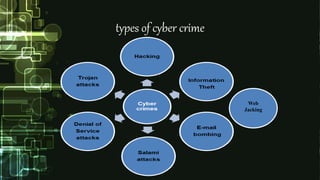
This document provides an outline on cyber crimes and cyber security. It begins with an introduction on the growth of the internet and the rise of cyber crimes. It then defines cyber crime as unlawful acts using computers as tools or targets. The document categorizes cyber crimes as those using computers as weapons or targets, and lists common types like hacking, viruses, and identity theft. It discusses the history of cyber crimes and reasons they occur like ease of access online and complex networks. The document also defines cyber security, provides advantages like protection from attacks, and offers tips for prevention such as using antivirus software and firewalls. It concludes that cyber security is an ongoing battle and everyone must play a role to be responsible online.