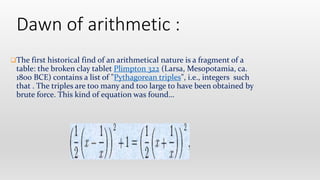
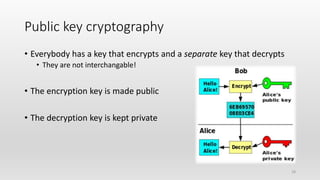
Number theory is a branch of pure mathematics focused on the study of integers, historically known as arithmetic. Key historical figures include the Pythagoreans, Āryabhaṭa, and Diophantus, each contributing foundational concepts such as irrational numbers and polynomial equations. The document also discusses practical applications of number theory in fields like cryptography and error-correcting codes, highlighting its importance in securing digital transactions.