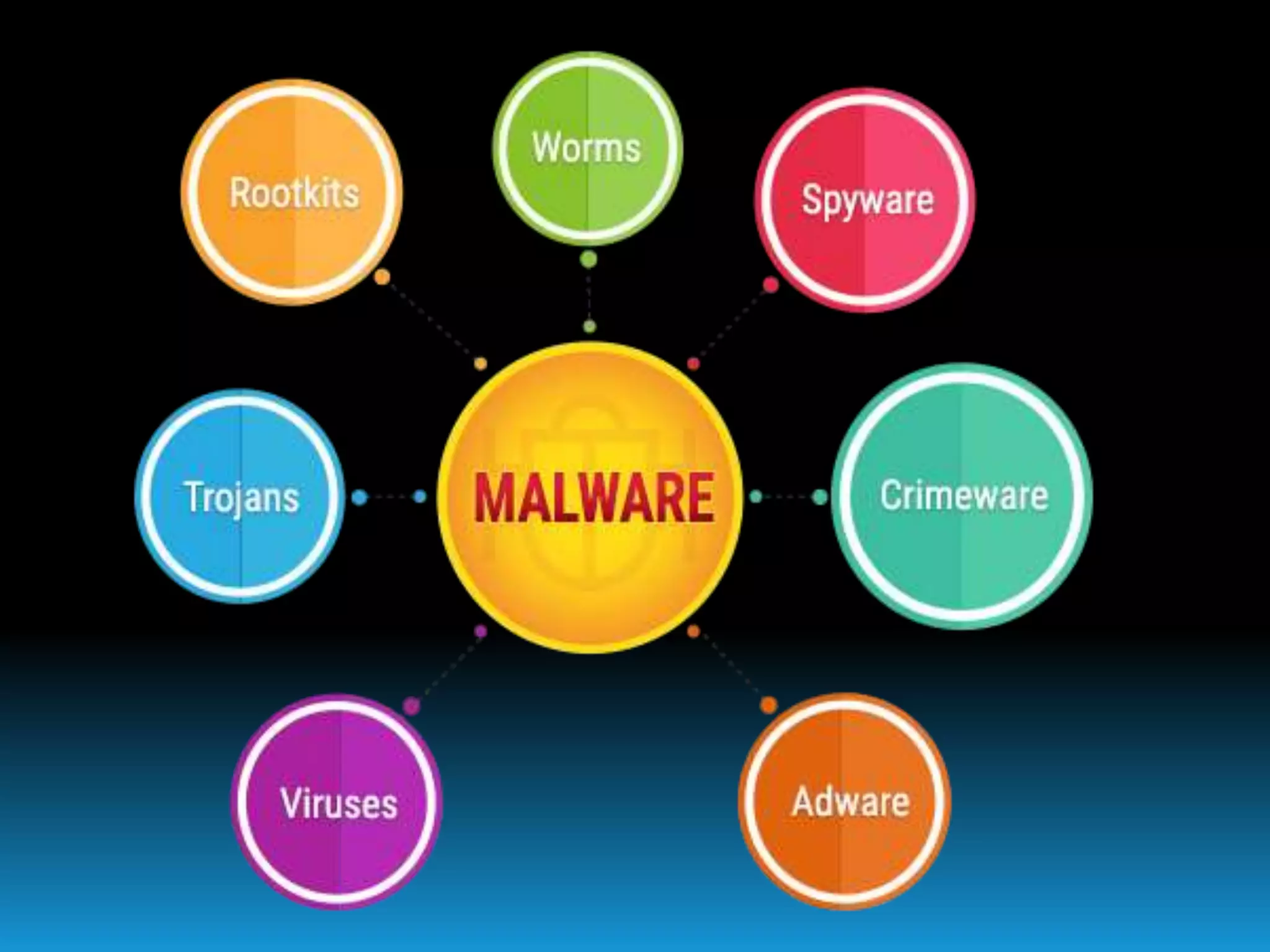
This document discusses cyber security and the need for protecting online information. It defines cyber security as protecting computer systems, software, data and services from disruption or theft. Common security threats are discussed such as viruses, hackers including white hat, grey hat and black hat hackers, malware like Trojan horses, and password cracking. The document provides solutions for implementing security like using antivirus software, firewalls, strong unique passwords, and backups.