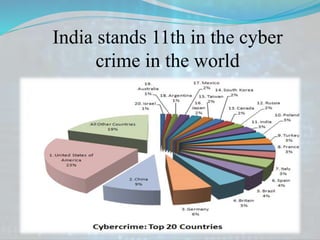
The document discusses the importance of cyber security in protecting online information amidst increasing internet connectivity and related threats. It outlines various security problems, including viruses, hacking, malware, and password cracking, and suggests preventive measures such as using security suites and strong passwords. Additionally, it highlights that cyber security is a collective responsibility, noting India's ranking in global cyber crime.