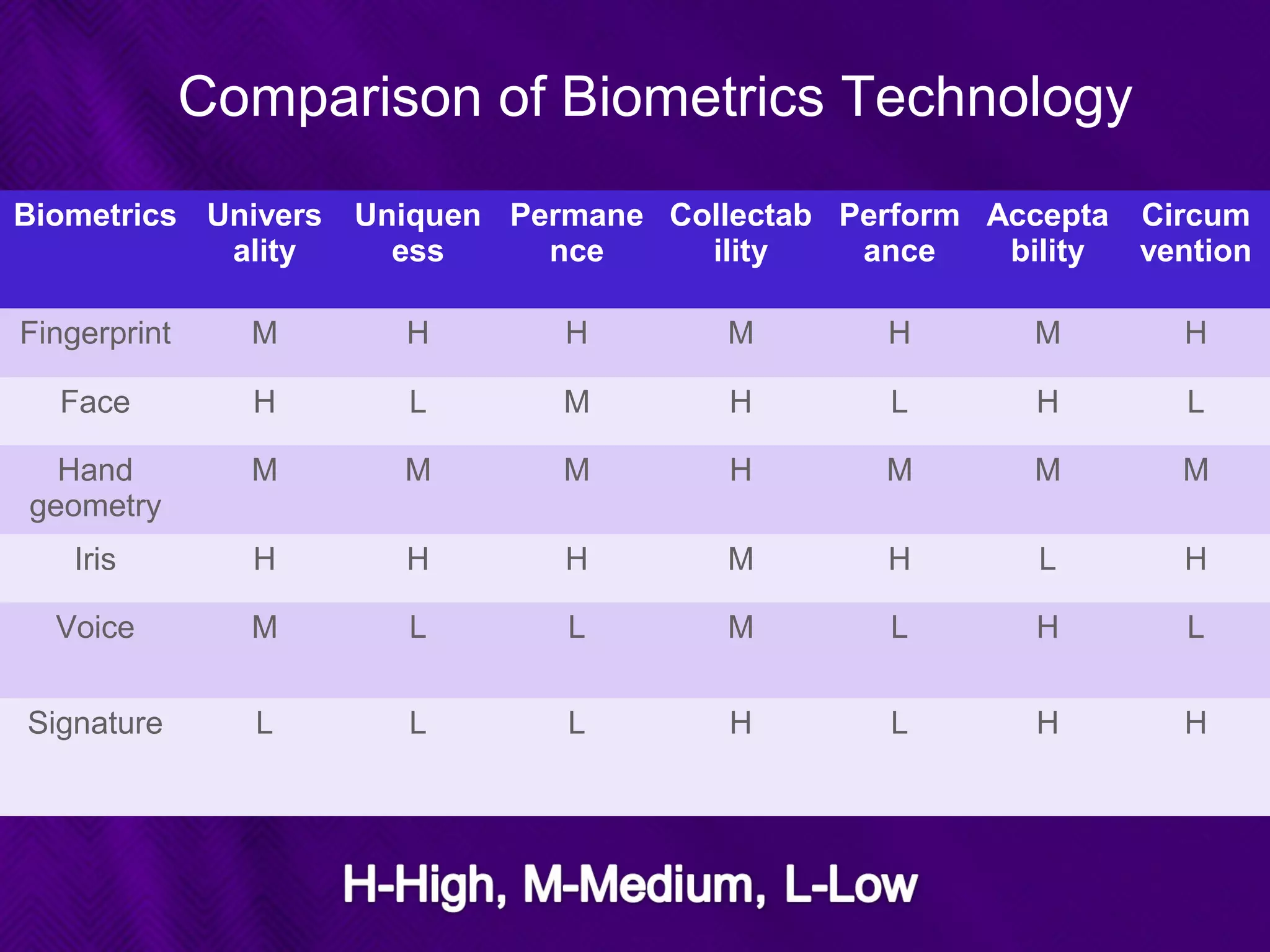
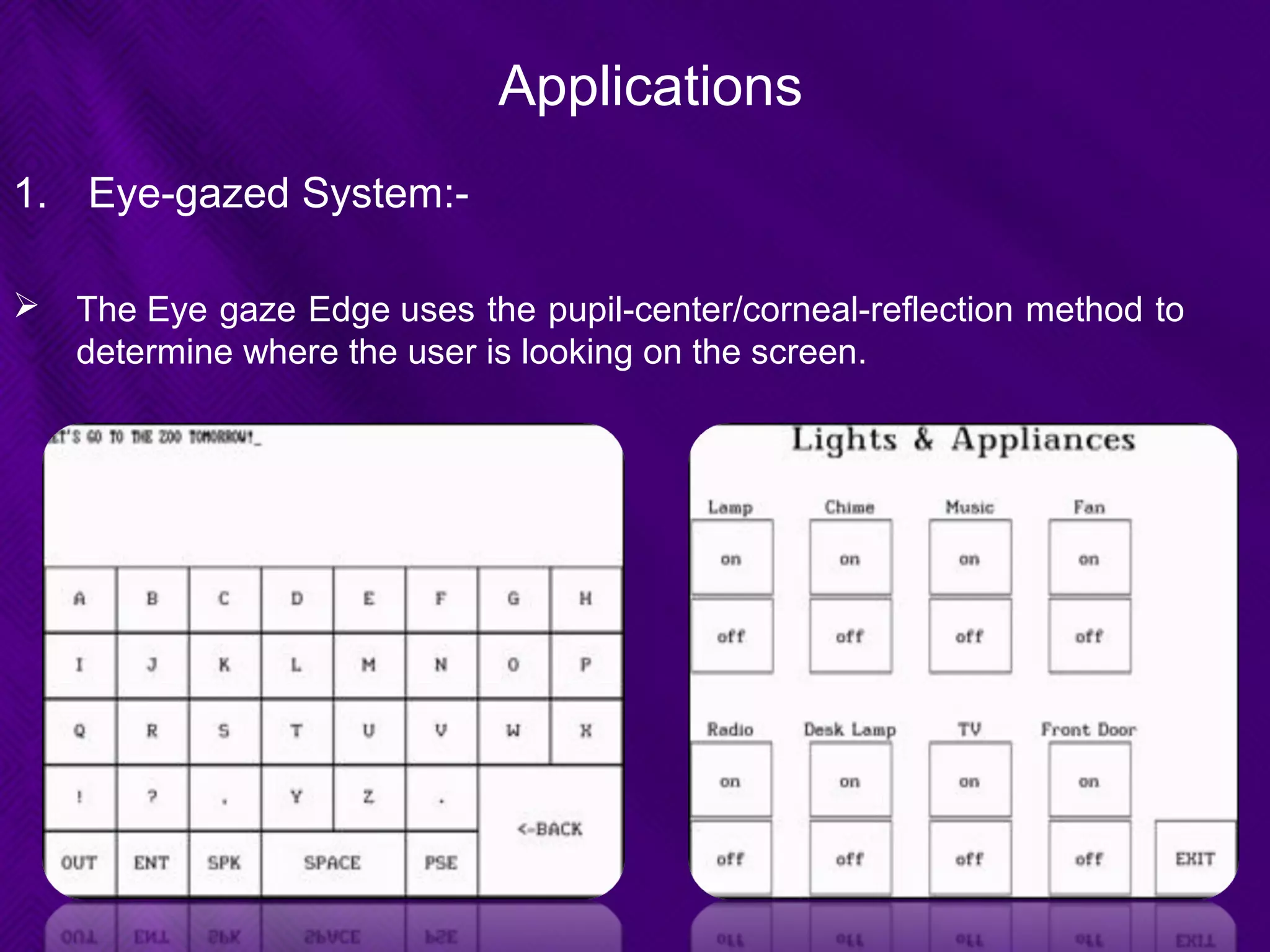
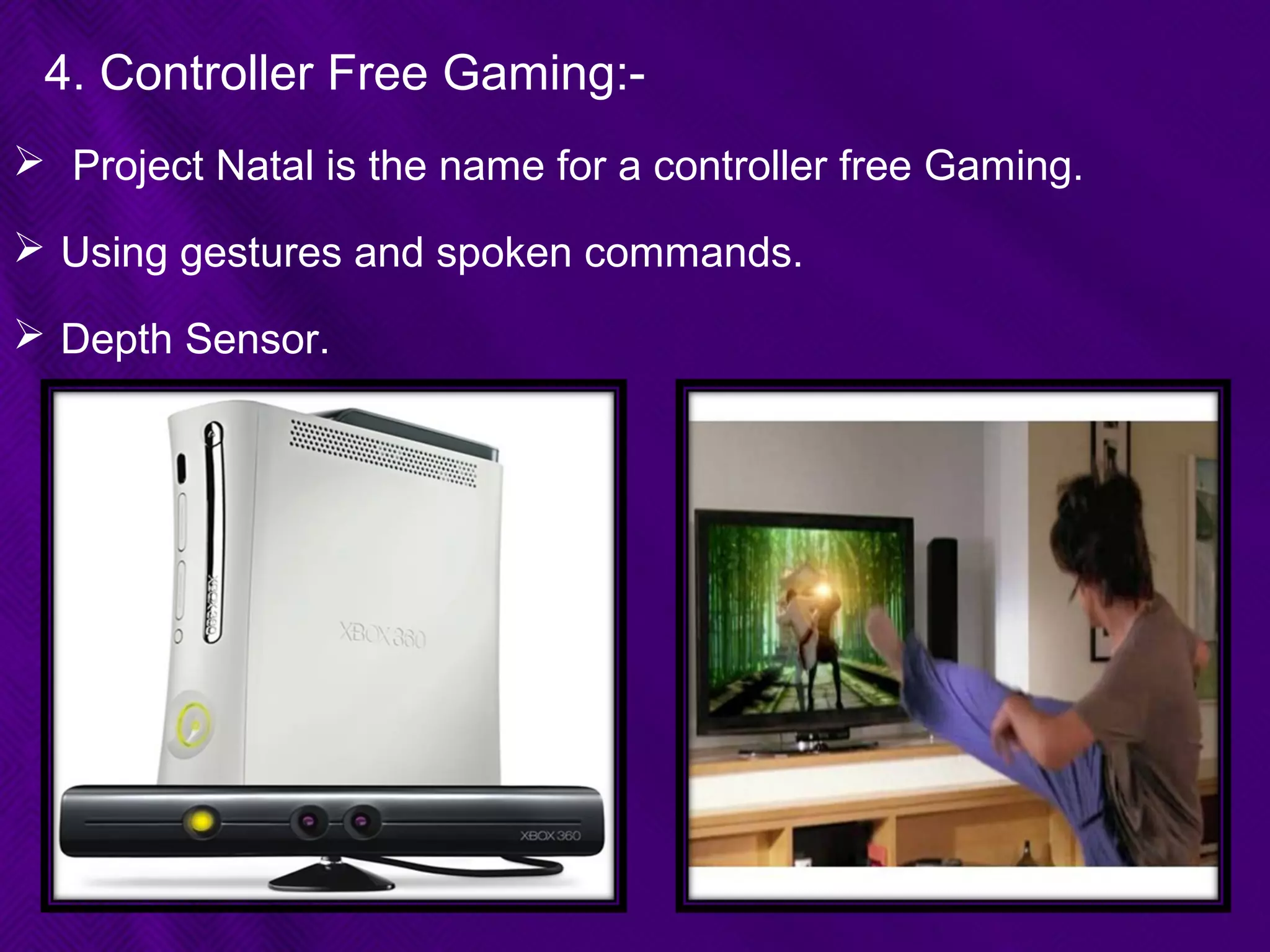
This document provides an overview of biometrics technologies. It begins with an introduction to biometrics and then discusses the history of biometrics from ancient Egyptians and Chinese using fingerprints to modern systems being developed in the 1970s. The document outlines key characteristics biometrics must have such as universality and permanence. It then classifies and describes various biometric technologies including fingerprint, face, iris, voice, and signature recognition. Application examples are presented for areas like gaming, television control, and accessibility switches. The document concludes that biometrics provide a user-friendly way to interact with devices without passwords while continuing to develop as an emerging field.