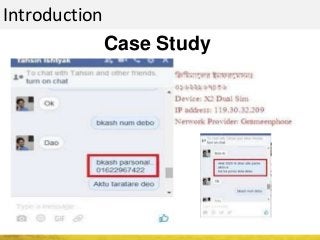
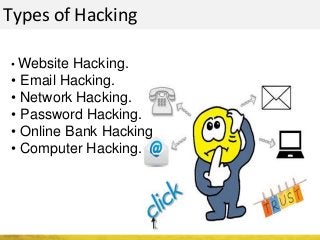
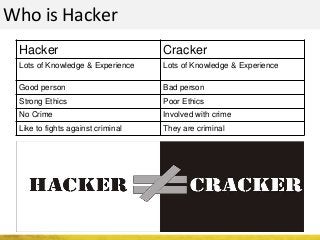
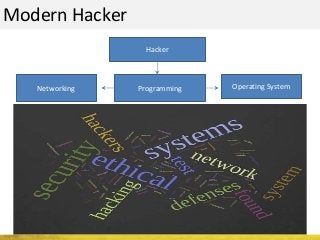
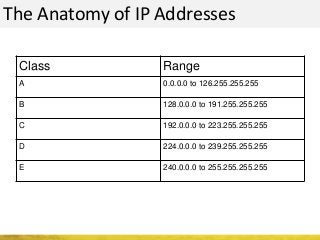
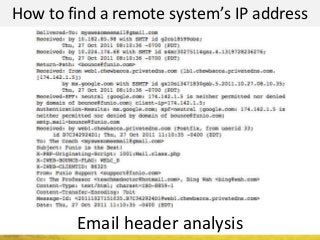
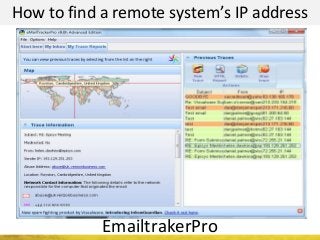
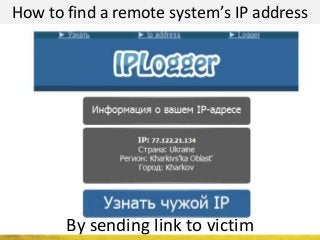
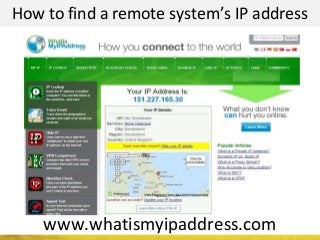
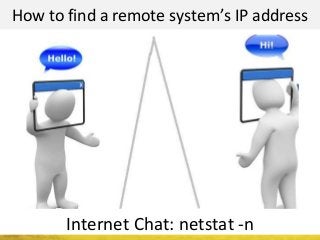
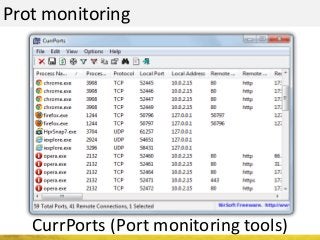
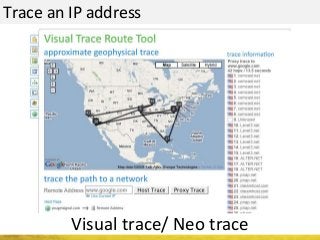
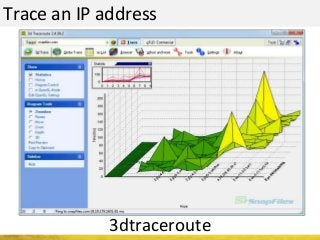
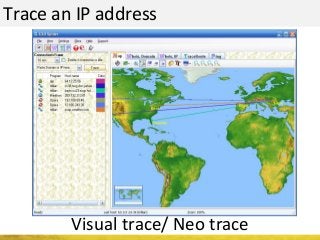
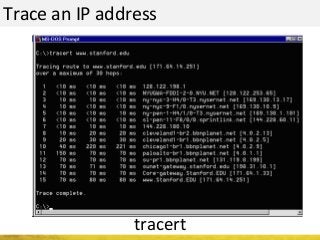
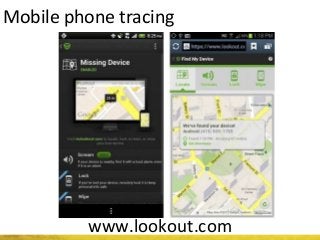
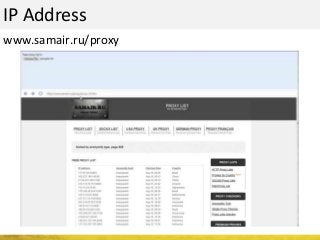
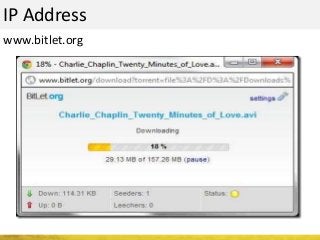
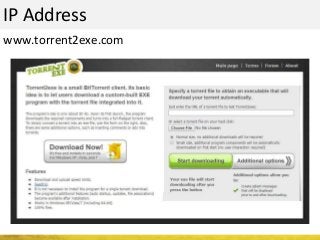
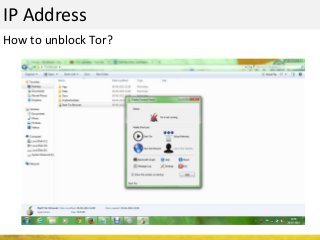
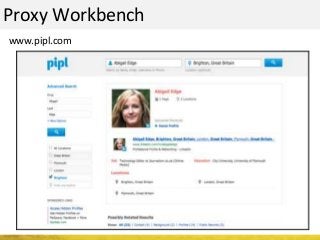
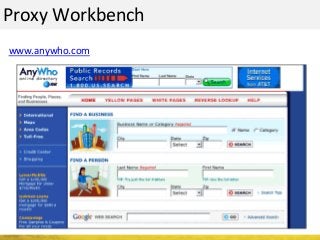
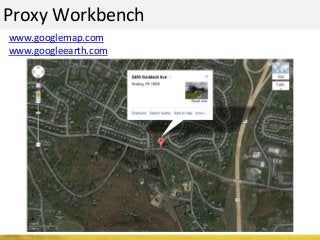
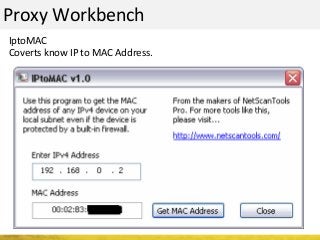
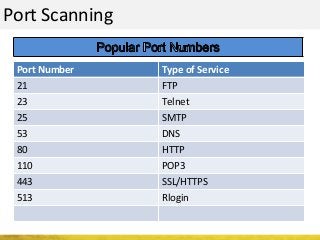
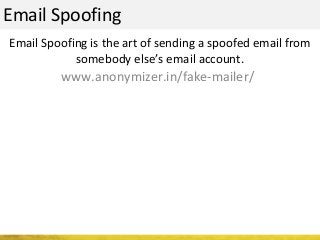
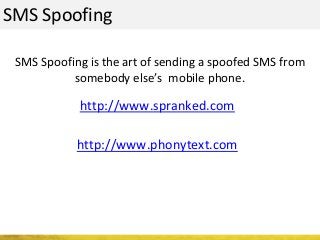
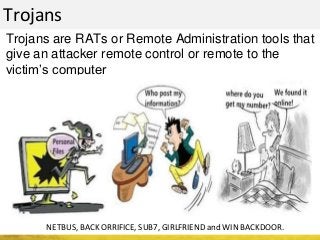
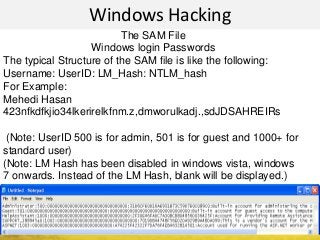
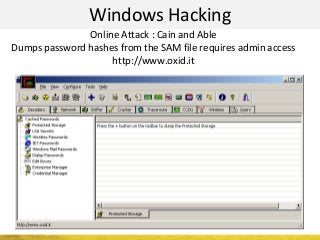
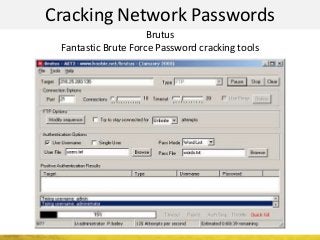
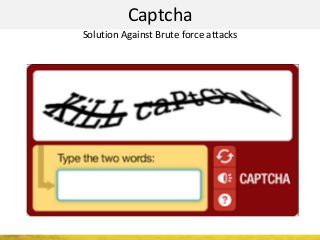
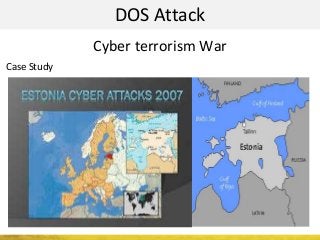
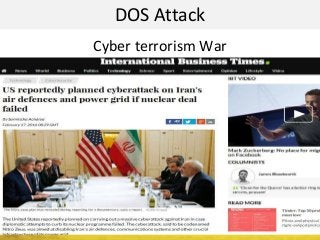
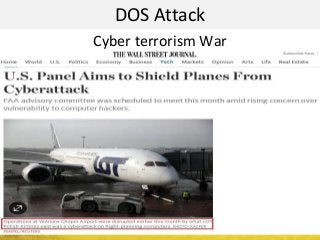
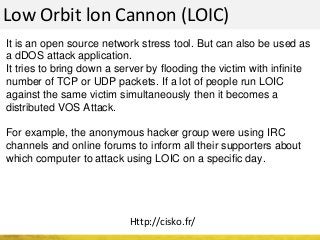
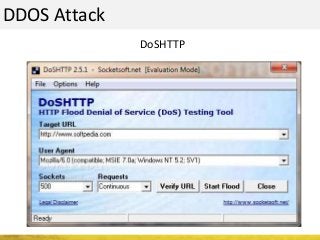
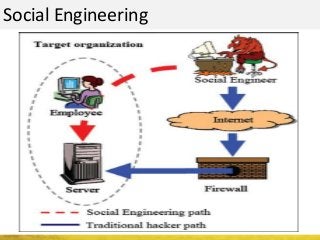
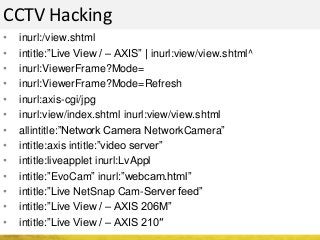
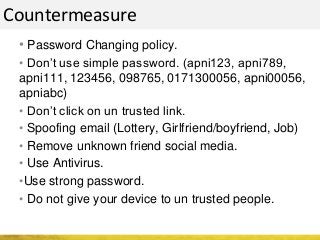
The document outlines a cyber security workshop led by Mehedi Hasan, covering topics such as cyber crime, hacking types, and information security measures. It discusses various cyber threats, including hacking techniques, malware, and social engineering, while also presenting case studies and countermeasures to combat these threats. The workshop aims to educate participants on thinking like a hacker to better defend against cyber criminals.