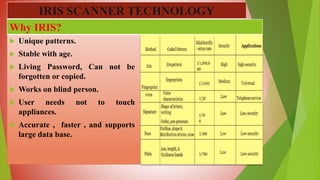
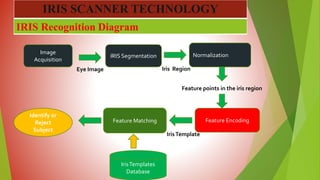
This document presents information on iris scanner technology from a presentation by Shams. It discusses what the iris is, why iris recognition is used, the history and development of iris recognition, how iris recognition systems work, advantages like the iris being unique and stable over time, and disadvantages like the small target size and it being obscured. The conclusion is that iris scanning is highly accurate and fast but still needs some development to become more widely used technology.








![Test of Statistical Independence
Compare the iris codes (256*8=2048 bits) of the eyes using the
following formula.
[Code A (XOR) Code B] AND Mask AAND Mask B
H.D= ---------------------------------------------------------------------------------------------------------------------
Mask AAND Mask B
This is called Hamming Distance (H.D).
Iris pattern - Comparison
IRIS SCANNER TECHNOLOGY](https://image.slidesharecdn.com/irisscannertechnology-170307042507/85/Iris-scanner-technology-11-320.jpg)




