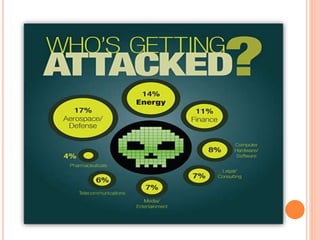
The document outlines the concepts of cyber crime and cyber security, emphasizing their significance in protecting data and national security. It discusses major security issues like viruses and hacking, provides safety tips, and highlights the pros and cons of cyber security. The conclusion suggests that understanding and implementing cyber security measures is crucial due to emerging threats.