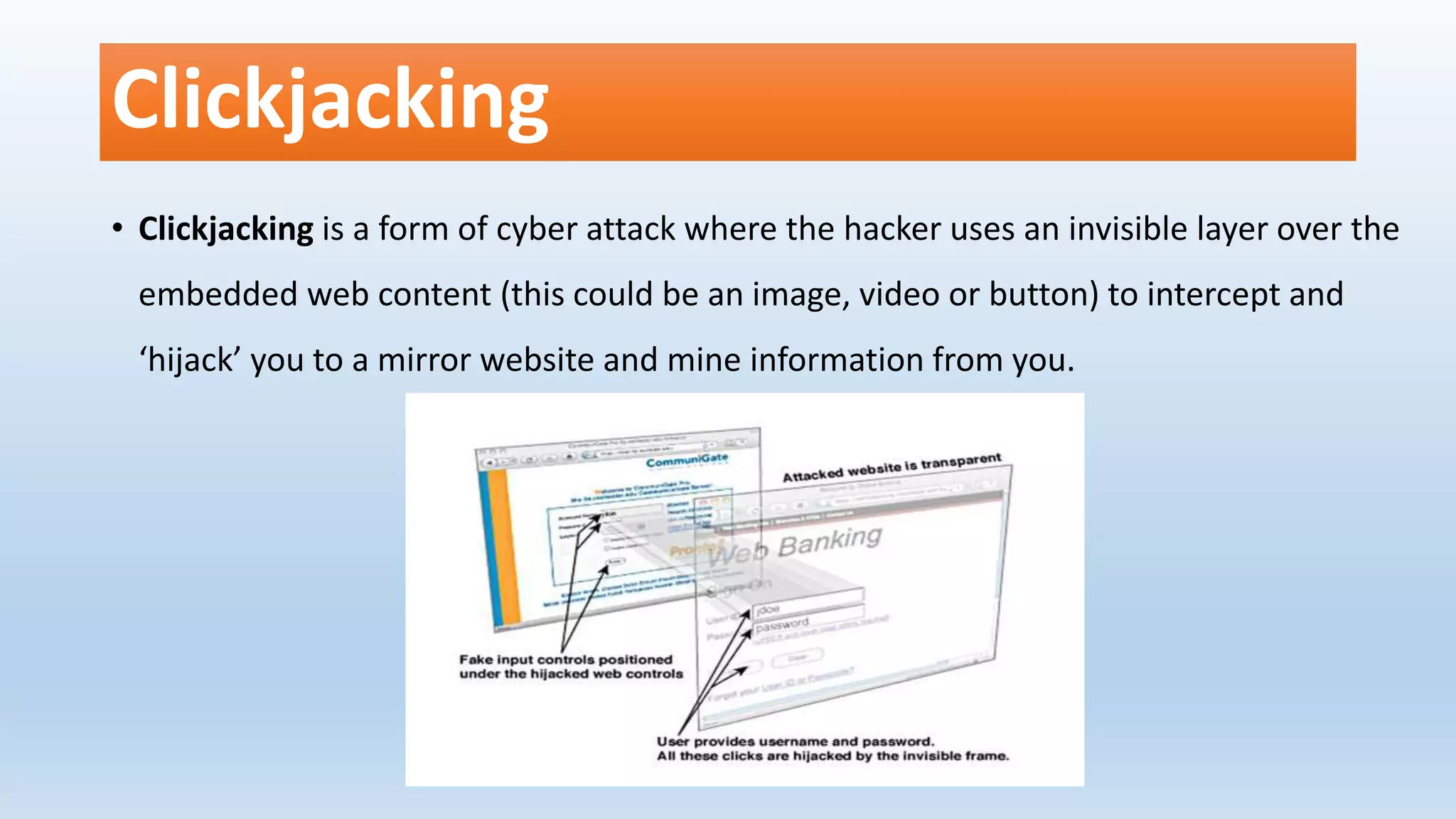
Cyber crime refers to any illegal activity involving computers or networks. Early cyber crimes included the first spam email in 1978 and the first computer virus in 1982. Cyber threats have evolved from using computers as simple tools to commit crimes like cyber theft to targeting computers directly through hacking and viruses. As technology advanced, criminals began using computers as instruments to aid crimes like money laundering. Common cyber crimes today include financial crimes, IP spoofing, trojans, web jacking, session hijacking, mail bombing, and keyloggers. Cyber security tools and practices like antivirus software, firewalls, passwords, and awareness can help prevent and defend against cyber crimes.