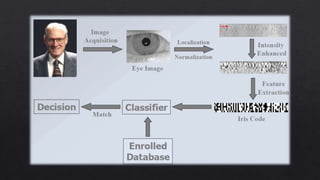
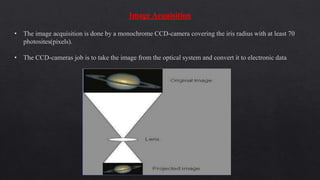
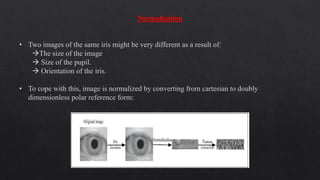
The document provides an overview of iris recognition technology, detailing its history, physiological principles, and operational mechanics, including image acquisition and feature extraction techniques. It outlines the advantages and disadvantages compared to other biometric systems, highlighting its accuracy and non-invasiveness while addressing challenges like poor image quality and usability for certain subjects. Additionally, it discusses various applications such as national border control, secure access, and financial transactions, concluding with the potential for wide adoption of this technology.