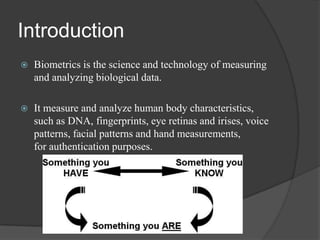
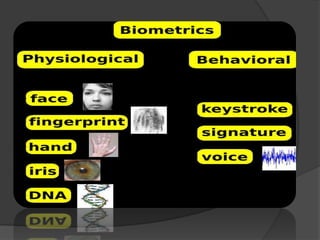
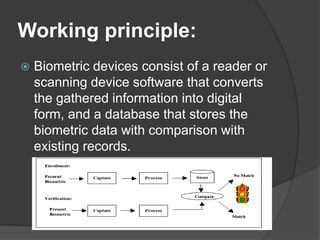
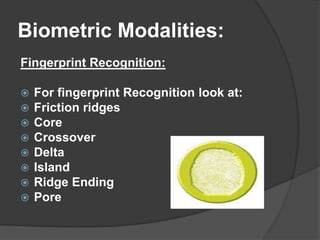
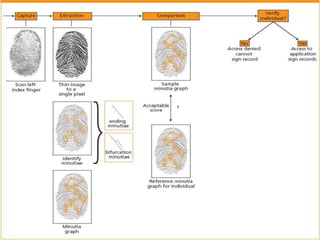
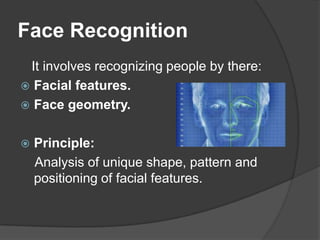
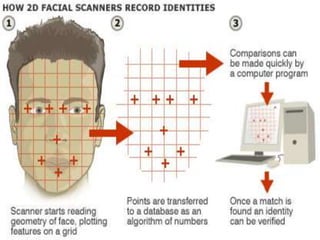
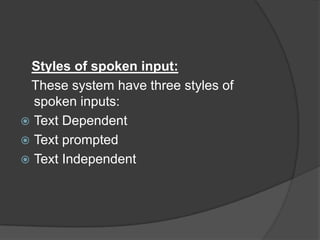
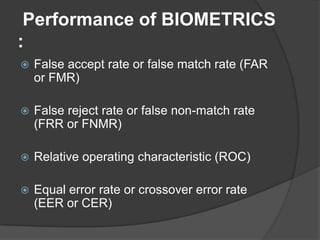
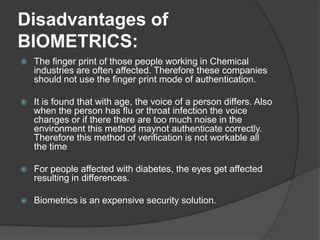
This document discusses biometrics, which uses human body characteristics to authenticate identity. It describes biometric devices that scan and digitize characteristics like fingerprints, irises, voice patterns. Biometrics can be physiological (face, fingerprints) or behavioral (signature, voice). To be used for identification, characteristics must be universal, unique, permanent, collectible, and difficult to circumvent. The document outlines various biometric modalities like fingerprint recognition, face recognition, voice recognition, and iris recognition. It also discusses advantages like accuracy but notes disadvantages like cost and changing characteristics with age, disease, or environment.