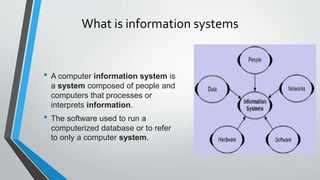
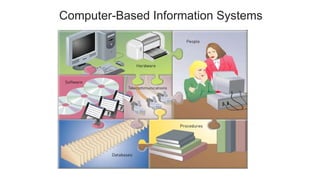
This document provides an introduction to cyber security. It defines cyber security as protecting cyberspace from attacks, and defines a cyber attack. It explains that cyberspace is where online communication occurs, via the internet. Cyber security is important because it affects everyone who uses computers and networks. Cyber security training is needed to establish human controls. Cyber attacks can target businesses, governments, institutions and individuals. Attackers include hackers, criminals, spies and nation-states who use methods like malware, social engineering, and network attacks. Defenders of cyber security include ICT teams, security vendors, manufacturers, and governments. Information systems and quality data are important assets to protect. Emerging cyber threats include cloud services, ransomware, spear ph