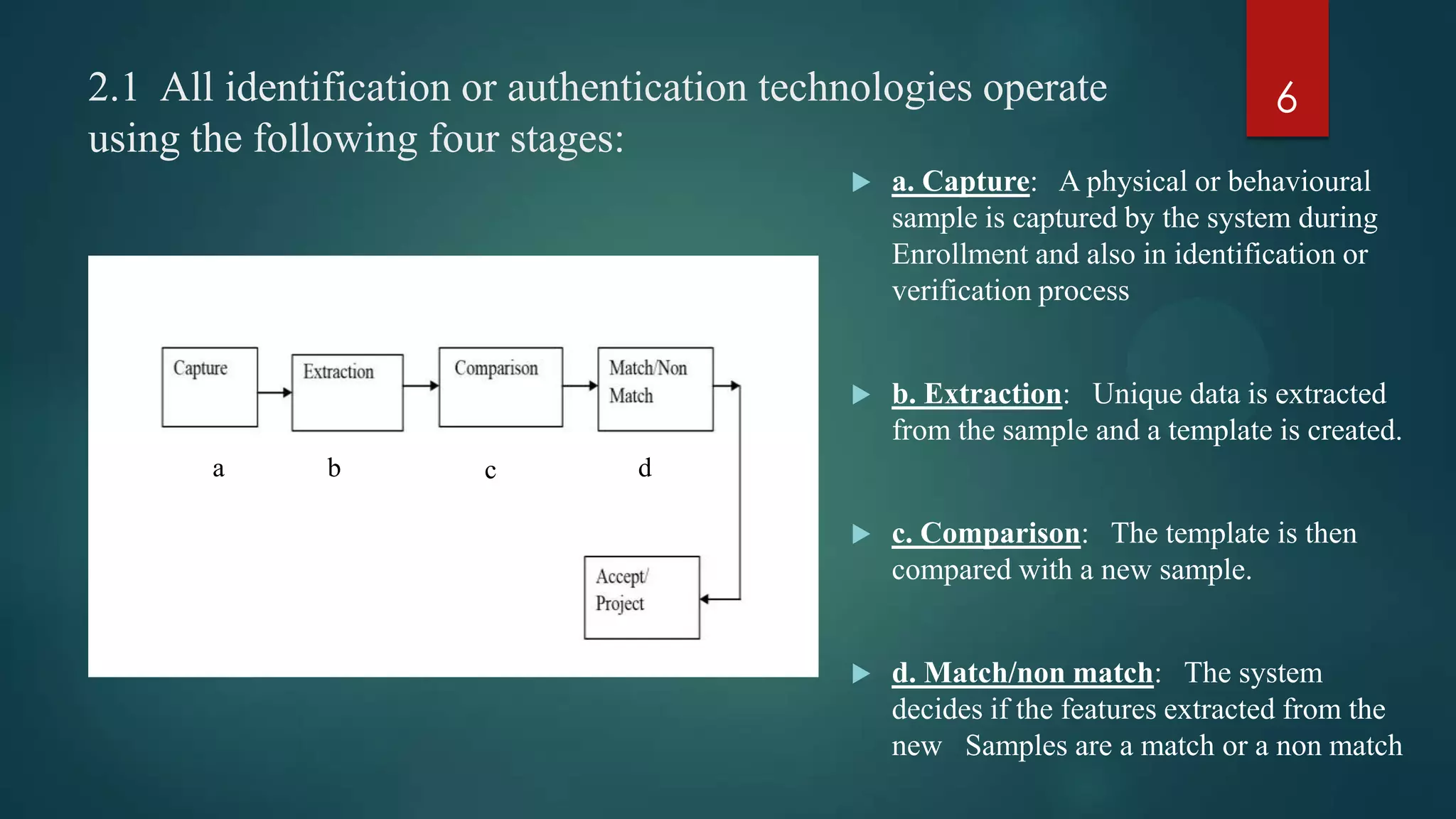
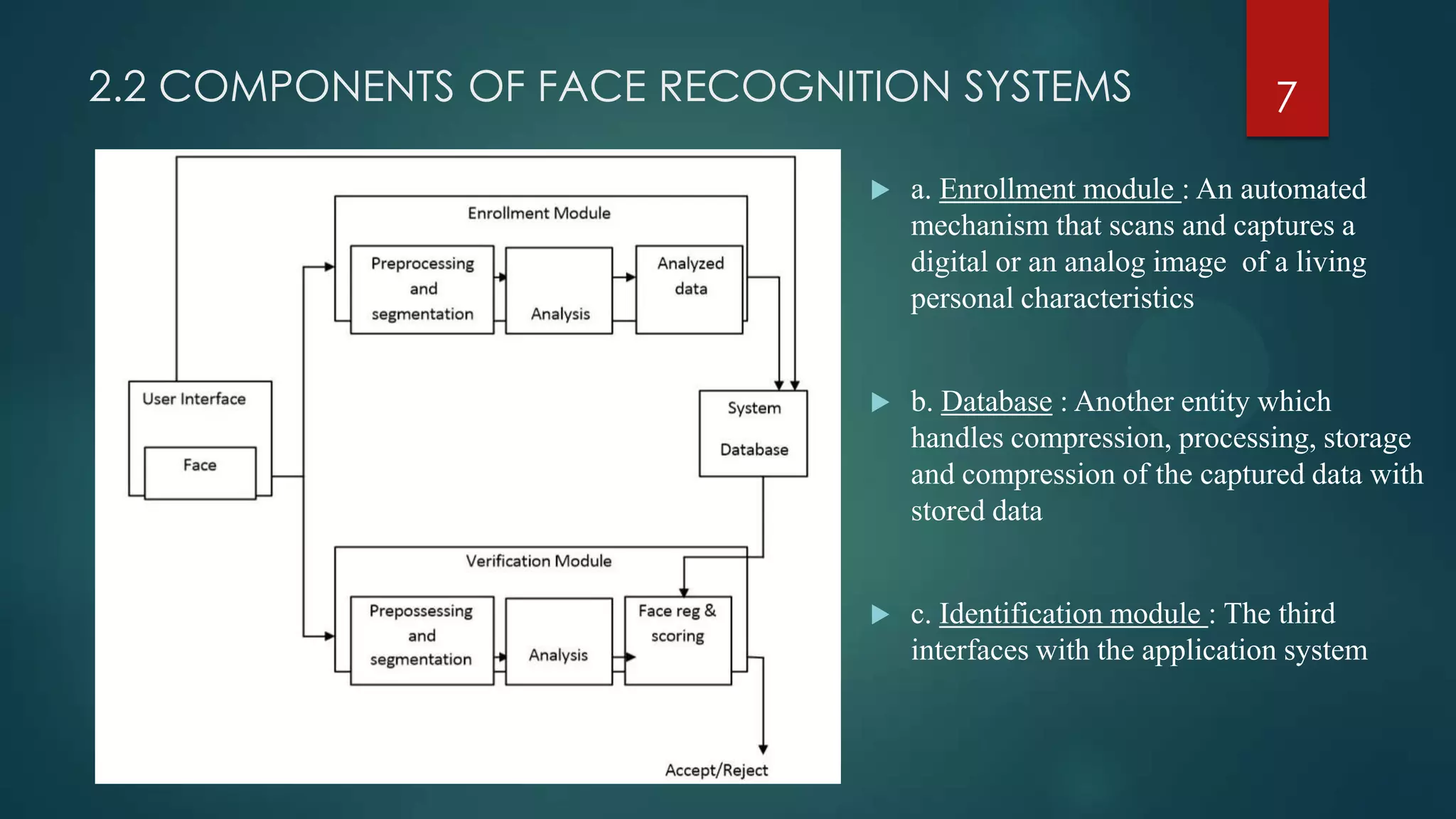
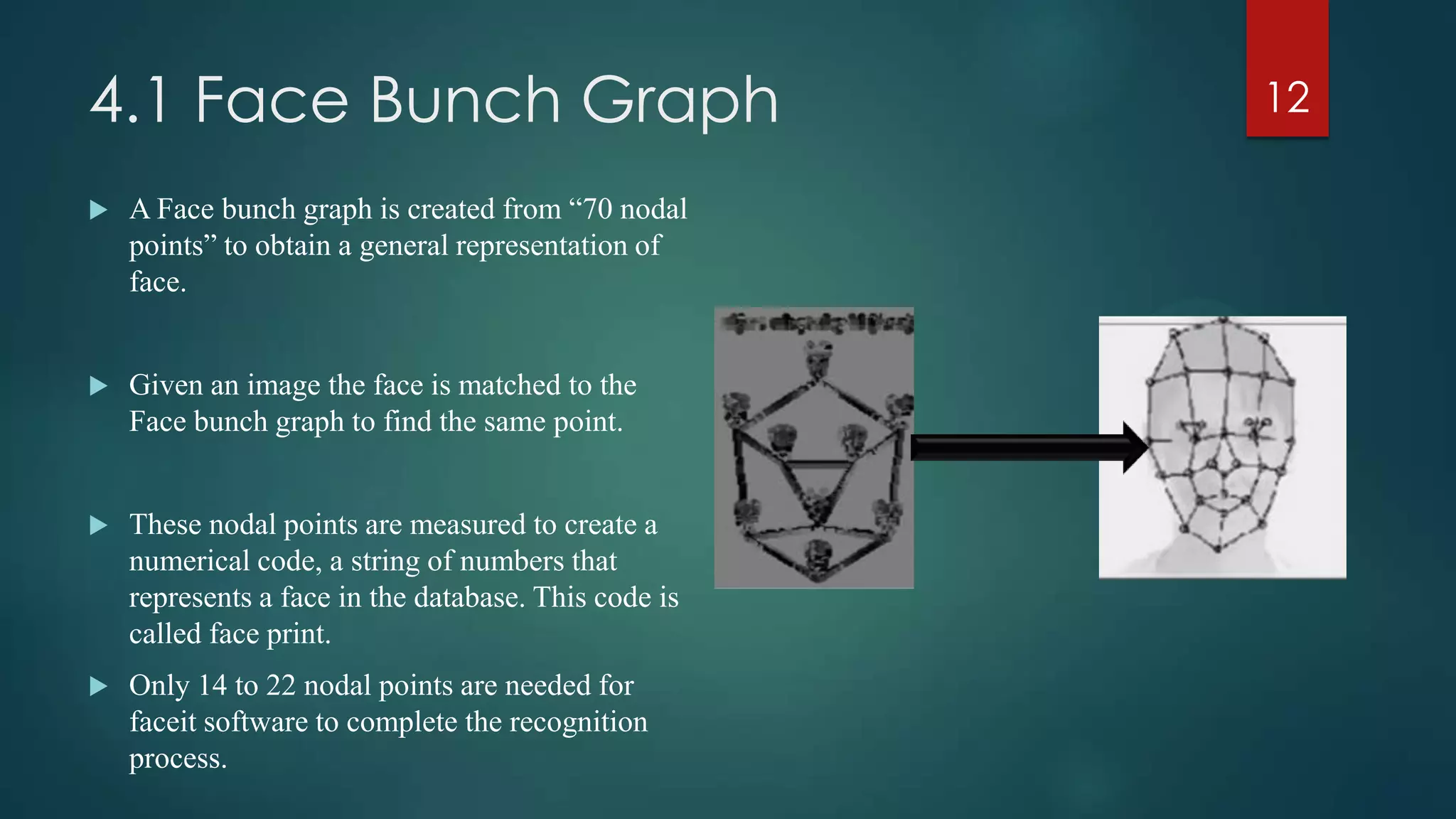
Face recognition technology may help solve problems with identity verification by analyzing facial features instead of passwords or pins. The document outlines the key stages of face recognition systems including data acquisition, input processing, and image classification. It also discusses advantages like convenience and ease of use, as well as limitations such as an inability to distinguish identical twins. Potential applications are identified in government, security, and commercial sectors.