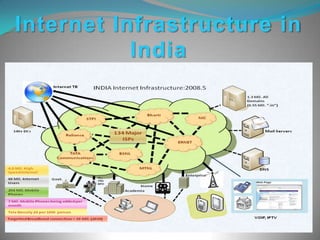
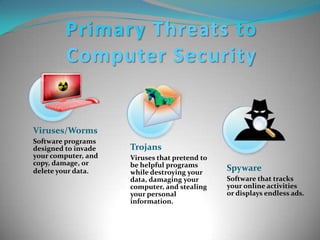
Cyber security expert Vivek Agarwal presented on cyber security. His presentation covered internet security, types of cyber crimes like hacking, child pornography, virus dissemination and cyber terrorism. It also discussed primary online risks like cyberbullies, predators, viruses and identity theft. The presentation provided steps individuals can take to boost cyber security such as using firewalls, automatic updates, antivirus and antispyware software. It emphasized educating families on internet safety and managing personal information.